Author: Cybernoz
An analysis conducted recently by researchers at cybersecurity firm Forescout showed that roughly 35,000 solar power systems are exposed to…
Cartier disclosed a data breach following a cyber attack Pierluigi Paganini June 04, 2025 Luxury-goods conglomerate Cartier disclosed a data…
Researchers have unearthed a sophisticated supply chain attack targeting Ruby Gems, a popular package manager for the Ruby programming language….
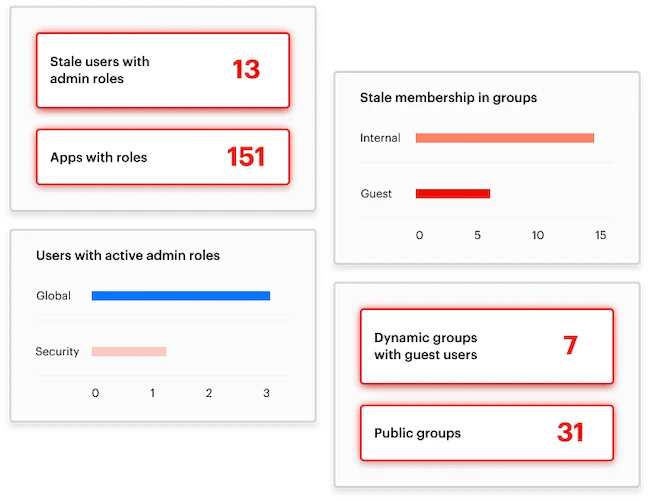
Varonis announced Varonis Identity Protection, the latest enhancement to its Data Security Platform that gives organizations visibility and control of…
Browse by Chapters Click on the tiles below to navigate the practical realities of the cloud ecosystem. Cloud Covered Champion…
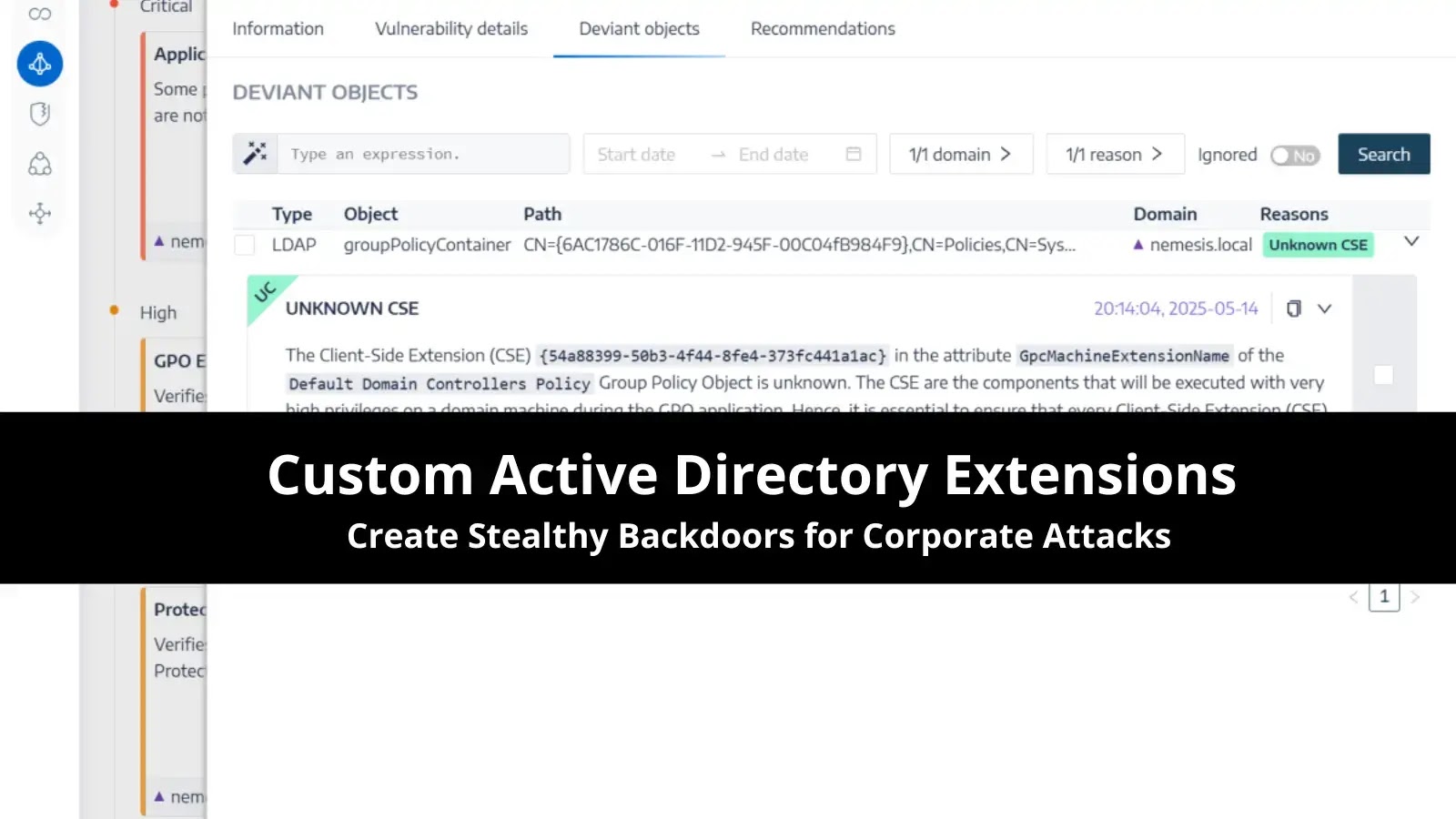
Active Directory (AD) Group Policy Objects (GPOs) are a cornerstone of centralized management for Windows environments, enabling administrators to configure…
Browse by Chapters Click on the tiles below to navigate the practical realities of the cloud ecosystem. Cloud Covered Champion…
Since 2016, the “DollyWay World Domination” campaign has quietly compromised more than 20,000 WordPress websites worldwide, exploiting vulnerabilities in plugins…
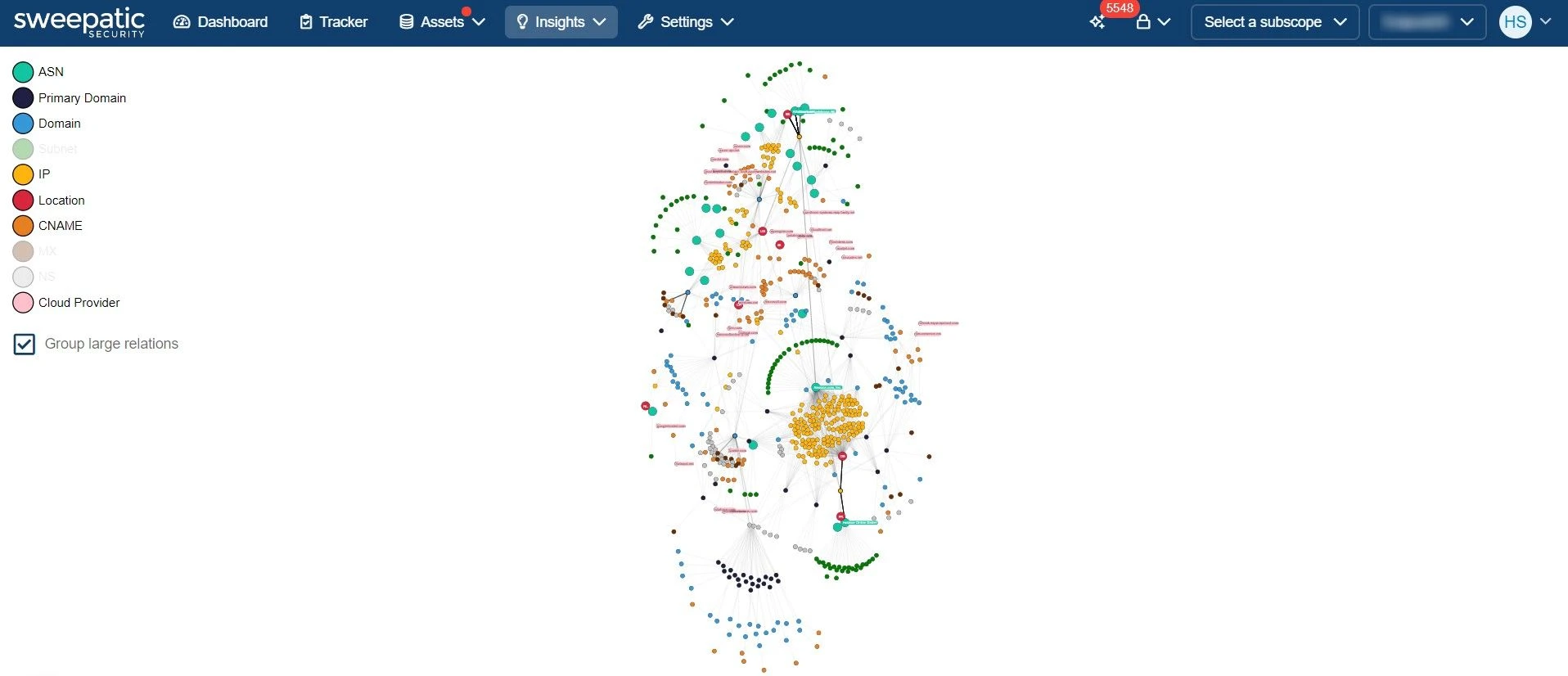
According to research, 62% of organizations said their attack surface grew over the past year. It’s no coincidence that 76%…
Decentralized identity (DID) is gaining traction, and for CISOs, it’s becoming a part of long-term planning around data protection, privacy,…
Jun 04, 2025The Hacker NewsVulnerability / DevOps Hewlett Packard Enterprise (HPE) has released security updates to address as many as…
In this Help Net Security interview, Thomas Squeo, CTO for the Americas at Thoughtworks, discusses why traditional security architectures often…