Iranian cyber unit Charming Kitten, officially designated APT35, has long been dismissed as a noisy but relatively unsophisticated threat actor a politically motivated collective known for recycled phishing templates and credential-harvesting pages.
Episode 4, the latest intelligence dump, fundamentally rewrites that assessment. What emerges is not a hacker collective but a government department, complete with expense reports, invoices, and procurement procedures that rival those of any legitimate enterprise.
The leaked files expose the bureaucratic machinery that sustains Iranian cyber operations: spreadsheets logging hosting providers and invoice numbers, cryptocurrency receipts processed through Cryptomus, and server rentals under a mosaic of false European identities.
These are not exploits they are administrative records. The dump illuminates how Tehran requisitions, funds, and maintains infrastructure, revealing the institutional metabolism that converts state intent into executable code.
The Three-File Architecture
The leaked dataset comprises three interconnected spreadsheets that function as an operational backbone.
The first, 0-SERVICE-Service.csv, contains roughly 170 rows tying domains to registrars, featuring more than 50 distinct ProtonMail identities and over 80 cleartext credential pairs.
Entries reference recurring providers: EDIS (VPS) appears approximately 20 times, NameSilo (domains) 14 times, and Impreza (VPS) 6 times. Line-item pricing spans dollars and euros, with lifecycle notes like “3 Months / #2016” and “SSL / no SSL.”
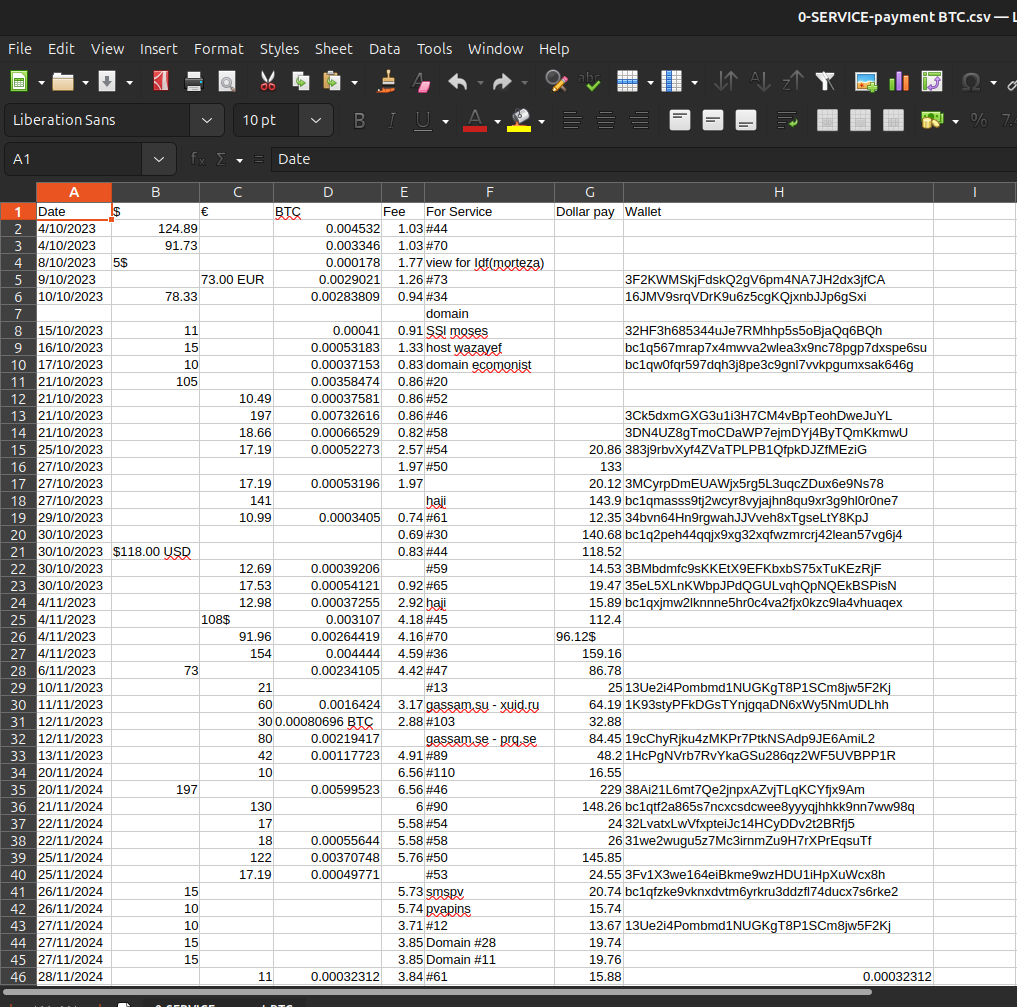
The second sheet, 0-SERVICE-payment BTC.csv, documents 55 cryptocurrency transactions spanning October 2023 through December 2024, totaling approximately $1,225 with average outlays of $56 per transaction.
At least 32 unique Bitcoin addresses populate the wallet field, many referencing internal service numbers that mirror entries in the service sheet. This creates a verifiable audit trail linking request, payment, and activation.
The third file, 1-NET-Sheet1.csv, closes the operational loop with network addresses: IP ranges and CIDR allocations with Persian-annotated connectivity notes and location markers.
These entries correspond to live infrastructure observed in provider dashboards, matching the same pseudonymous customer identities and service SKUs from the invoices.
The leaked materials reveal a striking operational pattern. APT35 operates not through improvisation but through a standardized workflow. Domain registration, VPS procurement, credential logging, and payment reconciliation follow a consistent procedural choreography.
Across multiple aliases and time periods, the same hosting tiers, vendors, price bands, and cryptocurrency payment rails recur with precision.
This consistency demonstrates an industrialized process engineered for resilience and administrative continuity rather than sophistication.
Perhaps most damaging, post-breach APT35 failed to execute basic operational security. Compromised infrastructure remained accessible for weeks, with live servers, hosting credentials, and payment gateway access left unprotected.
This gap between bureaucratic precision and OPSEC failures underscores a paradox central to Charming Kitten’s operations: meticulous administration coupled with operational carelessness.
The Moses Staff Connection
Buried within the service ledger sits a revelatory entry: moses-staff[.]io. This discovery addressed that APT35 operated the infrastructure supporting Moses Staff, the group ostensibly portrayed as an ideological hacktivist collective targeting Israeli organizations.
By breaching cloud providers and IT service firms like UST Global Israel, Moses Staff extends reach laterally, turning trusted intermediaries into unwitting vectors.
The overlapping ProtonMail accounts, registrars, and payment infrastructure reveal that Moses Staff’s seemingly independent ransomware campaigns were in fact products of APT35’s procurement workflow different “projects” assigned internal ticket numbers within the same bureaucratic regime.
The Episode 4 files expose how Tehran’s cyber operations function as a subscription service. Small cryptocurrency micropayments, fragmented across dozens of wallets and routed through Cyprus-based resellers, maintain persistent infrastructure while evading compliance detection.
This approach mirrors Iran’s broader experience with sanctions evasion: breaking expenditures into small, dispersed transactions to frustrate financial tracking and maintain operational continuity.
What these artifacts ultimately demonstrate is that state-sponsored cyber power rests not on technological innovation but on institutional persistence.
Behind every exploited system sits a purchase order; behind every campaign sits an accounts-payable clerk. The spreadsheet, not the malware, is what keeps Iranian cyber operations operational.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
