Since Apple removed the popular “right-click and open” Gatekeeper override in August 2024, threat actors have shifted their tactics to deliver malware on macOS.
Among emerging techniques, attackers are increasingly leveraging AppleScript (.scpt) files to bypass security controls and distribute credential stealers often disguised as legitimate software updates from popular applications such as Zoom and Microsoft Teams.
Apple’s removal of the Gatekeeper override eliminated one of the most effective infection vectors for macOS malware.
In response, attackers adapted by developing alternative delivery methods, most of which required victims to interact with Terminal manually a significant hurdle for successful exploitation.
Now, threat actors have discovered a more deceptive workaround: weaponizing .scpt files to execute malicious payloads while maintaining plausible deniability.
How AppleScript Attacks Work
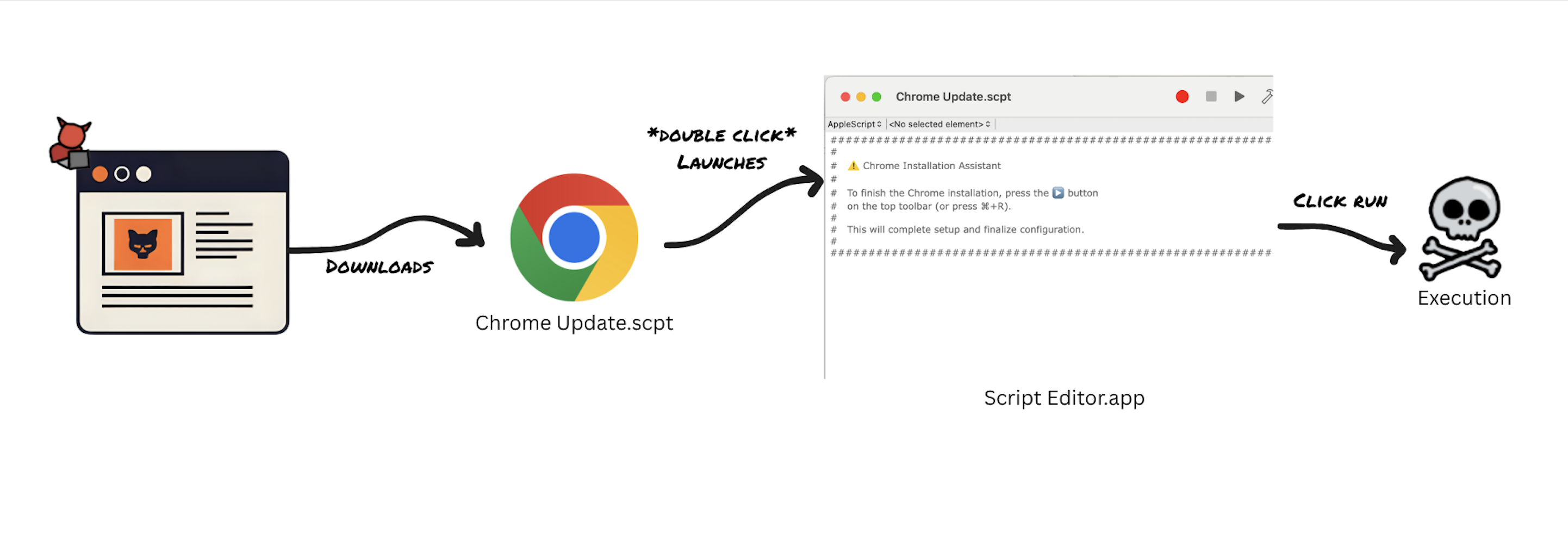
The attack chain is straightforward but effective. By default, .scpt files open in Script Editor when double-clicked. Attackers embed malicious commands within these scripts while using social engineering tricks to encourage execution.
Comments in the script persuade users to run it, often hiding actual malicious code behind numerous blank lines. When users click the Run button or press Command+R, the script executes immediately even if flagged by Gatekeeper as quarantined.
This method is particularly insidious because Script Editor is a legitimate macOS application, making the attack less suspicious than traditional malware delivery mechanisms.
Security researchers have identified .scpt files being used to create convincing fake documents and application installers.
What began as an advanced threat actor technique has now been adopted by commodity malware families, including Odyssey Stealer and MacSync Stealer. This “trickle-down” of APT tactics suggests the technique has matured into a widely-leveraged attack vector.
Threat actors have created fake .docx and .pptx files masquerading as legitimate documents financial proposals and investment agreements complete with custom icons that enhance their credibility.
Similarly, attackers have distributed fake update installers for Teams, Zoom, and other popular applications through sophisticated phishing websites designed to deceive macOS users.
Beyond disguising file names, attackers have enhanced the social engineering component by assigning custom icons to .scpt files.
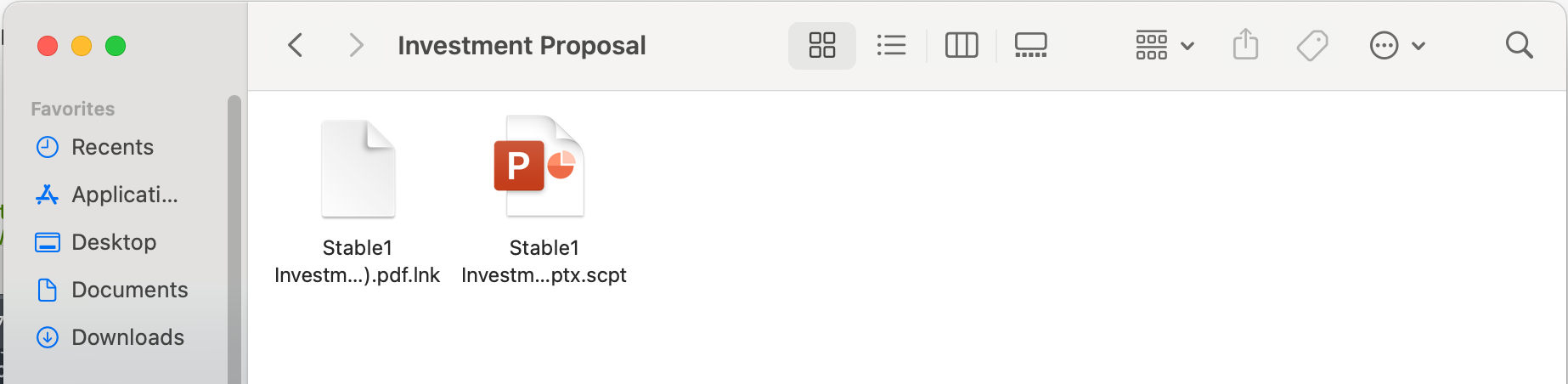

These icons are stored in the file’s resource fork and are preserved when files are delivered via ZIP or DMG archives. When users extract these files, they see convincing fake document or application icons rather than script indicators, significantly increasing the likelihood of execution.
Mitigations
VirusTotal analysis reveals that many of these malicious .scpt files have evaded detection entirely, with zero antivirus engine flagging them as malicious.
When this is unzipped on a Mac endpoint, the custom icon will be displayed, resulting in a convincing fake document.


Samples using this technique have been discovered disguised as Microsoft Teams SDK updates, Zoom SDK updates, and generic software packages, demonstrating the breadth of attack scenarios.
The emergence of AppleScript-based delivery represents a critical vulnerability in macOS security. Unlike Windows, where similar script-based attacks have been mitigated through changing default applications, macOS users lack straightforward defensive options.
Similar to zip files, dmg files also preserve the icons of the files. This is something that has become common samples we’ve seen for “Drag and drop to the terminal DMGs”.


Security teams can implement defensive measures by changing the default application for .scpt files away from Script Editor, similar to recommendations for .js and .vbs files on Windows.
Hunters can detect malicious scripts by searching for suspicious command patterns including obfuscated strings and event codes associated with shell script execution.
As attackers continue refining these techniques and adopting obfuscation strategies similar to PowerShell attacks, organizations must remain vigilant in monitoring for AppleScript-based threats targeting their macOS environments.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
