Author: Cybernoz
From a flurry of attacks targeting UK retailers to campaigns corralling end-of-life routers into botnets, it’s a wrap on another…
As organizations continue to embrace hybrid and remote work models in 2025, securing remote endpoints has become one of the…
History of OWASP Top 10 | HAHWUL 2021 A1 Broken Access Control A2 Cryptographic Failures A3 Injection A4 Insecure Design…
As organizations grapple with an increasingly fragmented digital landscape in mid-2025, advanced endpoint threat detection has become the linchpin of…
Using Deadfinder and GitHub Actions for Seamless Link Management A dead link, or broken link, occurs when a hyperlink points…
As organizations navigate an increasingly complex patchwork of privacy regulations worldwide, encryption has emerged as a critical tool for compliance…
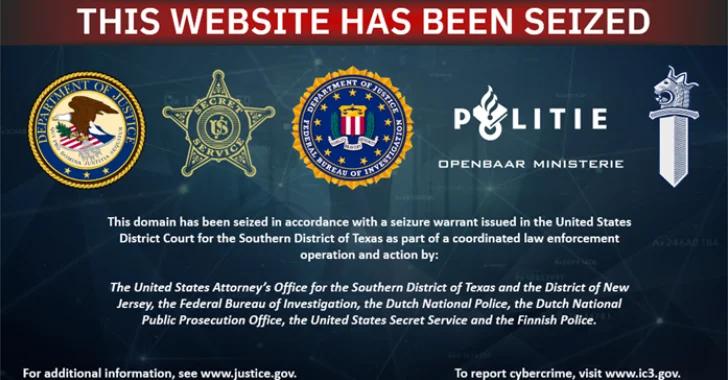
May 31, 2025Ravie LakshmananMalware / Cyber Crime A multinational law enforcement operation has resulted in the takedown of an online…
Hello, security enthusiasts! Today, we’re diving into the exciting new features of OWASP Noir v0.18, particularly focusing on the PassiveScan…
Data Subject Access Requests (DSARs) have emerged as a critical compliance challenge for businesses worldwide as privacy regulations continue to…
Keeper Security has unveiled an update to its password management platform: Keeper’s upgraded One-Time Share. The new feature enables bidirectional,…
Cybersecurity firm Quorum Cyber has uncovered two new versions of malicious software known as NodeSnake. This discovery highlights a possible…
May 31, 2025Ravie LakshmananVulnerability / Linux Two information disclosure flaws have been identified in apport and systemd-coredump, the core dump…