Author: Cybernoz
© 2025 Condé Nast. All rights reserved. WIRED may earn a portion of sales from products that are purchased through…
The Mobile Threat Intelligence (MTI) team identified a formidable new player in the mobile malware landscape: Crocodilus, an Android banking…
Infosecurity Europe 2025 is a cybersecurity event taking place from June 3 to 5 in London. Help Net Security is…
Sports apparel and footwear giant VF Corporation is notifying over 2,800 individuals that their personal information was compromised in a…
On May 15, 2025, Coinbase, the largest U.S. cryptocurrency exchange, publicly disclosed a major security breach that exposed the sensitive…
India, China and the US were the top DDoS attacks targets in Q1 2025, with APAC facing over half of…
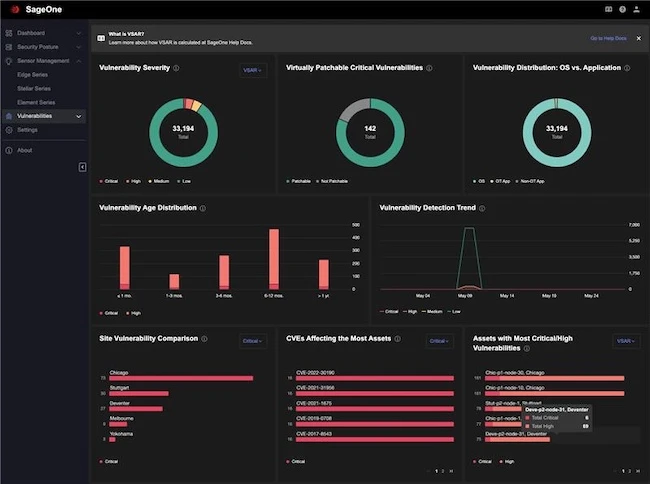
TXOne Networks announced an expanded new version of its SageOne OT Cybersecurity Governance Platform. Already relied upon by many industrial…
Small and medium-sized enterprises (SMEs) employ a staggering number of people in the UK, and are especially vulnerable to cyber…
$500m from UAE’s Castle Investments Demonstrates worldwide AI growth Data centres could empower startups Turkey’s data centre industry is experiencing…
Threat actors have been found exploiting the ubiquitous “Prove You Are Human” verification systems to distribute malicious software. Specifically, this…
TXOne Networks announced an expanded new version of its SageOne OT Cybersecurity Governance Platform. Already relied upon by many industrial…
One of the most significant conundrums faced by any organisation that plans a cloud migration is that there are many…