Author: Cybernoz
Apple must face the US Department of Justice’s lawsuit accusing the iPhone maker of unlawfully dominating the US smartphone market,…
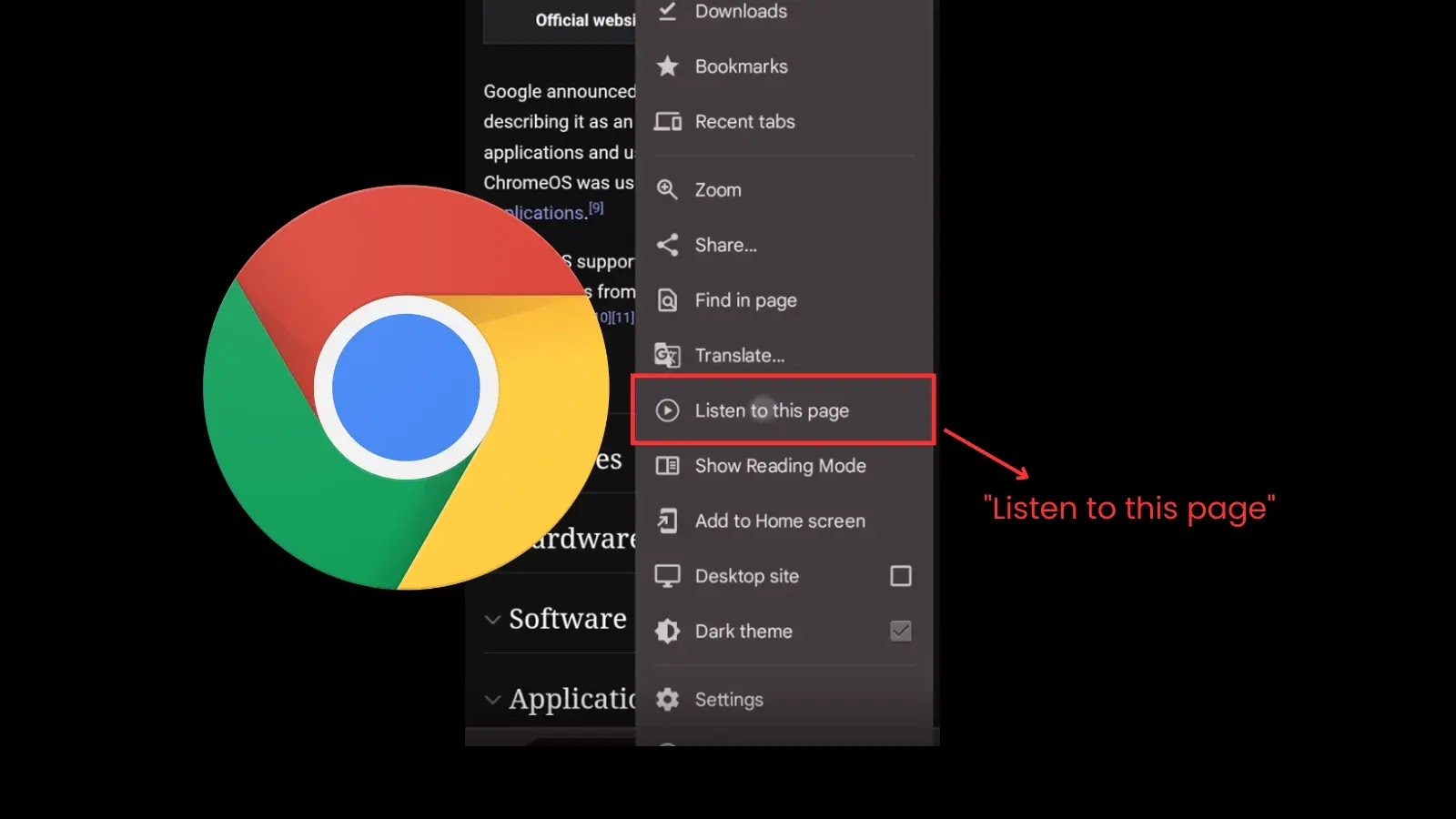
Google Chrome for Android is on the verge of a major upgrade that could reshape how users consume online content….
Woolworths Group has consolidated 30,000 marketing assets into Adobe’s digital asset management (DAM) platform in an effort to create a…
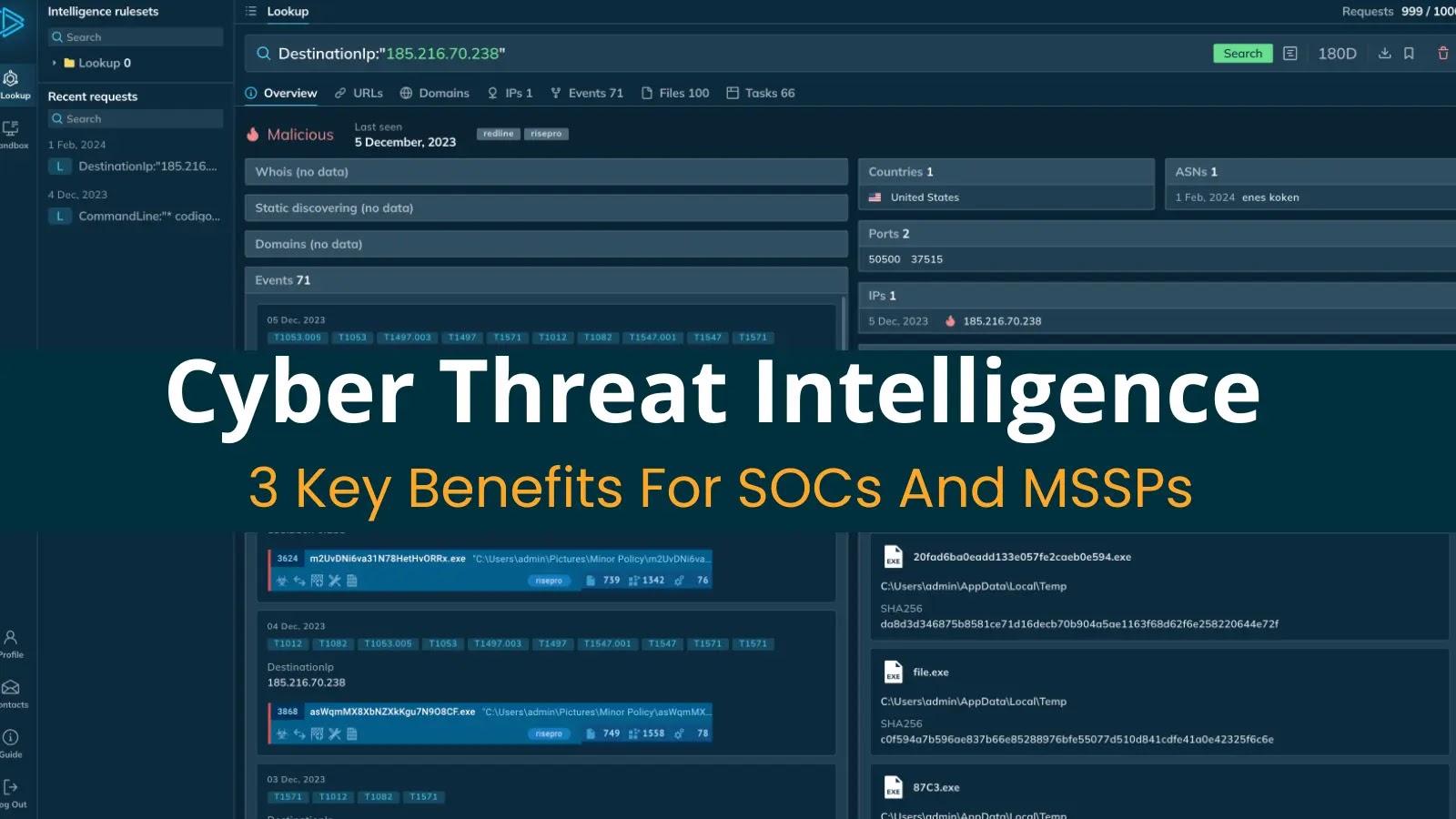
As attack vectors multiply and threat actors become increasingly sophisticated, security teams struggle to keep pace with the volume and…
Victoria Police has signed a $185 million renewal of its now-decade long IT support agreement with DXC Technology and Kinetic…
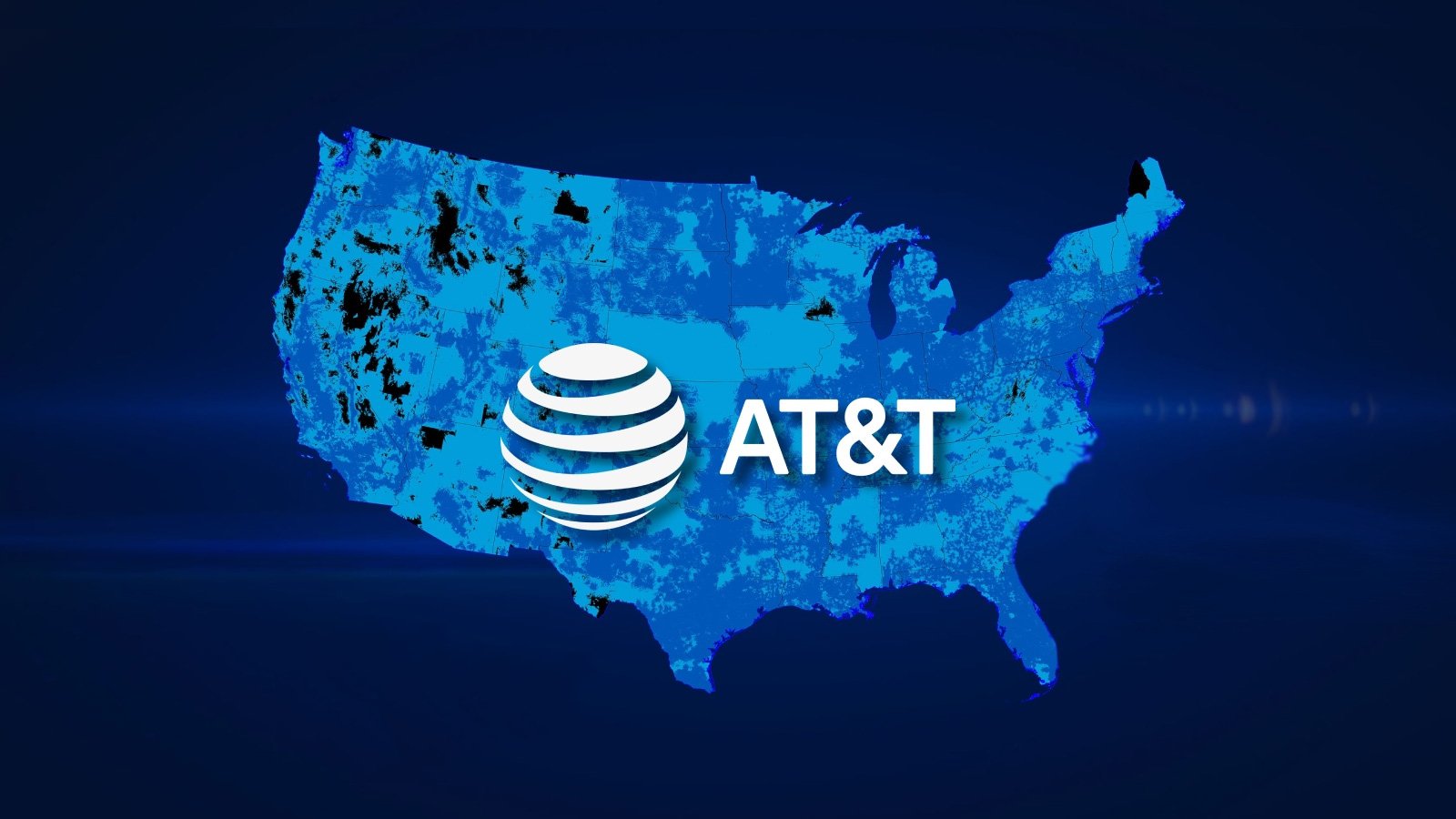
AT&T has launched a new security feature called “Wireless Lock” that protects customers from SIM swapping attacks by preventing changes…
A sophisticated phishing campaign leveraging the Snake Keylogger malware has emerged, exploiting legitimate Java debugging utilities to bypass security mechanisms…
Qilin was the top ransomware group by a wide margin in June, solidifying its position as the top ransomware group…
A sophisticated cyberattack hit the International Criminal Court Pierluigi Paganini July 01, 2025 The International Criminal Court (ICC) is probing…
Cloudflare announced Tuesday it will allow customers to block or charge fees for web crawlers deployed to scrape their websites…
A new FileFix attack allows executing malicious scripts while bypassing the Mark of the Web (MoTW) protection in Windows by…
The escalating tensions between Iran and Israel have triggered an unprecedented surge in hacktivist cyber operations, with over 80 distinct…