Author: Cybernoz
The constant evolution of cyber threats, particularly malware and ransomware, demands our unwavering attention. As threats advance, so must our…
Cybersecurity researchers have uncovered a large-scale attack targeting the npm ecosystem, compromising 16 popular React Native packages with a combined…
New Mirai botnet targets TBK DVRs by exploiting CVE-2024-3721 Pierluigi Paganini June 09, 2025 A new variant of the Mirai…
Socket’s Threat Research Team has uncovered two malicious npm packages, express-api-sync and system-health-sync-api, designed to masquerade as legitimate utilities while…
OpenAI has revealed that it banned a set of ChatGPT accounts that were likely operated by Russian-speaking threat actors and…
BadBox 2.0 botnet infects millions of IoT devices worldwide, FBI warns Pierluigi Paganini June 09, 2025 BadBox 2.0 malware has…
A sophisticated new malware attack vector that manipulates users through fake browser verification prompts designed to mimic legitimate CAPTCHA systems. …
June 6, 2025 – How to update Chrome on every Operating System (Windows, Mac, Linux, Chrome OS, Android, iOS) June…
The drumbeat of news around advances in artificial intelligence (AI) has become impossible to ignore. And yet it still doesn’t…
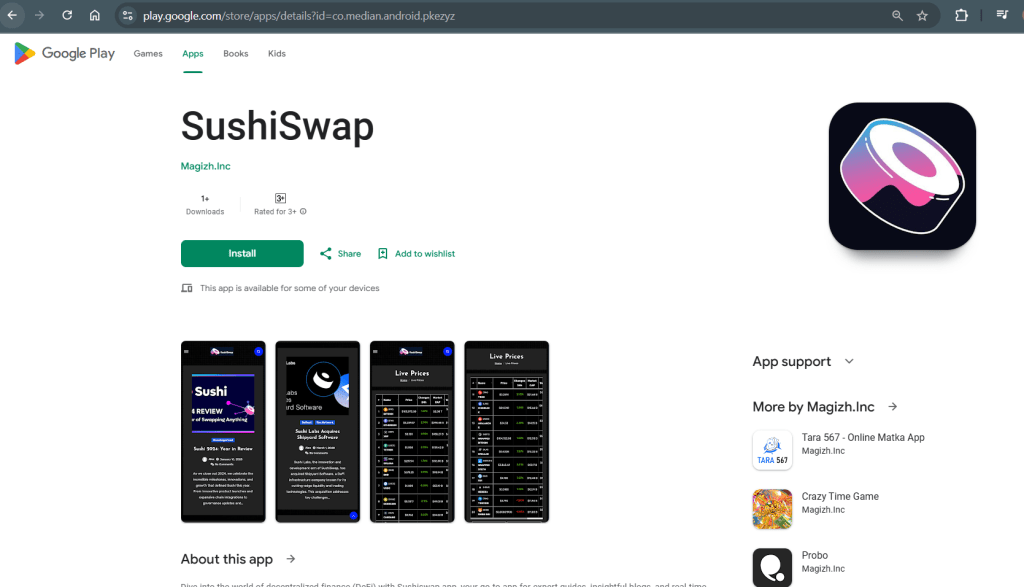
Cyble Research and Intelligence Labs (CRIL) has recently uncovered a malicious crypto phishing campaign where more than 20 malicious applications…
In the rapidly shifting digital world, cybersecurity professionals are constantly seeking innovative tools that not only streamline workflows but also…
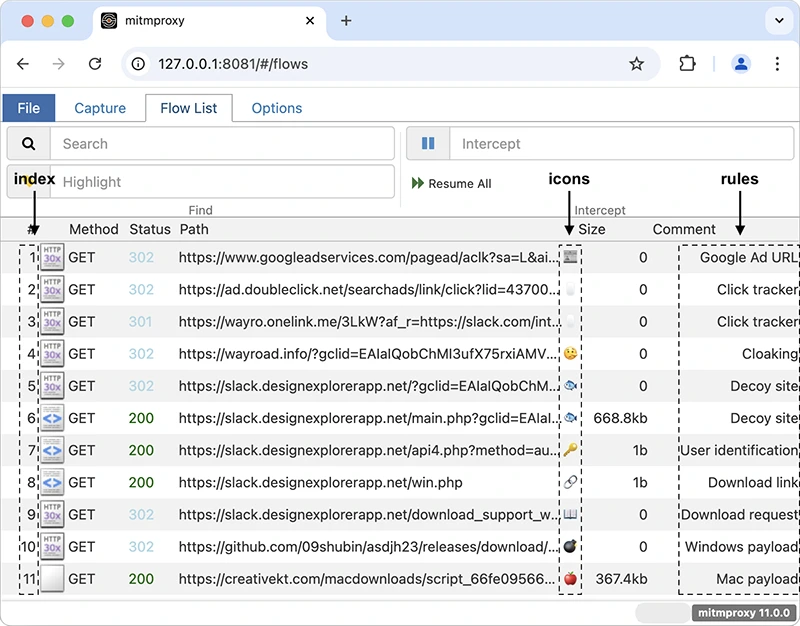
fiddleitm is an open-source tool built on top of mitmproxy that helps find malicious web traffic. It works by checking…