A group from China attacked a media organization in Taiwan, which is not yet known, and used Google’s platform to spread a red team tool called Google Command and Control (GC2) as a final payload.
While it’s part of their wider efforts to carry out harmful and malicious actions using Google’s resources.
The Threat Analysis Group (TAG) of Google recently identified a campaign that a group of hackers carried out called HOODOO. At the same time, this group is known by various names based on geography and location, which is being monitored by the TAG.
Here below, we have mentioned all the other names of “HOODOO”:-

- APT41
- Barium
- Bronze Atlas
- Wicked Panda
- Winnti
Strategic Perspective — Government-Backed Hackers Likely to Look to Criminals for Inspiration Targeting Cloud
Usually, we imagine military and espionage technology becoming available to the public after some time in a process called “spin-off.”
It involves making futuristic gadgets, like fighter jets and spy gear, available for public use and commercialization.
In some cases, it has been observed that organized crime groups are the first to adopt military or espionage technology.
They frequently have an advantage over their targets, who still use outdated technology from past conflicts. This, as a result, is a mismatch in defense that could lead to increased vulnerability for the targeted group.
With technology being a crucial part of military conflict and intelligence competition, state-sponsored cyber attackers constantly seek ways to build their arsenal.
By adapting the tools from threat actors, they do so using the following elements:-
- Published vulnerability research
- Adding exploits used in the wild
- In-house custom-made tools were developed
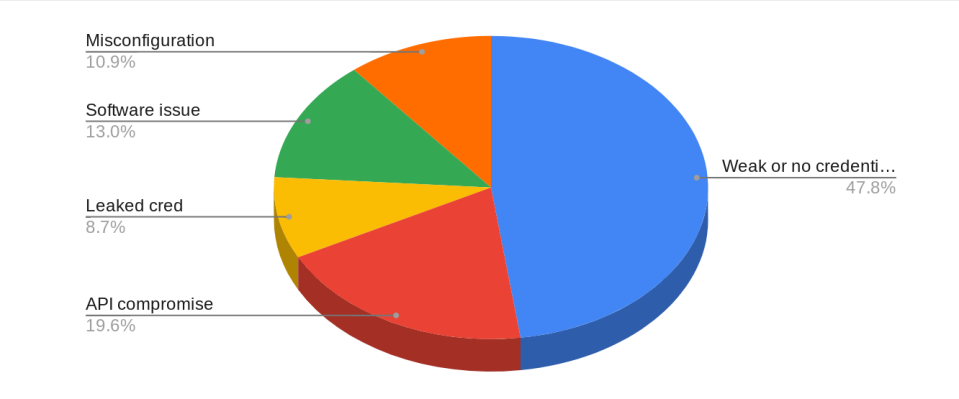
Credentials and API Issues Continue to Lead to Compromise Factors
Due to the weak passwords, it was observed during the fourth quarter of 2022 that almost half of the security breaches and incidents were caused.
Not only that but even in the past three months, this trend has remained apparent. API compromise remained a significant factor in nearly 20% of incidents in the third quarter, maintaining its trend.
However, there was some positive news, with a slight decrease in misconfiguration and software issues. The increased use of leaked credentials partly offset the decrease.
Threat actors still prioritize using credential-based access, a significant concern for 2023. In short, organizations should make it their top priority to address this issue on an immediate basis to prevent further exploitation.
HOODOO Uses Public Tooling, Google Workspace to Target Taiwanese Media
HOODOO (aka APT41), a Chinese-backed threat group, targeted a Taiwanese media organization in October 2022. While targeting the media company, they sent phishing emails containing links to password-protected files, and all the files sent were found to be hosted in Drive.
However, at the time, Google’s Threat Analysis Group (TAG) was able to disrupt the campaign.
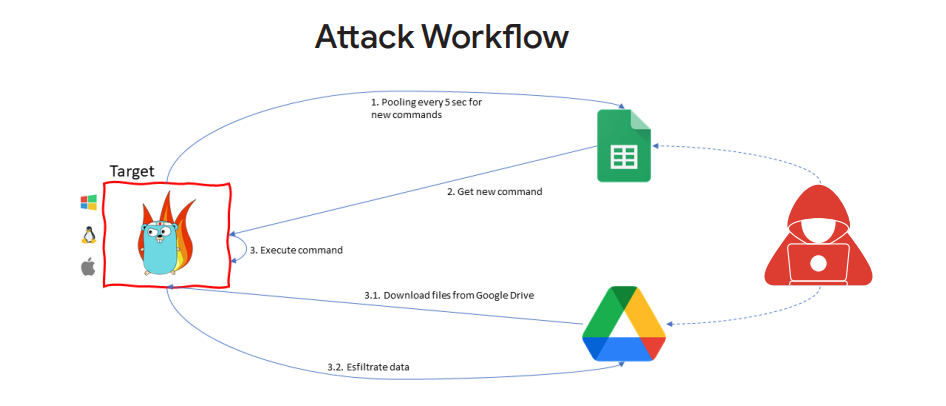
The payload used in the HOODOO attack on a Taiwanese media organization was a Go-written open-source red teaming tool named “Google Command and Control” (GC2).
Here, the tool uses the Google Sheets commands after installation on the victim machine to extract data into Google Drive, which is done to hide malicious activity.
As a result of these incidents, a few key trends about the threats posed by cybercriminals affiliated with China have been identified.
Compromised Customer Websites Hosted on IT Service Providers’ Infrastructure
Google found 14 customer websites in Feb 2023 on their cloud hosting platform that were hacked and communicating with malware.
Cybersecurity analysts at Google discovered this by using 2022 VirusTotal data. IT Service Providers (ITSP) were responsible for setting up all the sites for 14 clients who had purchased GC services from the ITSPs.
There are a few things that customers of Google Cloud ITSP and even ITSPs can do to prevent such misuse of their environments:-
- Ensure that clients are appropriately segregated.
- An individual administrator’s ability to access all clients must be limited.
- Monitor and analyze endpoint servers to determine if they have been compromised and take appropriate action.
- Make sure to patch vulnerabilities found using vulnerability scans immediately.
- ITSPS must ensure the ability to access resources based on their roles.
- In resold assets, ITSPs should provide guidance to clients regarding the secure configuration of websites, web applications, and domain names.
- Ensure that tenants are isolated from one another.
Cloud-Hosted Encrypted ZIP Files Evading Detection
Google Cybersecurity Action Team (GCAT) and Mandiant investigated the use of Google Drive for malware hosting by threat actors.
They discovered that in an attempt to avoid detection, the malware was being stored in encrypted ZIP files on Google Drive.
In Q4 2022, threat actors utilized DICELOADER malware to expand on this technique. DICELOADER is a versatile type of malware that threat actors can use for various illicit purposes or malicious activities.
Threat actors using cloud services to host malicious content pose a risk as they continue to develop evasive and stealthy techniques to avoid detection.
They have moved from using encrypted ZIP files containing malware to using encrypted ZIP files that link to trojanized legitimate installers.
All these stealthy techniques are concerning and emphasize the importance of maintaining strong cybersecurity measures.
Customer Challenges and Solutions When Security Patching Google Kubernetes Engine
The availability, flexibility, and security provided by Kubernetes clusters have resulted in an increasing number of cloud customers running their workloads on them.
Kubernetes clusters require regular patching to maintain their features and ensure the installation of security fixes.
GKE users can ensure their workloads remain available and up-to-date with security patches by setting up and managing Kubernetes environments. This enables a faster patching process without disrupting the ongoing business operations.
In 2021-22, GKE teams spoke with customers and discovered that most delayed or prolonged security patching to balance security and availability concerns are:-
- It has been a concern for some customers to update their applications when unexpected patches can break the “state” of those applications.
- During the patching process, some of the team worried that not-yet-completed workloads would have to be restarted during the installation, which might disrupt work like machine learning “training”.
- Customers were concerned that security upgrades might also result in unanticipated changes to APIs, so they delayed upgrading.
- It is possible that patching will take longer for customers with large node fleets, and a weak security posture may be maintained longer.
The low-hanging fruit: leaked service account keys and the impact on your organization
One of the leading causes of abuse on Google Cloud continues to be the leakage or inadvertent sharing of service account credentials.
According to Google’s abuse systems, 42% of leaked critical incidents occurred because customers failed to take action after being contacted by Google, leaving the keys vulnerable or exposed.
The following points need to be taken into account by organizations seeking to reduce or mitigate the risks they face:-
- Proper management.
- Principle of least privilege with scoped IAM policies.
- Ensure the implementation of restricted policies and controls.
- Make sure to continue scanning and monitoring exposed keys.
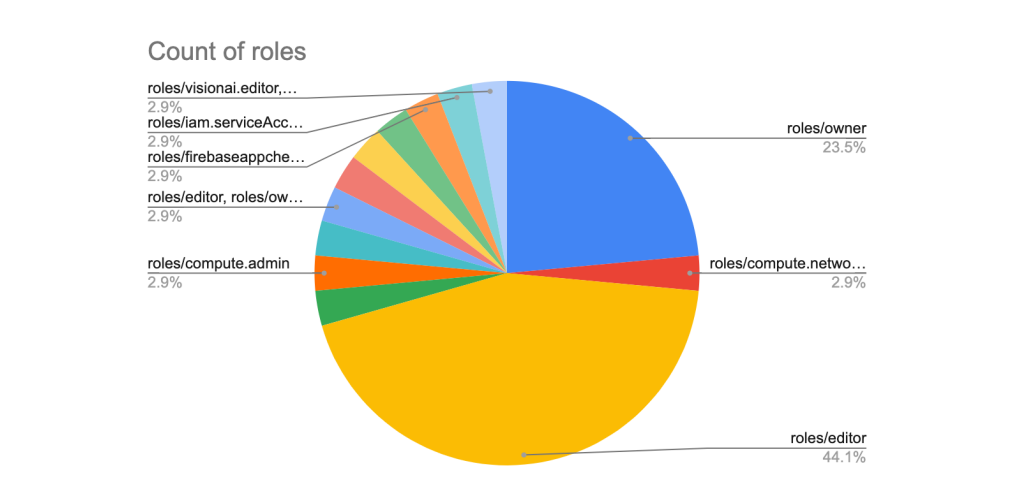
The top 5 most used policies on AWS and Azure were AdminstratorAccess and Owner, respectively, mirroring what Google Cloud’s Fraud and Abuse teams have found with IAM role assignments.
Organizations face significant risks and potential consequences when service account keys and other persistent credentials are leaked, making it essential to secure such sensitive information.
Mitigations
Here below, we have mentioned all the recommended mitigations:-
- Follow best practices when setting up Service Accounts and assess their need.
- The inventory should be kept, and the user should be audited regularly.
- If keys are exposed, have a plan and test your assumptions after discovering them.
- Utilize the IAM recommender, enforce organizational policies, and scope IAM permissions.
- Ensure that keys are not checked in and monitor for keys that have been exposed.
