The notorious Chinese-speaking cyberespionage group APT41 has expanded its operations into new territories, launching sophisticated attacks against government IT services across Africa using advanced Windows administration modules.
This represents a significant geographical expansion for the group, which has previously concentrated its efforts on organizations across 42 countries in various sectors including telecommunications, energy, healthcare, and education.
In a recently documented incident, the threat actors demonstrated their evolving tactics by leveraging the Atexec and WmiExec modules from the Impacket penetration testing toolkit to establish persistence and conduct lateral movement within compromised networks.
The attack showcased APT41’s ability to adapt their methodologies to specific target environments while maintaining their characteristic stealth and persistence.
The campaign’s sophistication became apparent through the attackers’ use of hardcoded internal service names, IP addresses, and proxy server configurations embedded directly within their malware.
Most notably, the group compromised and weaponized a SharePoint server within the victim’s own infrastructure to serve as a command and control (C2) center, demonstrating their capability to turn organizational assets against their owners.
Securelist analysts identified the threat actor through distinctive tactical patterns and infrastructure similarities with previous APT41 campaigns.
The researchers noted that Africa had previously experienced minimal activity from this particular advanced persistent threat group, making this incident particularly significant for understanding the group’s expanding global reach.
.webp)
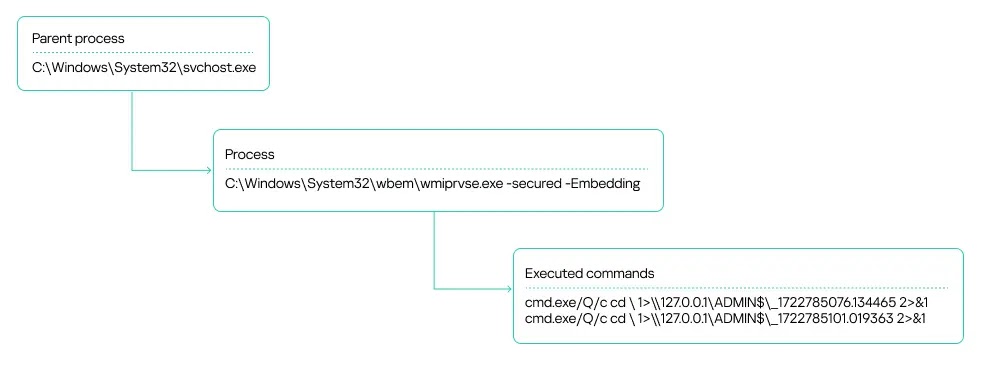
The attack’s initial detection came through monitoring systems that identified suspicious WmiExec activity, characterized by a distinctive process chain pattern of svchost.exe → exe → cmd.exe.
This execution flow served as a key indicator of the attackers’ presence and provided security teams with early warning signs of the compromise.
Lateral Movement and Privilege Escalation Tactics
The attackers’ lateral movement strategy revealed sophisticated understanding of Windows environments and administrative protocols.
.webp)
Following their initial compromise, APT41 operators conducted extensive reconnaissance using built-in Windows utilities to map the target network and identify security solutions.
Their reconnaissance phase included systematic enumeration commands such as cmd.exe /c netstat -ano > C:Windowstemptemp_log.log and cmd.exe /c tasklist /v > C:Windowstemptemp_log.log, which provided comprehensive network and process visibility.
The group then escalated privileges by harvesting credentials from critical registry hives using commands like cmd.exe /c reg save HKLMSAM C:Windowstemptemp_3.log and cmd.exe /c reg save HKLMSYSTEM C:Windowstemptemp_4.log.
The attackers exploited compromised domain accounts with administrative privileges to distribute their toolkit across multiple hosts via SMB protocol, placing malicious files in strategic locations including C:WindowsTasks and C:ProgramData directories.
This methodical approach enabled them to establish persistent access while maintaining operational security throughout their campaign.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now




