Author: Cybernoz
Jun 03, 2025Ravie LakshmananEmail Security / Vulnerability Cybersecurity researchers have disclosed details of a critical security flaw in the Roundcube…
Scams are no longer annoyances, tricking individuals but not damaging the economy. They have become big business, with Arkose Labs…
Android banking trojan Crocodilus rapidly evolves and goes global Pierluigi Paganini June 03, 2025 A new Android banking trojan called…
Reconnaissance plays an integral part in bug bounty hunting, with hidden parameter discovery an even more crucial role as they…
With the recent attacks on UK retailers Marks & Spencer and Co-op, so-called Scattered Spider has been all over the…
Microsoft Edge for Android is rolling out an enhanced privacy feature that allows users to secure their InPrivate browsing sessions…
Aembit, the workload identity and access management (IAM) company, today announced a major expansion of its platform to support Microsoft…
Silver Spring, Maryland, June 3rd, 2025, CyberNewsWire Aembit, the workload identity and access management (IAM) company, today announced a major…
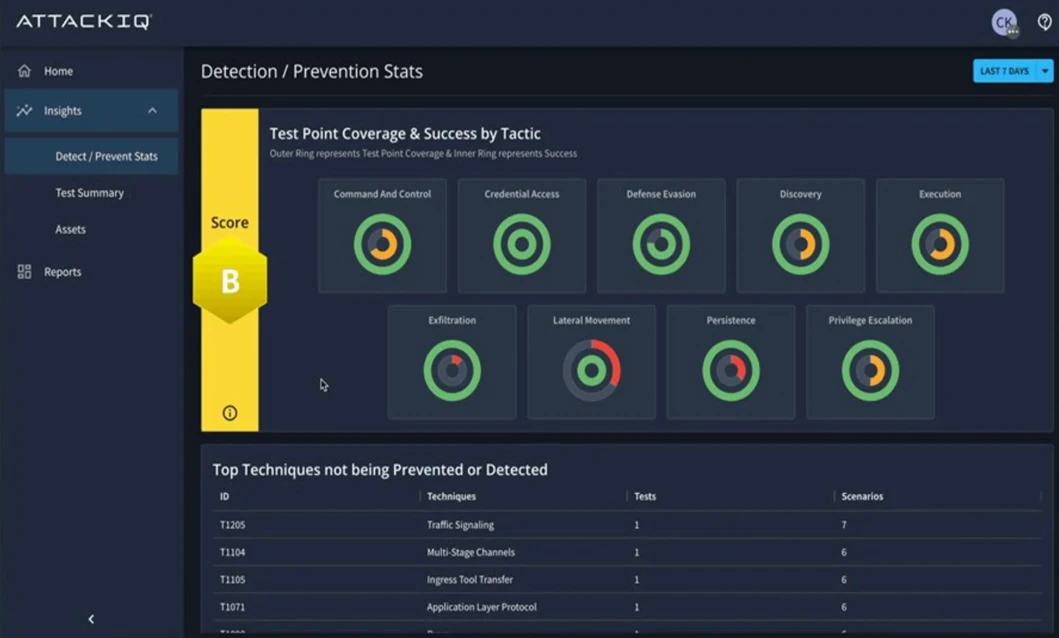
AttackIQ releaseed AttackIQ Ready3. With expanded discovery capabilities, Ready3 maps both internal and external attack surfaces. By correlating asset discovery…
As generative AI (GenAI) tools become embedded in the fabric of enterprise operations, they bring transformative promise, but also considerable…
Over 1,000 industrial monitoring devices made by Canada-based Instantel may be exposed to remote hacking due to a critical vulnerability….
Fashion retail giant Victoria’s Secret has delayed its first quarter 2025 earnings release because of ongoing corporate system restoration efforts…