Author: Cybernoz
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) have released four new Industrial Control Systems (ICS) advisories. These advisories expose…
U.S. CISA adds Apple iOS, iPadOS, and macOS flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini August 22, 2025 U.S….
Separating truth from fiction is the first step towards making better parenting decisions. Let’s puncture some of the most common…
Artificial intelligence systems can automatically generate functional exploits for newly published Common Vulnerabilities and Exposures (CVEs) in just 10-15 minutes…
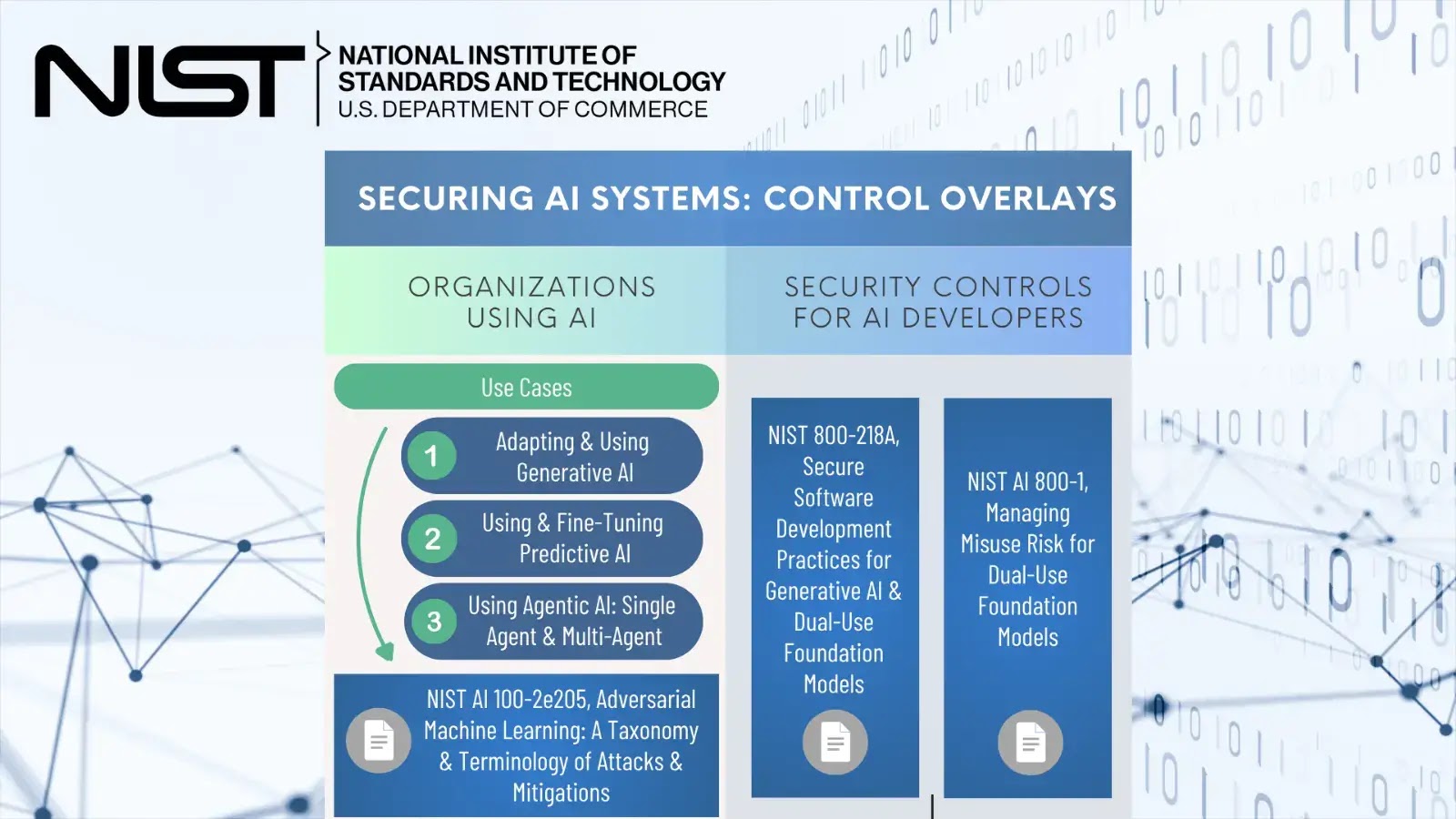
The National Institute of Standards and Technology (NIST) has unveiled a comprehensive initiative to address the growing cybersecurity challenges associated…
Aug 22, 2025Ravie LakshmananCybercrime / Malware A 55-year-old Chinese national has been sentenced to four years in prison and three…
A critical security vulnerability has been discovered in the widely-used sha.js npm package, exposing millions of applications to sophisticated hash…
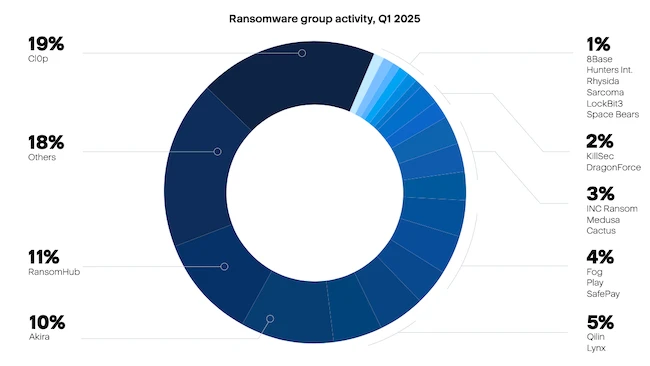
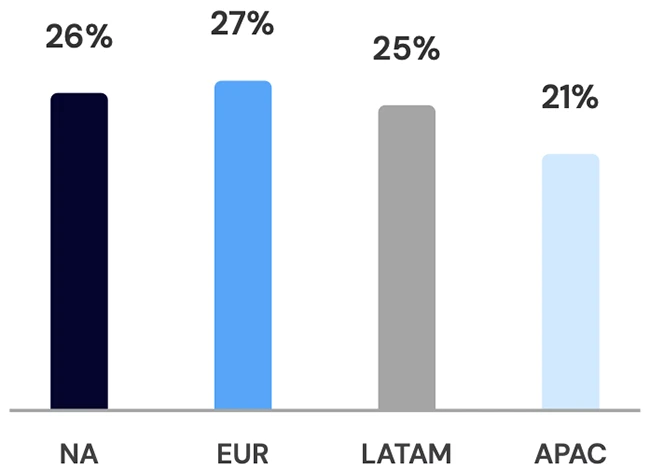
Ransomware continues to be the major threat to large and medium-sized businesses, with numerous ransomware gangs abusing AI for automation,…
A critical vulnerability in Docker Desktop for Windows has been discovered that allows any container to achieve full host system…
Attackers don’t always need a technical flaw. More often, they just trick your people. Social engineering works, and AI makes…
Security researchers from Adversa AI have uncovered a critical vulnerability in ChatGPT-5 and other major AI systems that allows attackers…
A small-town water system, a county hospital, and a local school district may not seem like front-line targets in global…