Malware analyst discovered a new version of the Atomic macOS info-stealer (also known as ‘AMOS’) that comes with a backdoor, to attackers persistent access to compromised systems.
The new component allows executing arbitrary remote commands, it survives reboots, and permits maintaining control over infected hosts indefinitely.
MacPaw’s cybersecurity division Moonlock analyzed the backdoor in Atomic malware after a tip from independent researcher g0njxa, a close observer of infostealer activity.
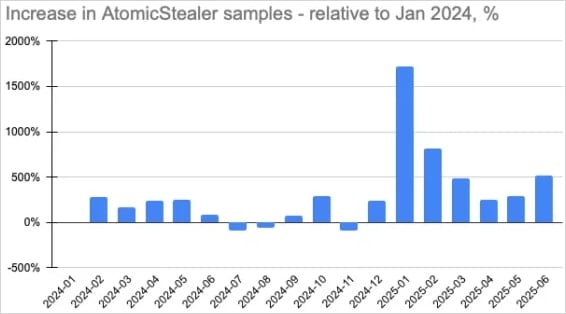
“AMOS malware campaigns have already reached over 120 countries, with the United States, France, Italy, the United Kingdom, and Canada among the most affected,” the researchers say.
“The backdoored version of Atomic macOS Stealer now has the potential to gain full access to thousands of Mac devices worldwide.”
Source: Moonlock
Evolution of the Atomic stealer
The Atomic stealer, first documented in April 2023, is a malware-as-a-service (MaaS) operation promoted on Telegram channels for a hefty subscription of $1,000 per month. It targets macOS files, cryptocurrency extensions, and user passwords stored on web browsers.
In November 2023, it supported the first-ever expansion of ‘ClearFake’ campaigns onto macOS, while in September 2024, it was spotted in a large-scale campaign by the cybercrime group’ Marko Polo,’ who deployed it on Apple computers.
Moonlock reports that Atomic has recently shifted from broad distribution channels like cracked software sites, to targeted phishing aimed at cryptocurrency owners, as well as job interview invitations to freelancers.
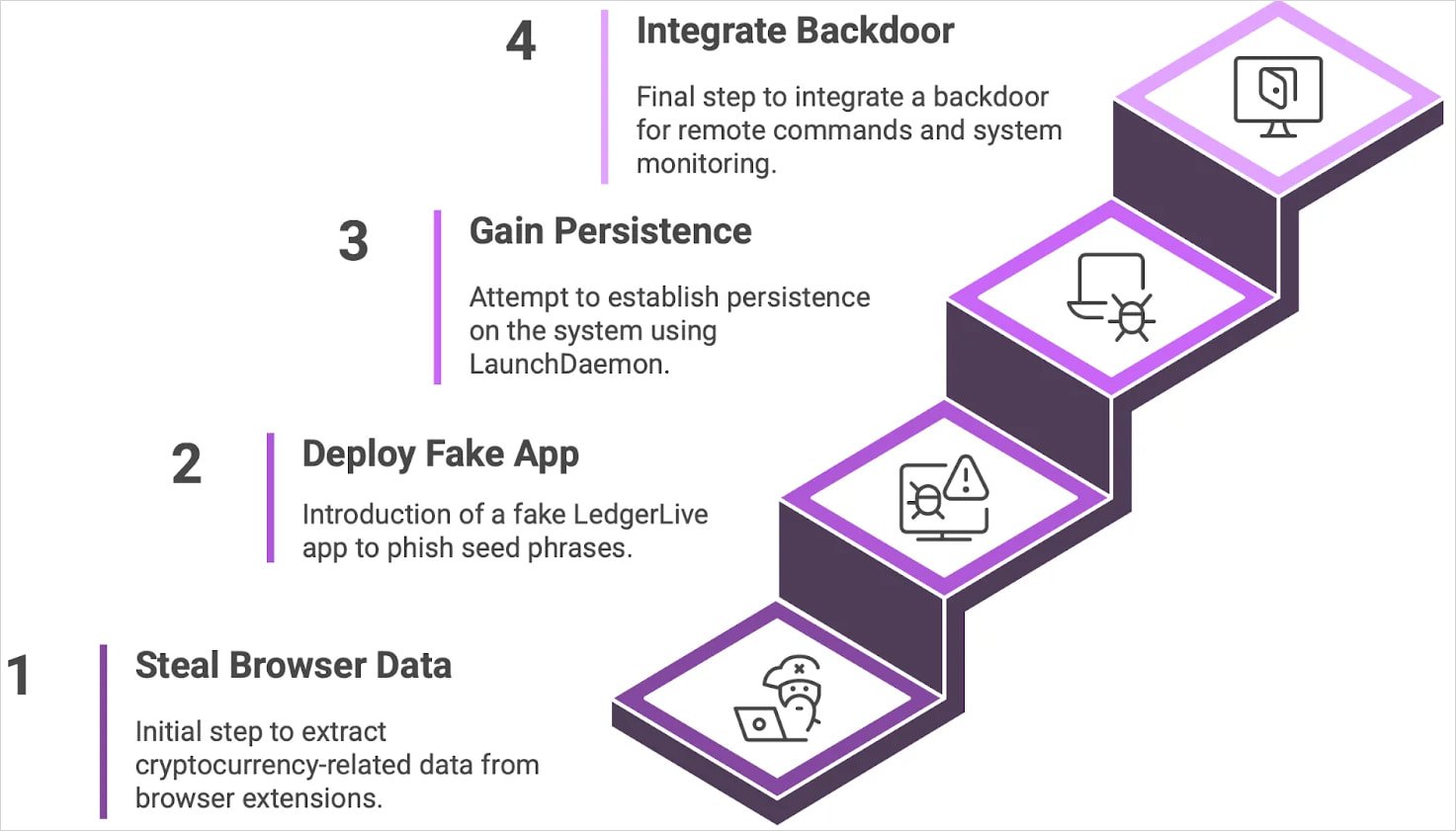
The analyzed version of the malware comes with an embedded backdoor, uses of LaunchDaemons to survive reboots on macOS, ID-based victim tracking, and new command-and-control infrastructure.
Source: Moonlock
A backdoor into your Mac
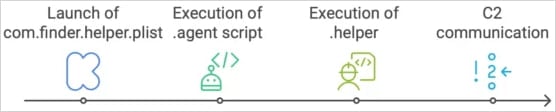
The core backdoor executable is a binary named ‘.helper,’ downloaded and saved in the victim’s home directory as a hidden file post-infection, the researchers say.
A persistent wrapper script named ‘.agent’ (also hidden) runs ‘.helper’ in a loop as the logged-in user, while a LaunchDaemon (com.finder.helper) installed via AppleScript ensures that ‘.agent’ executes at system startup.
This action is performed with elevated privileges using the user’s password stolen during the initial infection phase under a false pretext. The malware can then execute commands and change ownership of the LaunchDaemon PLIST to ‘root:wheel’ (superuser level on macOS).
Source: Moonlock
The backdoor allows the threat actors to execute commands remotely, log key strokes, introduce additional payloads, or explore lateral movement potential.
To evade detection, the backdoor checks for sandbox or virtual machine environments using ‘system_profiler’ and also features string obfuscation.
The evolution of Atomic malware shows that macOS users are becoming more attractive targets and malicious campaigns aimed at them are increasingly sophisticated.

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz’s detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.
