An advanced persistent threat (APT) group with ties to Hamas has intensified its espionage operations against government and diplomatic entities across the Middle East, deploying a sophisticated new malware suite dubbed AshTag.
The threat actor, tracked as Ashen Lepus (also known as WIRTE), has demonstrated significant operational evolution while maintaining persistent activity throughout regional conflicts, including the Israel-Hamas war and beyond the October 2025 Gaza ceasefire.
Ashen Lepus, active since 2018, has traditionally targeted entities in close geographic proximity, such as the Palestinian Authority, Egypt, and Jordan.
Recent intelligence indicates a substantial expansion of the group’s operational scope, with attacks now reaching Arabic-speaking nations including Oman and Morocco.
This broader targeting demonstrates the threat actor’s growing ambitions and capabilities in regional cyber-espionage operations.
The campaign reveals a tangible evolution in Ashen Lepus’s operational security and tactics.
While previous operations demonstrated only moderate sophistication, the group has recently adopted more advanced techniques including enhanced custom payload encryption, infrastructure obfuscation using legitimate subdomains, and in-memory execution to minimize forensic artifacts.
These improvements represent a strategic shift toward better operational security and evasion capabilities.
The AshTag Malware Suite
AshTag represents a significant upgrade from the group’s traditional tooling. The modular .NET backdoor is designed for stealthy persistence and remote command execution, masquerading as a legitimate VisualServer utility to avoid detection.
The malware suite features extensive capabilities including file exfiltration, content download, and in-memory execution of additional modules.
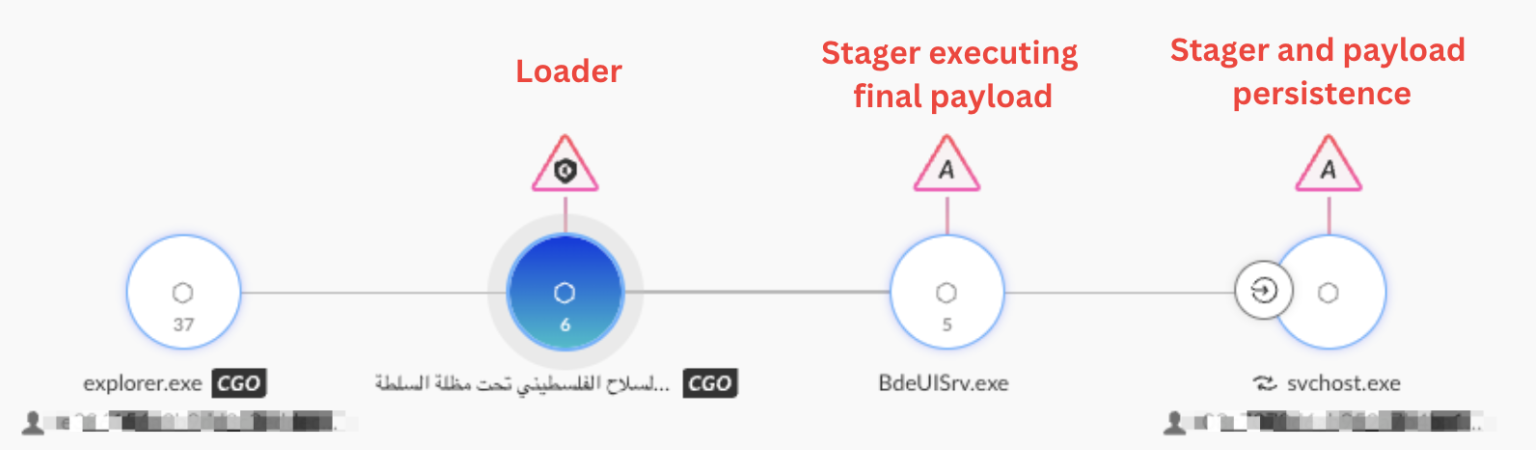
The infection chain begins with a benign PDF decoy file that guides targets to download a RAR archive containing malicious payloads.
When victims execute the binary file expecting to open a document, it side-loads a malicious DLL called AshenLoader in the background.
This loader retrieves and executes AshenStager, which then deploys the full AshTag payload while establishing persistence through scheduled tasks.
A notable development in this campaign is the group’s updated command and control (C2) infrastructure.
Instead of hosting C2 servers on their own domains, Ashen Lepus now registers API and authentication-related subdomains of legitimate domains such as api[.]healthylifefeed[.]com and auth[.]onlinefieldtech[.]com.
This approach helps malicious activity blend with benign network traffic and complicates detection efforts.
The group implements several cautionary measures including embedding secondary payloads within HTML tags of seemingly benign webpages, geofencing servers to prevent automated analysis, and checking specific User-Agent strings unique to the malware.
The modular architecture includes separate modules for persistence, screen capture, file management, and system fingerprinting, though analysis reveals specific components remain in active development.
Hands-On Data Theft Operations
Following automated infection, Ashen Lepus conducts hands-on data theft by accessing compromised systems to stage specific documents.
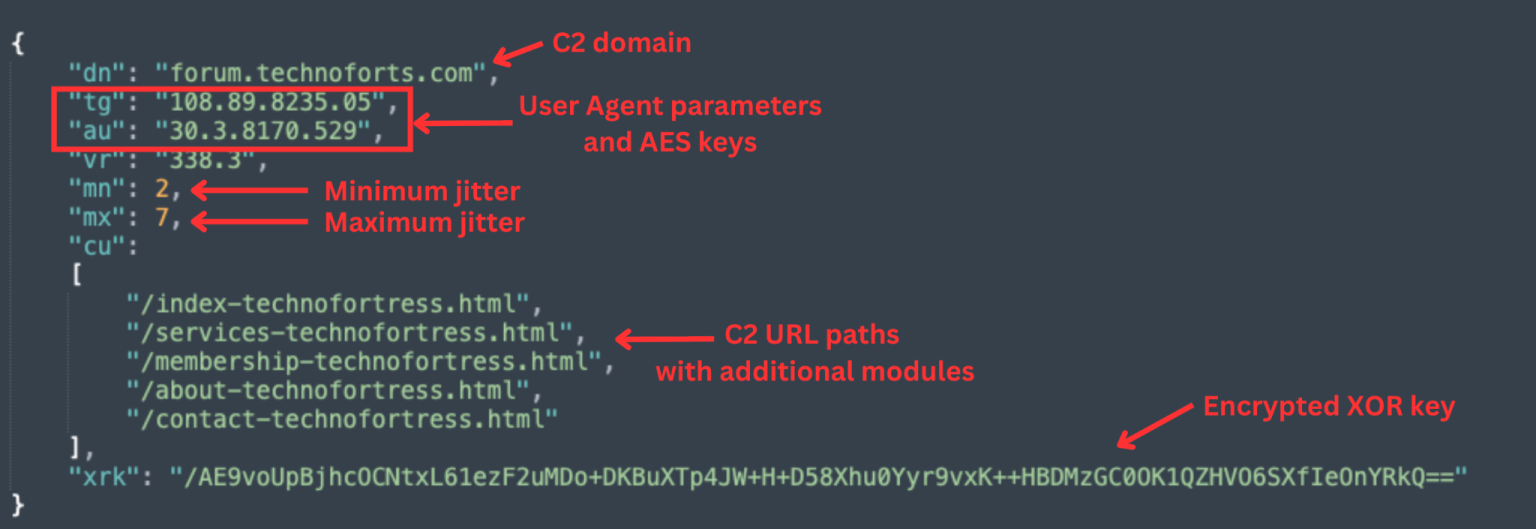
When AshenStager retrieves AshenOrchestrator’s payload, the stager receives a Base64-encoded JSON file. The JSON file contains the payload and the payload’s configuration.
Threat actors have been observed downloading documents directly from victim mail accounts, revealing their primary objective of obtaining diplomacy-related intelligence.
For exfiltration, the group leverages Rclone, an open-source file transfer tool, marking the first observed use of this legitimate utility by Ashen Lepus to blend malicious activity with normal network traffic.
Palo Alto Networks customers receive enhanced protection through Advanced WildFire, Advanced URL Filtering, Advanced DNS Security, Cortex XDR, and XSIAM products.
Ashen Lepus distinguishes itself from affiliated groups by maintaining persistent activity throughout the Israel-Hamas conflict period when other threat actors decreased operations.
The group continued deploying newly developed malware variants even after the October 2025 Gaza ceasefire, demonstrating clear commitment to continuous intelligence collection aligned with geopolitical objectives.
The majority of lure themes relate to Middle East geopolitical affairs, particularly those involving the Palestinian Territories, with recent campaigns showing increased focus on Turkey and its relationship with Palestinian administration.
Lure documents include themes such as partnership agreements between Morocco and Turkey, Hamas training reports, and proposals for unifying Palestinian arms.
Organizations in the Middle East, particularly governmental and diplomatic sectors, should remain vigilant against this evolving threat.
The company has updated its machine-learning models and analysis techniques to identify domains and URLs associated with this activity as malicious.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
