Author: Cybernoz
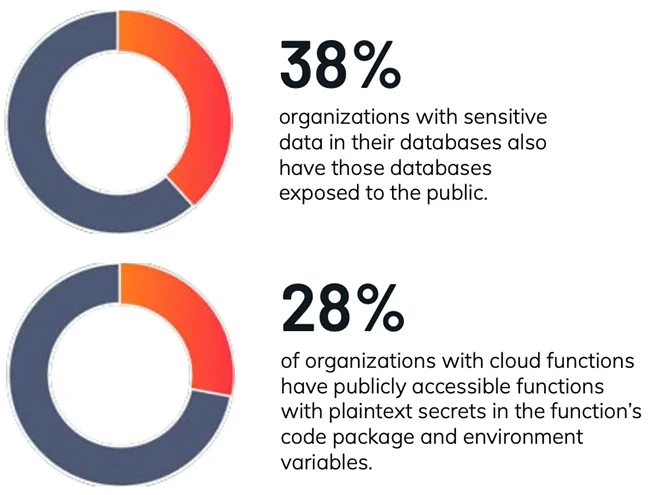
AI adoption is increasing, with 84% of organizations now using AI in the cloud, according to Orca Security. But this…
A critical security vulnerability in Google’s account recovery system allowed malicious actors to obtain the phone numbers of any Google…
A recent campaign by Chinese state-sponsored threat actor APT41 has unveiled a novel exploitation of Google Calendar for malware command-and-control…
Chinese state-sponsored hackers launched sophisticated reconnaissance operations against cybersecurity giant SentinelOne’s infrastructure in October 2024, representing part of a broader…
The Arkana Security extortion gang briefly listed over the weekend what appeared to be newly stolen Ticketmaster data but is…
Ransomware operators have increasingly turned to a sophisticated new malware tool called Skitnet, also known as “Bossnet,” to enhance their…
Riot police in Los Angeles fire a 40mm LMT weapon from Defense Technology, which is banned by Canada. Jim Vondruska/Getty…
Apple announced a slew of artificial intelligence features across its software and services and said it will open up the…
Whole Foods Market’s primary food distributor United Natural Foods is experiencing operational disruptions in response to a cyberattack it detected…
A comprehensive analysis of the Bitter espionage group has revealed eight years of sustained cyber operations employing increasingly sophisticated custom-developed…
Afterpay has overhauled its marketing technology stack, deploying Hightouch to turn its Snowflake environment into a customer data platform (CDP)….
Google’s latest comprehensive survey reveals a concerning surge in cybercriminal activities targeting American users, with over 60% of U.S. consumers…