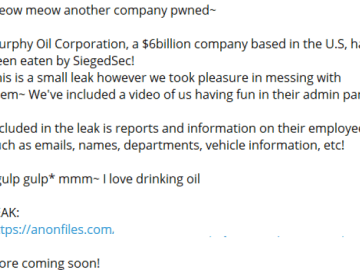
Apple is fixing multiple new vulnerabilities in its products.
According to the latest Rapid Security Response announcement, Apple has taken decisive action to fix a critical zero-day vulnerability, CVE-2023-37450. This vulnerability has been actively exploited and could lead to arbitrary code execution.
The CVE-2023-37450 vulnerability exists in WebKit, the browser engine used by Apple’s Safari and other web browsers on iOS and iPadOS.
The exploitation of this vulnerability can be triggered by processing specially crafted malicious web content, potentially leading to arbitrary code execution. An anonymous security researcher reported the issue, which has been addressed through improved checks.
However, Apple’s commitment to Rapid Security Response patches for user security also presents certain limitations. The company’s stringent upgrade policies restrict users from uninstalling full system updates, even if they encounter genuine issues.
This approach prevents downgrades that could reintroduce old bugs exploited for jailbreaking or installing alternative operating systems.
Apple Security Response patches: Does it help?
The Silicon Valley tech giant has implemented the Rapid Security Response system to address these Apple vulnerabilities.
This system focuses on a subset of software components that are commonly targeted by cybercriminals for launching cyber attacks, particularly Safari and other web browsing elements. By prioritizing these components, Apple aims to patch vulnerabilities quickly and efficiently.
Rapid Security Response updates are available for macOS Ventura 13.4.1, iOS 16.5.1, and iPadOS 16.5.1. After applying the rapid patch, the versions will display 13.4.1 (a) and 16.5.1 (a), respectively.
In the case of older supported versions of macOS Big Sur and macOS Monterey, a traditional system update is available solely for patching Safari, resulting in Safari version 16.5.2.
While these updates cater to the latest Apple platforms, it’s important to note that as of now (as of July 10, 2023), there are no updates available for other Apple systems, including iOS 15, older iPhones and iPads, Apple Watches, and TVs.
It remains possible that these platforms are also affected by the vulnerability mentioned above. Users are advised to monitor Apple’s general Security Portal and the new Rapid Security Response page to stay informed about updates for other Apple systems.
Apple’s Rapid Security Response: A new way of dealing with vulnerabilities
It’s worth mentioning that Apple introduced the Rapid Security Response updates in May 2023. These updates serve as crucial security enhancements between regular software updates, focusing on components such as Safari, the WebKit framework stack, and critical system libraries.
In addition to providing faster mitigation for security issues, including those that have been actively exploited or reported, these rapid patches can be uninstalled by users if necessary, differentiating them from regular security updates.
Apple’s Rapid Security Response updates have set a benchmark in the industry for their speed and wide-scale deployment across millions of devices. By enabling automatic updates, Apple ensures that most customers receive these security updates seamlessly.
Debrup Ghosh, Senior Product Manager at Synopsys Software Integrity Group, highlights the significance of Apple’s swift response, emphasizing the importance of addressing vulnerabilities promptly and efficiently.
While every effort is made to eliminate vulnerabilities during development and testing, they can occasionally slip through the cracks.
However, the critical factor lies in an organization’s ability to quickly fix and remediate these vulnerabilities, preventing or mitigating active exploits. Apple’s Rapid Security Updates demonstrate an effective and efficient approach toward achieving this goal.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.