Multiple bugs affecting millions of vehicles from 16 different manufacturers could be abused to unlock, start, and track cars, plus impact the privacy of car owners.
The security vulnerabilities were found in the automotive APIs powering Acura, BMW, Ferrari, Ford, Genesis, Honda, Hyundai, Infiniti, Jaguar, Kia, Land Rover, Mercedes-Benz, Nissan, Porsche, Rolls Royce, Toyota as well as in software from Reviver, SiriusXM, and Spireon.
The flaws run a wide gamut, ranging from those that give access to internal company systems and user information to weaknesses that would allow an attacker to remotely send commands to achieve code execution.
The research builds on earlier findings from late last year, when Yuga Labs researcher Sam Curry et al detailed security flaws in a connected vehicle service provided by SiriusXM that could potentially put cars at risk of remote attacks.
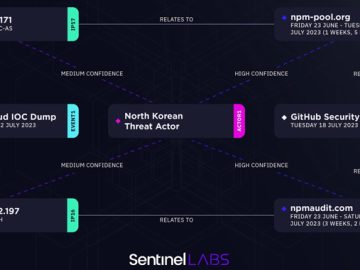
The most serious of the issues, which concern Spireon’s telematics solution, could have been exploited to gain full administrative access, enabling an adversary to issue arbitrary commands to about 15.5 million vehicles as well as update device firmware.
“This would’ve allowed us to track and shut off starters for police, ambulances, and law enforcement vehicles for a number of different large cities and dispatch commands to those vehicles,” the researchers said.
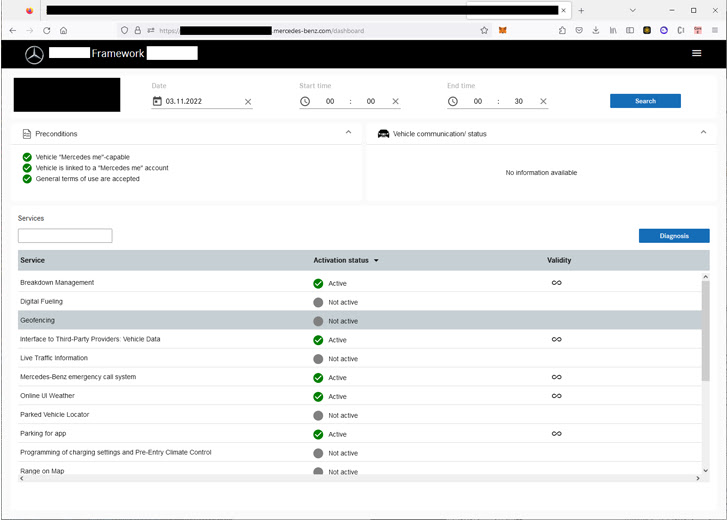
Vulnerabilities identified in Mercedes-Benz could grant access to internal applications via an improperly configured single sign-on (SSO) authentication scheme, while others could permit user account takeover and disclosure of sensitive information.
Other flaws make it possible to access or modify customer records, internal dealer portals, track vehicle GPS locations in real time, manage the license plate data for all Reviver customers, and even update vehicle status as “stolen.”
While all the security vulnerabilities have since been fixed by the respective manufacturers following responsible disclosure, the findings highlight the need for defense-in-depth strategy to contain threats and mitigate risk.
“If an attacker were able to find vulnerabilities in the API endpoints that vehicle telematics systems used, they could honk the horn, flash the lights, remotely track, lock/unlock, and start/stop vehicles, completely remotely,” the researchers noted.
//e&&!t&&(jQuery.ajax({url:”https://thehackernews.com/feeds/posts/default?alt=json&max-results=4″,type:”get”,cache:!1,dataType:”jsonp”,success:function(e){for(var t=””,s=””,r=0;r<e.feed.entry.length;r++){for(var a,l=0;l<e.feed.entry[r].link.length;l++)if("alternate"==e.feed.entry[r].link[l].rel){t=e.feed.entry[r].link[l].href;break}100<(a=(a="content"in e.feed.entry[r]?e.feed.entry[r].content.$t:"summary"in e.feed.entry[r]?e.feed.entry[r].summary.$t:"").replace(/]*>/g,””)).length&&(a=a.substring(0,90));var n=(n=e.feed.entry[r].title.$t).substring(0,58),o=(o=e.feed.entry[r].media$thumbnail.url.replace(//s72-c-e100/,”/s260-rj-e365″));s+=’
“}s+=””,document.getElementById(“result”).innerHTML=s}}),t=!0)})});
//]]>