Security researchers at Apiiro have released two free, open-source tools designed to detect and block malicious code before they are added to software projects to curb supply chain attacks.
The two tools consist of a comprehensive ruleset for Semgrep and Opengrep designed to detect malicious code patterns with minimal false positives and PRevent, a GitHub-integrated scanner, that detects and alerts on suspicious code in pull requests (PRs).
According to Apiiro’s security researcher Matan Giladi, the tools have a minimal false positive detection rate, making them particularly valuable in real-world practice.
Specifically, the detection accuracy of the ruleset for PyPI packages is 94.3%, while it drops to the still impressive 88.4% for npm packages. PRevent successfully flags malicious PRs in 91.5% of the examined cases.
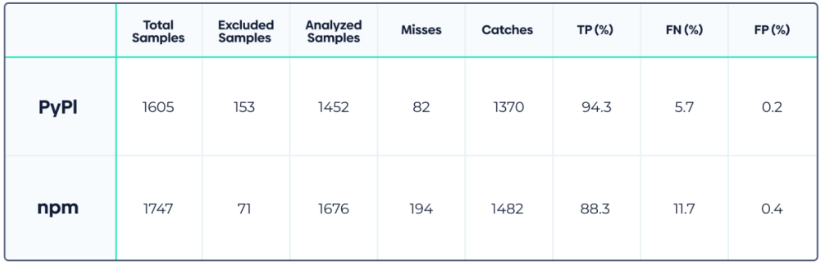
Source: Apiiro
Catching malicious code
Apiiro’s malicious code detection strategy is based on identifying “code anti-patterns,” which are suspicious patterns in code that demonstrate behaviors that are rare in legitimate code but common in malware.
The detection system uses static analysis, meaning it examines code without executing it, keeping the environment safe from accidental infections.
These anti-patterns include:
- Various obfuscation methods like encoding, nested transformations, and runtime modifications that help hide the code’s functionality and intent.
- Use of exec(), eval(), or similar functions, which allow arbitrary code execution at runtime.
- Code that downloads and executes remote payloads from external, unknown servers.
- Methods for exfiltrating sensitive user data to external locations.
This ruleset can be integrated into CI/CD pipelines for automatic repository scanning, used for scanning npm and PyPI packages, or adapted to other platforms using Semgrep or Opengrep.
PRevent, which uses the same anti-patterns, is designed to scan pull request events in real-time before code is merged, stopping any threats before they reach production.
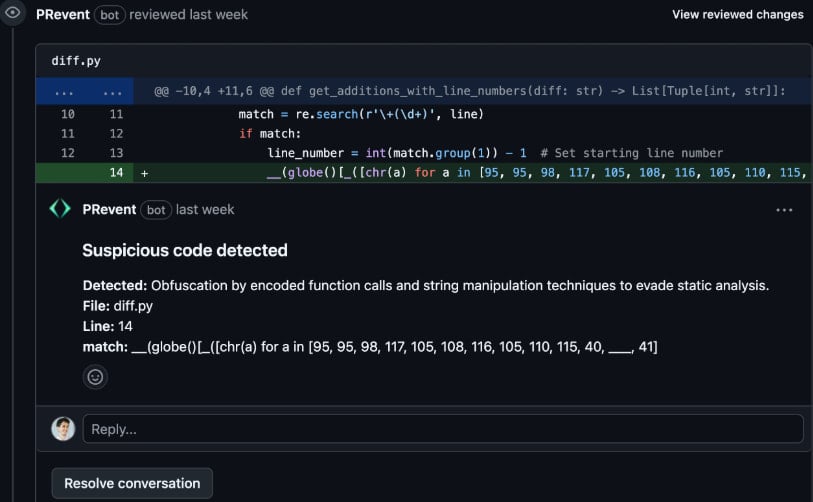
Source: Apiiro
It can be set to block the merging until an authorized reviewer approves it or add comments on detected issues to ensure developers are alerted of the risks.
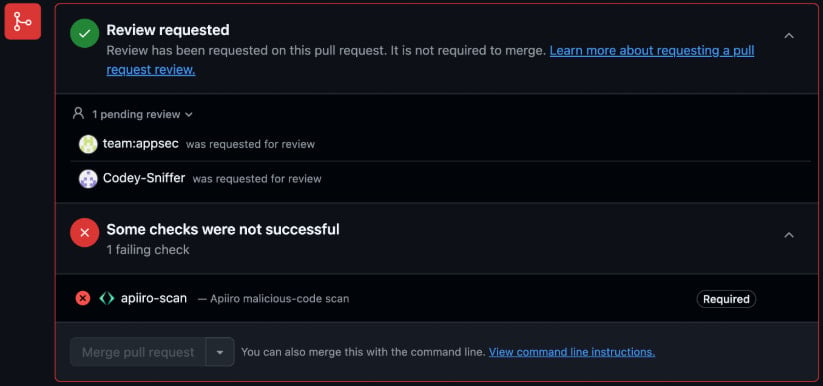
Source: Apiiro
Apiiro acknowledges that its tools are still practically limited, as they cannot detect malware hidden in compiled binaries nor scan npm and PyPI packages directly, but plans to add more features like deep code analysis and AI-assisted scans in future updates.
Both the malicious code detection ruleset and the PRevent tool are available for free on GitHub, with instructions on how to use them.
BleepingComputer has not tested these security tools and cannot guarantee their effectiveness or safety.
