Author: Cybernoz
Jun 02, 2025Ravie LakshmananSpyware / Vulnerability Qualcomm has shipped security updates to address three zero-day vulnerabilities that it said have…
North Lincolnshire Council has received a planning application for a 1,000mW datacentre campus, as its push to become a government-backed…
Mobile chipmaker Qualcomm on Monday warned that professional hackers are already exploiting three newly patched Adreno GPU bugs and the…
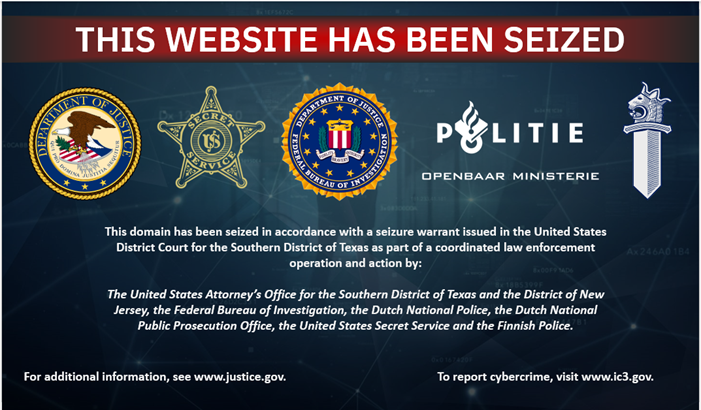
Police took down several popular counter-antivirus (CAV) services, including AvCheck Pierluigi Paganini June 02, 2025 On May 27, 2025, authorities…
Listen to the article 5 min This audio is auto-generated. Please let us know if you have feedback. President Donald…
The “Russian Market” cybercrime marketplace has emerged as one of the most popular platforms for buying and selling credentials stolen by…
A recently disclosed vulnerability in IBM InfoSphere DataStage, tracked as CVE-2025-1499, has raised concerns across the enterprise data management sector….
The government has run a trial of using artificial intelligence (AI) with 20,000 civil servants which it said demonstrates they…
MediaTek has published its latest Product Security Bulletin, revealing several security vulnerabilities affecting a wide range of its chipsets used…
Among all ages, Minecraft still rules the gaming scene as a preferred choice. The game provides a broad spectrum of…
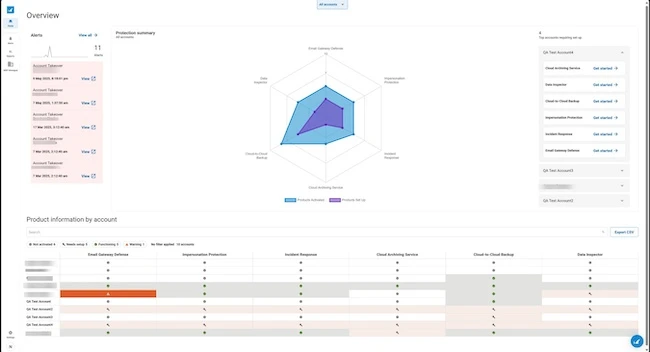
Barracuda Networks unveiled the BarracudaONE AI-powered cybersecurity platform. BarracudaONE maximizes threat protection and cyber resilience by unifying layered security defenses…
The introduction of generative artificial intelligence (GenAI) into any organisation spreads anxiety among the workforce, in much the same way…