Author: Cybernoz
In this Help Net Security interview, Renana Friedlich-Barsky, EVP and CISO at LPL Financial, discusses how threat actors are targeting…
The threat landscape in the bioeconomy is different from what most CISOs are used to. It includes traditional risks like…
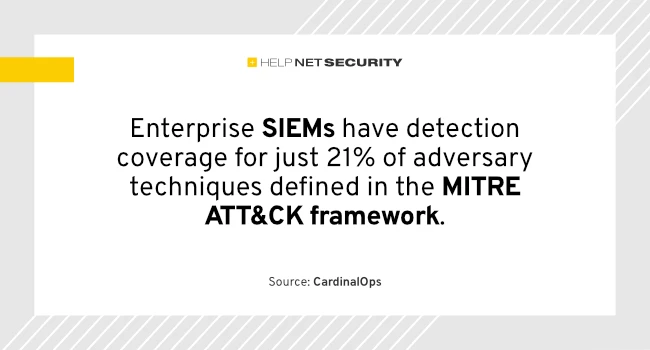
Using the MITRE ATT&CK framework as a baseline, organizations are generally improving year-over-year in understanding security information and event management…
In just 12 months, attackers attempted to steal more than $300 million via vendor email compromise (VEC), with 7% of…
A new proof-of-concept (PoC) exploit for a critical zero-day vulnerability affecting multiple Fortinet products raises urgent concerns about the security…
I’m sure you’ve heard the argument that LLMs aren’t really thinking because, according to them, LLMs are just predicting the…
A financially motivated group of hackers known as UNC6040 is using a surprisingly simple but effective tactic to breach enterprise…
A new variant of the Mirai malware botnet is exploiting a command injection vulnerability in TBK DVR-4104 and DVR-4216 digital…
Cybersecurity researchers have flagged a supply chain attack targeting over a dozen packages associated with GlueStack to deliver malware. The…
Over 950K weekly downloads at risk in ongoing supply chain attack on Gluestack packages Pierluigi Paganini June 08, 2025 A…
Security Affairs newsletter Round 527 by Pierluigi Paganini – INTERNATIONAL EDITION Pierluigi Paganini June 08, 2025 A new round of…
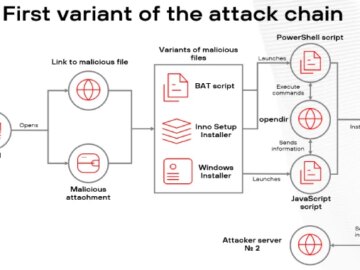
Jun 08, 2025Ravie LakshmananMalware / Browser Security Cybersecurity researchers have shed light on a new campaign targeting Brazilian users since…