Author: Cybernoz
A new wave of cyberattacks is targeting WordPress websites through malicious SEO plugins that can lead to complete site takeover….
Microsoft is currently investigating a significant service disruption affecting Microsoft Forms, leaving numerous users unable to access the popular online…
Instagram has begun rotating its TLS certificates on a daily basis, with each certificate valid for just over a week….
We interviewed William Lyne, Head of Cyber Intelligence at the UK National Crime Agency (NCA), on the evolving ransomware ecosystem, the…
A sophisticated mobile ad fraud operation dubbed “IconAds” has infiltrated Android devices worldwide through 352 malicious applications distributed via Google…
Scattered Spider, also tracked under aliases such as UNC3944, Scatter Swine, and Muddled Libra, has emerged as a formidable financially…
Effective onboarding is essential in fast-paced hospitality, with high turnover rates and a multitude of expectations as the baseline for…
Critical security vulnerabilities have been discovered in PHP that could allow attackers to execute SQL injection attacks and cause denial…
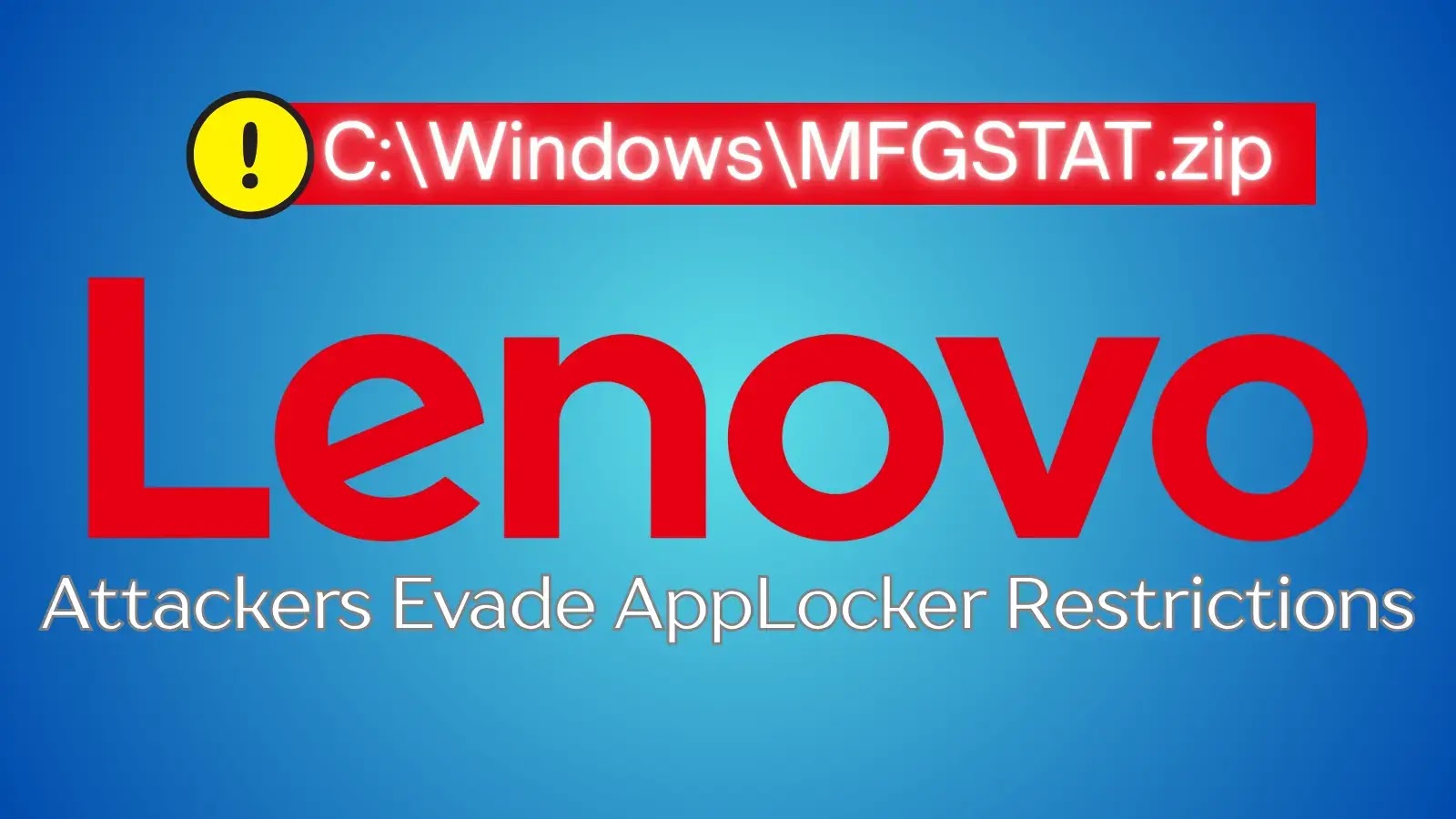
A security researcher has uncovered a significant vulnerability affecting Lenovo computers: a writable file within the Windows directory that can…
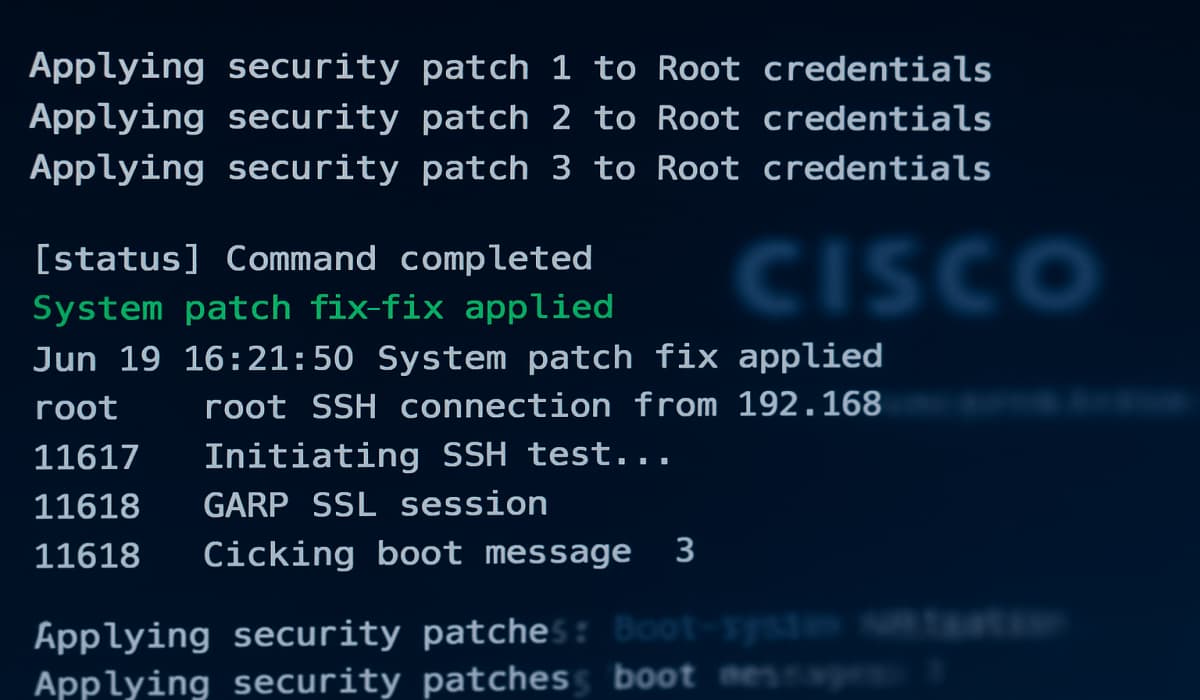
Cisco, a leading networking hardware company, has issued an urgent security alert and released updates to address a severe vulnerability…
Jul 04, 2025Ravie LakshmananVulnerability / Linux Cybersecurity researchers have disclosed two security flaws in the Sudo command-line utility for Linux…
A critical security vulnerability has been discovered in HIKVISION’s applyCT component, part of the HikCentral Integrated Security Management Platform, that…