The Androxgh0st botnet has significantly expanded its operations since 2023, with cybercriminals now compromising prestigious academic institutions to host their command and control infrastructure.
This sophisticated malware campaign has demonstrated remarkable persistence and evolution, targeting a diverse range of vulnerabilities across web applications, frameworks, and Internet of Things devices to establish widespread network access.
The botnet’s operators have shown particular cunning in their selection of hosting infrastructure, preferring to embed their malicious operations within legitimate, trusted domains.
.png
)
This strategic approach not only provides operational cover but also exploits the inherent trust associated with educational and institutional websites.
The choice to target academic institutions reflects a calculated decision to leverage domains that typically receive less scrutiny from security monitoring systems and maintain high reputation scores with security vendors.
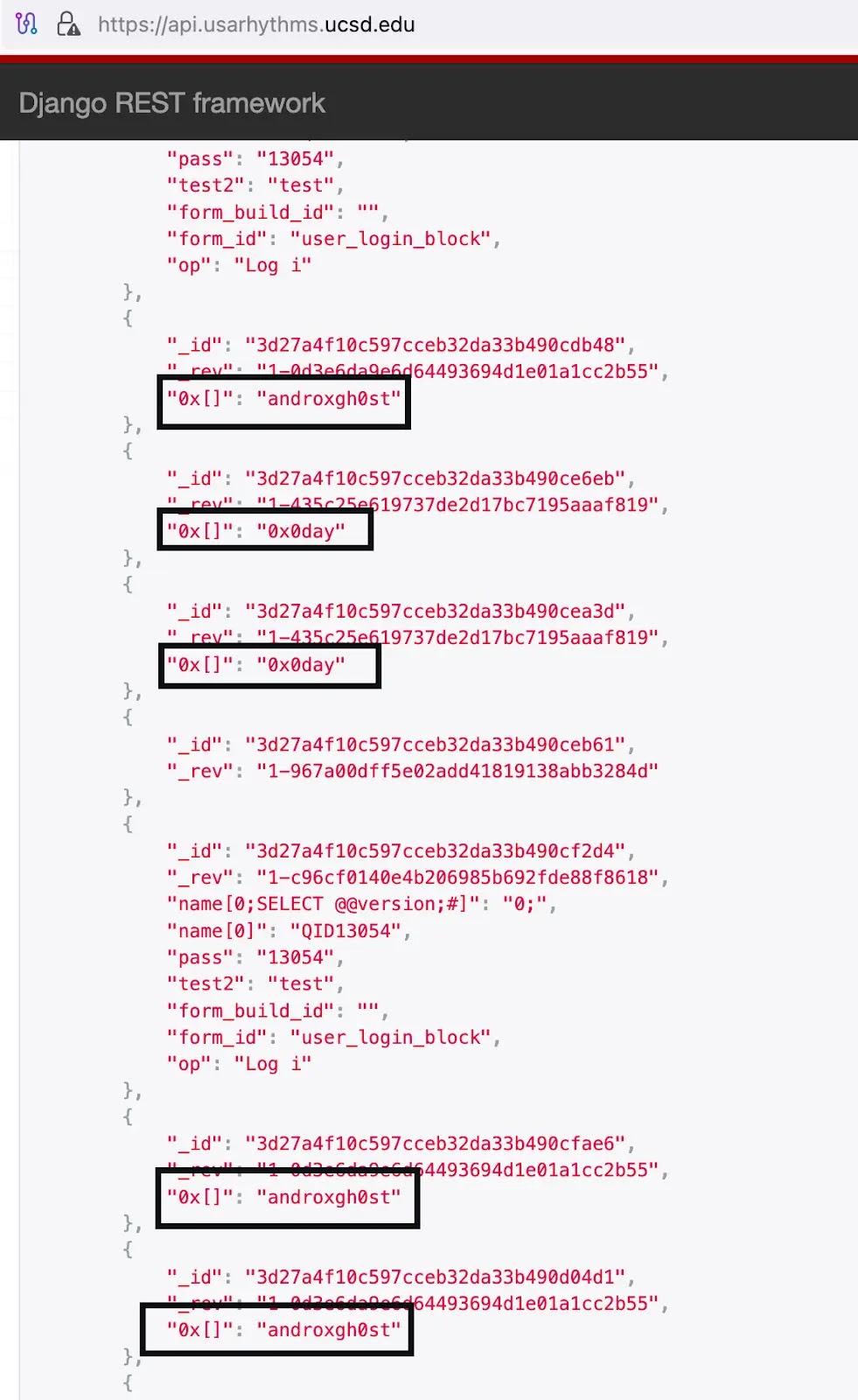
CloudSEK analysts identified that the Androxgh0st operators successfully compromised a University of California, San Diego subdomain, specifically “api.usarhythms.ucsd.edu,” to host their command and control logger.
.webp)
This particular subdomain appears to be associated with the USA Basketball Men’s U19 National Team portal, demonstrating how attackers exploit legitimate but potentially under-monitored institutional web properties.
The compromise represents a significant escalation in the botnet’s sophistication and operational security measures.
The malware’s attack methodology encompasses exploitation of over twenty distinct vulnerabilities, marking a fifty percent increase in initial access vectors compared to previous campaigns.
These vulnerabilities span multiple technology stacks including Apache Shiro JNDI injection flaws, Spring Framework remote code execution vulnerabilities (Spring4Shell), WordPress plugin weaknesses, and Internet of Things device command injection vulnerabilities.
The diversity of attack vectors ensures broad target coverage and maximizes the likelihood of successful system compromise across different organizational environments.
Webshell Deployment and Persistence Mechanisms
The Androxgh0st operators deploy a sophisticated arsenal of four distinct webshells designed for persistent access and continued exploitation of compromised systems.
The primary webshell, “abuok.php,” employs hexadecimal encoding combined with PHP’s eval function to execute obfuscated payloads.
The malicious code utilizes eval(hex2bin()) to decode and execute embedded commands, while wrapping the payload in seemingly innocuous text strings to evade basic detection mechanisms.
error_reporting(0); eval(hex2bin("636c617373204e7b707..."));The “myabu.php” variant demonstrates additional evasion techniques through ROT13 encoding, where str_rot13("riny") produces “eval” to execute arbitrary code submitted via POST requests.
This encoding method provides a simple yet effective obfuscation layer that bypasses signature-based detection systems while maintaining full remote code execution capabilities.
The webshells collectively enable file upload functionality, code injection capabilities, and persistent backdoor access, ensuring that even if primary infection vectors are patched, the attackers maintain multiple pathways for continued system access and exploitation.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
