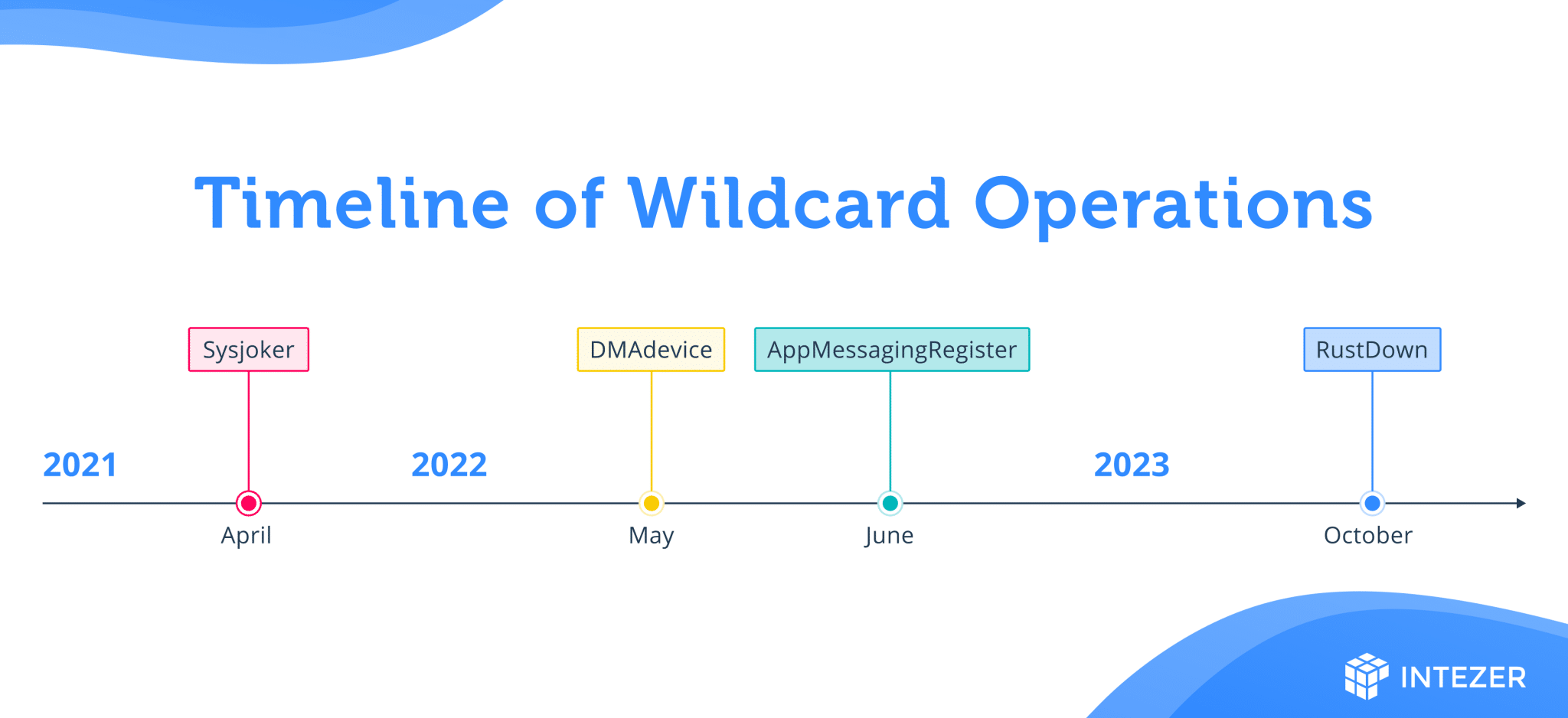
SysJoker malware was initially discovered to be used by the APT group dubbed “WildCard” and targeted Israel’s educational sector. However, the operations of this APT threat actor have expanded to include additional malware variants, with one of them found to be written in Rust programming language.
This new rust malware has been coined “Rustdown” by the malware developers. In addition to this, the threat actor has also shifted their focus to critical sectors within Israel, like education, IT infrastructure, and electric power generation.
In the upcoming webinar, Karthik Krishnamoorthy, CTO and Vivek Gopalan, VP of Products at Indusface demonstrate how APIs could be hacked. The session will cover: an exploit of OWASP API Top 10 vulnerability, a brute force account take-over (ATO) attack on API, a DDoS attack on an API, how a WAAP could bolster security over an API gateway
Technical Analysis
Two new malware variants have been discovered, which have evolved from the SysJoker malware. These variants were named DMADevice.exe and AppMessagingRegistrar.exe and were written in C++.
There were three samples of malware variants found in two of them DMADevice.exe and AppMessagingRegistrar.exe.
DMADevice
According to the samples analyzed, this malware had a code similar to SysJoker. Additionally, one unique string was identified to be exactly the same in the SysJoker malware.
It was the custom alphabet “0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghilmnopqrstuvmxyz” that was present in the code of both SysJoker and the DMA device malware variants. This string misses two characters, “jk”, the same on both samples.
AppMessagingRegistrar
This variant was identified to be compiled after the DMAdevice variant and also shares the same code as SysJoker. However, there are different capabilities, XOR keys, and URL paths on this malware. The URL paths used by this malware are,
- api/update
- /api/register
- /api/library
- /api/requests
This malware is downloaded from a ZIP file and executed by a DLL file masquerading as Brave browser. Furthermore, the use of Gdrive and OneDrive was similar on both DMAdevice and AppMessagingRegistrar variants of SysJoker malware.
RustDown: The new variant
As of October 2023, the APT group has been found to be relying on a different malware written in Rust, which was a 32-bit Windows executable that disguised itself as a PHP framework component.
The codebase of this malware was new but shared the same Tactics, Techniques, and Procedures of the WildCard APT group.
This malware implements multiple calls to the Sleep API with random time durations which was similar to the SysJoker malware. Additionally, it also copies the executable to another location using PowerShell for persistence.
A complete report about these new variants of SysJoker malware and the WildCard APT group has been published, which provides detailed information about the TTP, source code, hash values, and other information.
Indicators of Compromise
Rustdown
d4095f8b2fd0e6deb605baa1530c32336298afd026afc0f41030fa43371e3e72
DMAdevice (SysJoker May 2022 Variant)
e076e9893adb0c6d0c70cd7019a266d5fd02b429c01cfe51329b2318e9239836
6c8471e8c37e0a3d608184147f89d81d62f9442541a04d15d9ead0b3e0862d95
AppMessagingRegistrar (SysJoker June 2022 Variant)
67ddd2af9a8ca3f92bda17bd990e0f3c4ab1d9bea47333fe31205eede8ecc706
SysJoker Downloader
96dc31cf0f9e7e59b4e00627f9c7f7a8cac3b8f4338b27d713b0aaf6abacfe6f
Dead Drop Resolver URL
- https://onedrive.live[.]com/download?resid=16E2AEE4B7A8BBB1%21112&authkey=!AED7TeCJaC7JNVQ (RustDown)
- https://onedrive.live[.]com/download?cid=F6A7DCE38A4B8570&resid=F6A7DCE38A4B8570%21115&authkey=AKcf8zLcDneJZHw (DMAdevice.exe)
- https://onedrive[.]live.com/download?cid=3014636895E3FE3B&resid=3014636895E3FE3B%21106&authkey=AD4OGrVz9h17Jzo (AppMessagingRegistrar.exe)
C2
- 85.31.231[.]49:443 (Rustdown)
- sharing-u-file[.]com (DMAdevice.exe)
- audiosound-visual[.]com (AppMessagingRegistrar.exe)filestorage-short[.]org (SysJoker Downloader)
Experience how StorageGuard eliminates the security blind spots in your storage systems by trying a 14-day free trial.




