A sophisticated new cyberattack targeting Android devices in South Korea has been uncovered, leveraging Google’s asset-tracking feature, Find Hub, to remotely wipe sensitive user data.
Threat actors disguised as psychological counselors and North Korean human rights activists have distributed malware masquerading as stress-relief programs, marking a significant escalation in state-sponsored attacks linked to the notorious KONNI APT group.
The Genians Security Center (GSC) traces this campaign to the KONNI APT group, known for overlapping infrastructure and targets with Kimsuky and APT37 North Korean regime-linked actors previously classified by some as a single entity.
The Multilateral Sanctions Monitoring Team (MSMT), a UN-backed group, recently reaffirmed that KONNI and Kimsuky are separate but closely associated groups, both operating under the sanctioned 63 Research Center.
Notably, KONNI’s latest attack extends its operational reach by exploiting Android devices through Google’s Find Hub, a legitimate service designed to locate and secure lost phones.
For the first time, investigators have confirmed that state-linked threat actors compromised Google accounts, then abused Find Hub to track victims’ locations and invoke remote device wipes, erasing vital personal and work data.
Social Engineering and Initial Intrusion
Attackers initiated their campaign by impersonating trusted entities mental health professionals supporting North Korean defector youth and human rights activists to gain credibility.
The trust inherent in these relationships increased victims’ susceptibility, while the malware leveraged KakaoTalk’s PC sessions to propagate further among contacts.
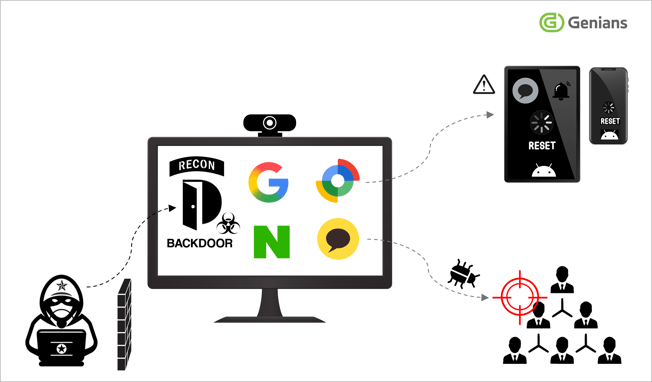
Upon infection, malicious scripts infected systems silently, establishing persistence and engaging in real-time reconnaissance.
The malware communicated with multiple command-and-control (C2) servers, allowing adversaries to install additional modules for ongoing surveillance, including webcam and audio monitoring especially effective against devices without physical activity indicators.

Spear-phishing tactics included sending emails purporting to be from the National Tax Service with embedded malicious files, or using KakaoTalk messenger to distribute “stress-relief” software.
Digital forensic analysis revealed that once initial access was achieved, attackers harvested credentials for Google and Naver accounts.
Afterward, the attacker opened Google’s Security menu, went to the Your devices section, and selected the Find My Phone link.


With this control, they logged into Google’s Security dashboard, targeted devices via Find Hub, and executed multiple remote reset commands.
These actions triggered factory resets, disabling communications and compounding the impact by cutting victims off from further notifications or alerts.
The compromised Google accounts were then used to distribute malware through KakaoTalk, amplifying reach and reinforcing attacks.

Not only was personal and sensitive data exfiltrated, but the incident also demonstrated an advanced combination of psychological manipulation and technical exploitation a hallmark of operationally mature APT strategies.
Malware Architecture
The malicious “Stress Clear.zip” archive contained an MSI package signed with a legitimate-seeming digital certificate, thus avoiding basic security scrutiny.
The ‘Stress Clear.msi’ file runs only on Windows operating systems and is not executable on non-compatible platforms such as smartphones, so those devices are not infection targets.
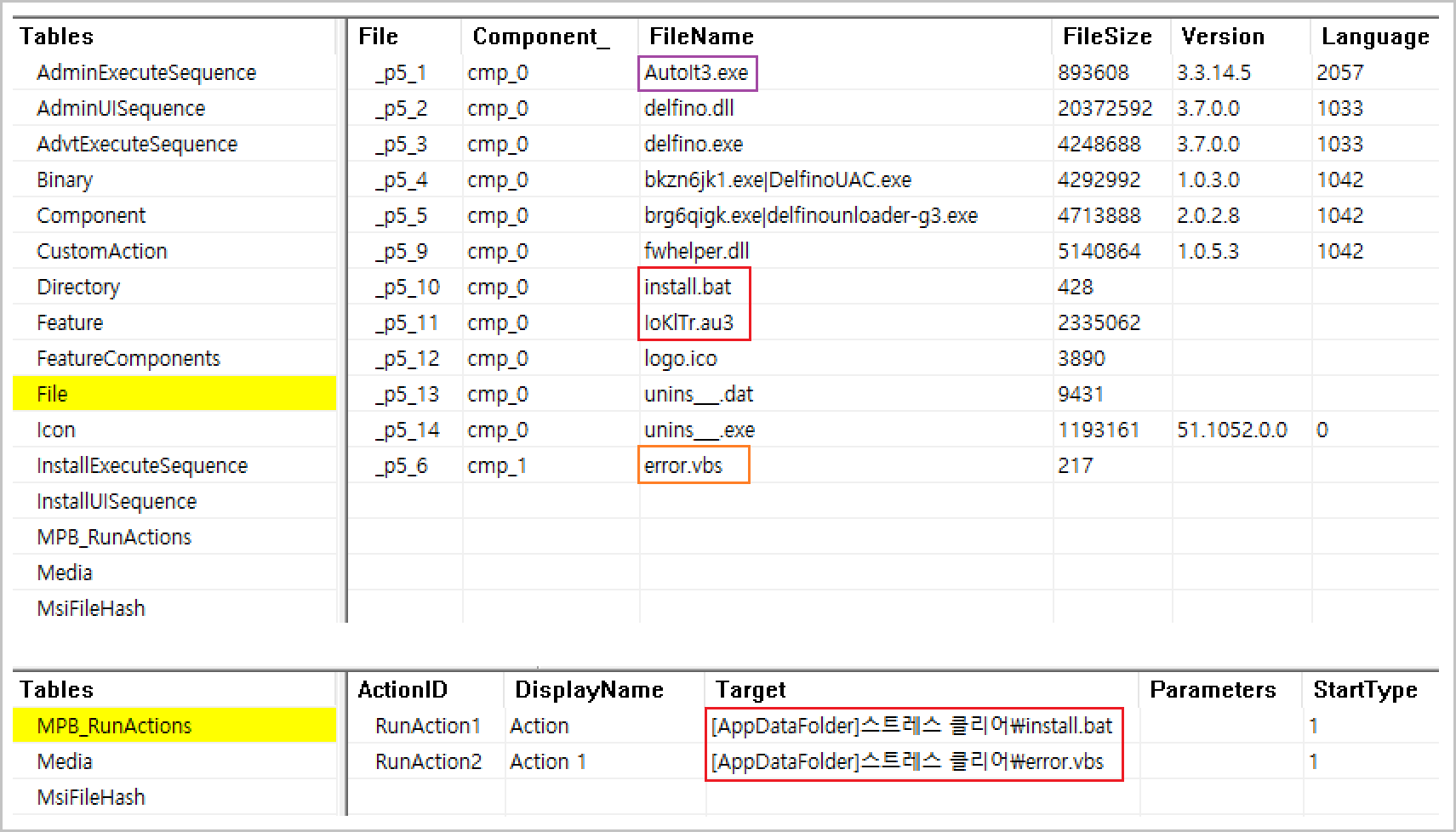

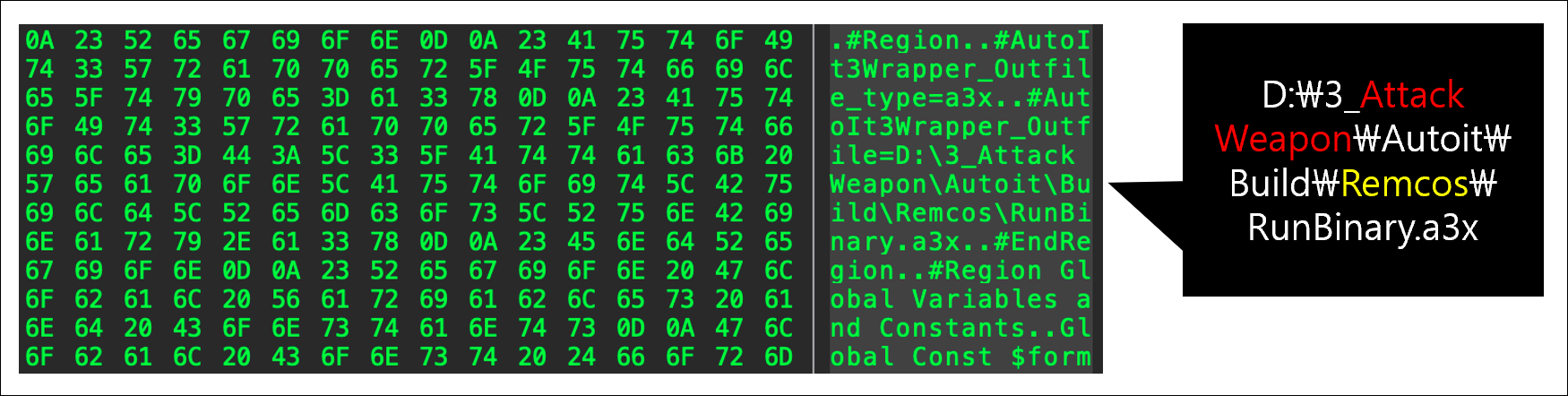
On execution, embedded batch files and AutoIt scripts established persistence, mapped scheduled tasks, and distributed additional modules such as RemcosRAT, QuasarRAT, and RftRAT.
These allowed remote access, keylogging, and further exfiltration while evading traditional antivirus and network controls.

This wave of attacks signals the urgent need for robust security measures. Enterprises and individuals should:
- Harden account security by enabling two-factor authentication and regular password changes.
- Implement real-time behavior-based detection via modern EDR (Endpoint Detection and Response) solutions, tracking process activity, credential access, and communication with suspicious C2 sites.
- Monitor for IOCs linked to KONNI and related North Korean threat actors and deploy network segmentation and rapid containment policies.
Given the demonstrated ability of these actors to abuse legitimate platform features, such as Find Hub, coordinated efforts are required from service providers and users alike to verify remote wipe requests and enforce authenticated ownership, reducing opportunistic exploitation and cascading data loss.
The emergence of Android device remote-wipe malware, skillfully masked as mental health tools, reveals the continually evolving strategies of state-linked cyber adversaries and highlights the necessity of proactive, intelligence-driven defense.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.