Author: Cybernoz
It is estimated that one third to a half of North Korea’s budget comes from cyberfraud and extortion. Finextra reports that most…
In this Help Net Security video, Gal Livschitz, Senior Penetration Tester at Terra Security, explains how phishing has evolved and…
Google has weighed in on a court case that will decide the future of a powerful but contentious tool for…
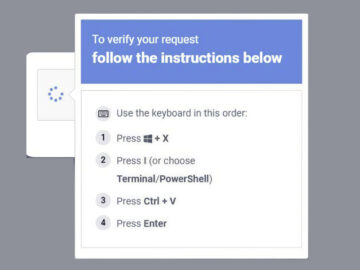
Ravie LakshmananMar 06, 2026Endpoint Security / Browser Security Microsoft on Thursday disclosed details of a new widespread ClickFix social engineering…
Sweden’s central bank has advised citizens to keep SEK1,000 (£81) in cash at home as part of its emergency plans…
The Middle East has entered a critical tipping point, as tensions between Iran, the United States, and Israel escalated into…
An international law enforcement operation has dismantled LeakBase, a major online marketplace for stolen data that had become a central…
Hollard Insurance Australia has started introducing AI into its business to speed up claim management in a bid to make…
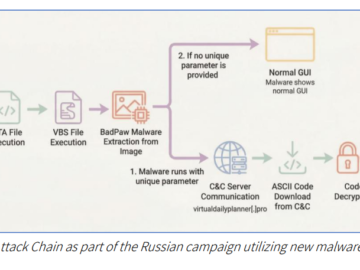
Russian APT targets Ukraine with BadPaw and MeowMeow malware Pierluigi Paganini March 05, 2026 Researchers uncovered a Russian campaign targeting…
Listen to the article 4 min This audio is auto-generated. Please let us know if you have feedback. The confirmation…
The Department of Health and Human Services unveiled a tool Thursday to help health care facilities assess their cybersecurity risks,…
The education sector is notoriously short on cash, but rich in assets for threat actors to target. How can managed…