Author: Cybernoz
A notice to House offices Monday from the chamber’s chief administrative officer said that staffers are forbidden from having WhatsApp…
If you have internet-connected cameras in or around your home, be sure to check their settings. Researchers just discovered 40,000…
A US federal judge in San Francisco has ruled that Anthropic’s use of books without permission to train its artificial…
SonicWall is warning customers that threat actors are distributing a trojanized version of its NetExtender SSL VPN client used to…
Australia’s internet watchdog and YouTube exchanged barbs after the regulator urged the government to reverse a planned exemption for the…
Demystifying Cyber Risk: How Qualys is Transforming Security Leadership Cybersecurity leadership is undergoing a profound transformation. No longer confined to…
Cybersecurity researchers at Kaspersky have reported a new spyware operation, dubbed SparkKitty, that has infected apps available on both the…
Jun 24, 2025Ravie LakshmananSocial Media / Privacy The United States Embassy in India has announced that applicants for F, M,…
Trezor is alerting users about a phishing campaign that abuses its automated support system to send deceptive emails from its…
British businesses are suffering significantly more damaging losses from ransomware attacks compared to the rest of the world, where things…
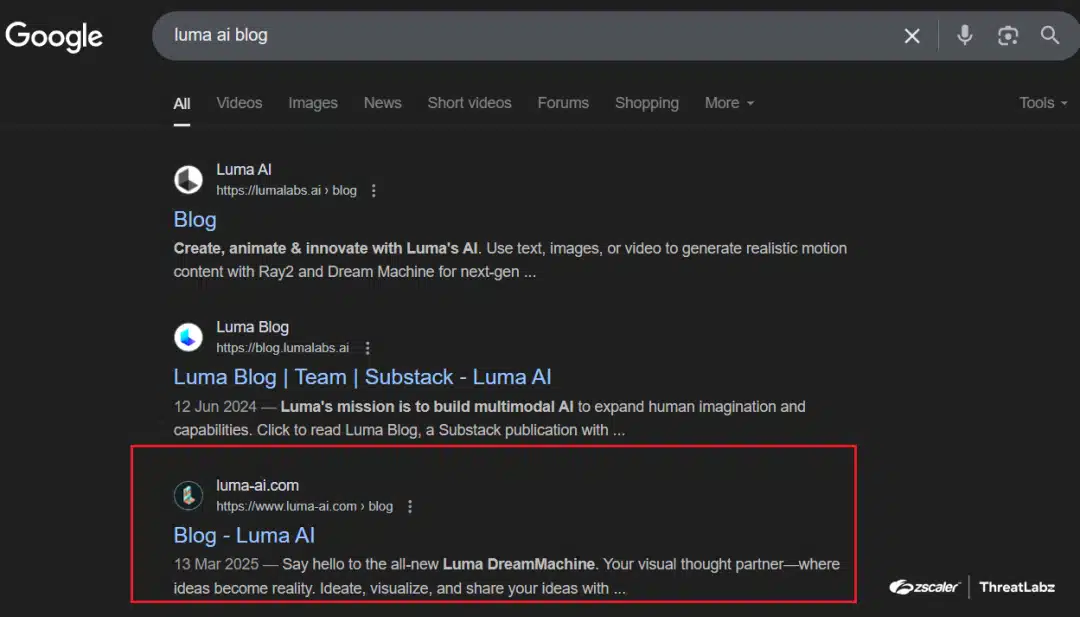
Threat actors are hijacking Google search results for popular AI platforms like ChatGPT and Luma AI to deliver malware, in…
Microsoft says Windows 10 home users who want to delay switching to Windows 11 can enroll in the Extended Security Updates…