Author: Cybernoz
The Justice Department announced on Wednesday that two men accused of breaching a law enforcement portal as part of a…
Broadcom has issued a high-severity security advisory (VMSA-2025-0012) for VMware NSX, addressing three newly discovered stored Cross-Site Scripting (XSS) vulnerabilities:…
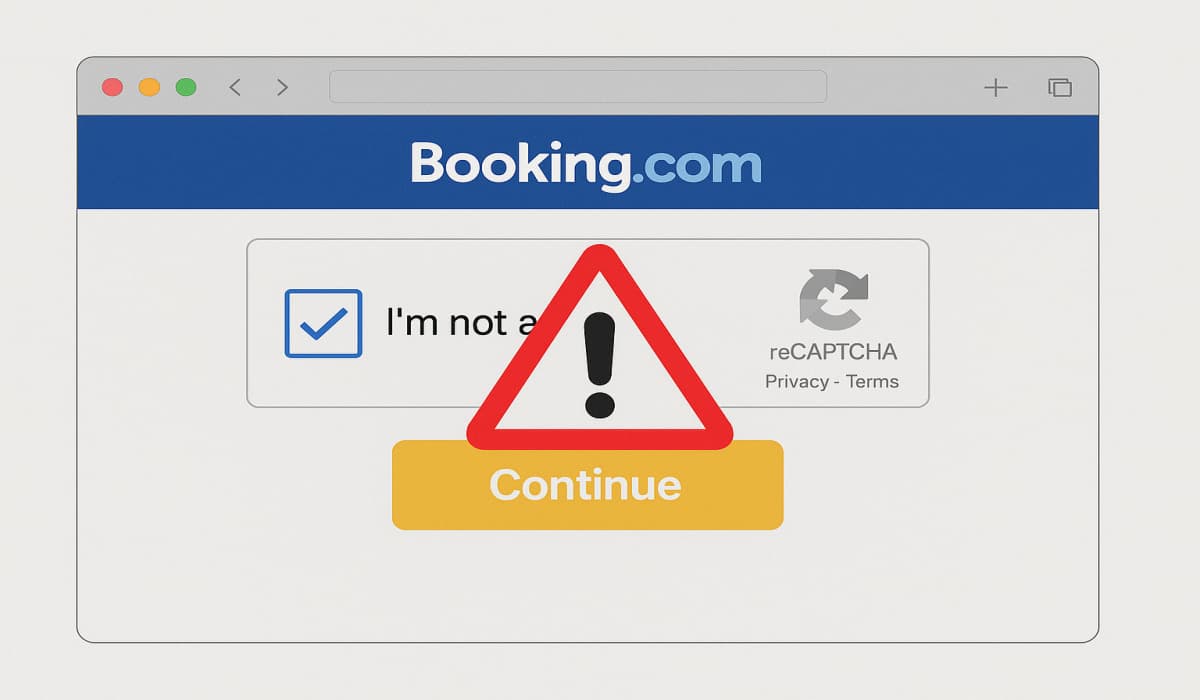
Cofense Intelligence uncovers a surge in ClickFix email scams impersonating Booking.com, delivering RATs and info-stealers. Learn how these sophisticated attacks…
Artificial intelligence (AI) and small business tools are being abused as smokescreens to hit unsuspecting victims with ransomware. In the…
ClickFix is not a malware, but a very successful social engineering technique. It primarily relies on MFA verification fatigue and…
The German data protection authority (BfDI) has fined Vodafone GmbH, the telecommunications company’s German subsidiary, €45 million ($51.4 million) for…
In a Rhino Security Labs, six critical vulnerabilities have been identified in Infoblox’s NetMRI network automation and configuration management solution,…
Jun 05, 2025Ravie LakshmananDark Web / Law Enforcement The U.S. Department of Justice (DoJ) on Wednesday announced the seizure of…
As data breaches rise and public trust flickers, Australia has taken a bold step in reforming its Privacy Act, marking…
American media company Lee Enterprises revealed this week that the disruptive cyberattack it dealt with earlier this year resulted in…
The financially motivated threat cluster UNC6040, tracked by Google Threat Intelligence Group (GTIG), has been orchestrating a series of voice…
Approximately 145 dark web and clear web domains associated with the BidenCash marketplace have been seized, the US Department of…