Author: Cybernoz
Microsoft is ending support for Exchange Server 2016, Exchange Server 2019, and Outlook 2016 on October 14, 2025. That date…
Breaking Out of the Security Mosh Pit When Jason Elrod, CISO of MultiCare Health System, describes legacy healthcare IT environments,…
Over the past few weeks, VMware customers holding onto their perpetual licenses, which are often unsupported and in limbo, have…
The US Treasury Department on Thursday announced sanctions against a Philippines-based company for providing infrastructure to hundreds of thousands of…
My journey migrating from Jekyll to Zola, a Rust-based SSG. It’s been nearly three years since I switched back from…
ConnectWise is investigating suspicious activity — likely associated with a nation-state actor — affecting a limited number of customers that use ScreenConnect. …
With Infosecurity Europe around the corner next week, planning your schedule can be tricky. But never fear! The Gurus have…
Cybersecurity researchers from Trustwave’s Threat Intelligence Team have uncovered a large-scale phishing campaign orchestrated by the notorious hacker group Storm-1575,…
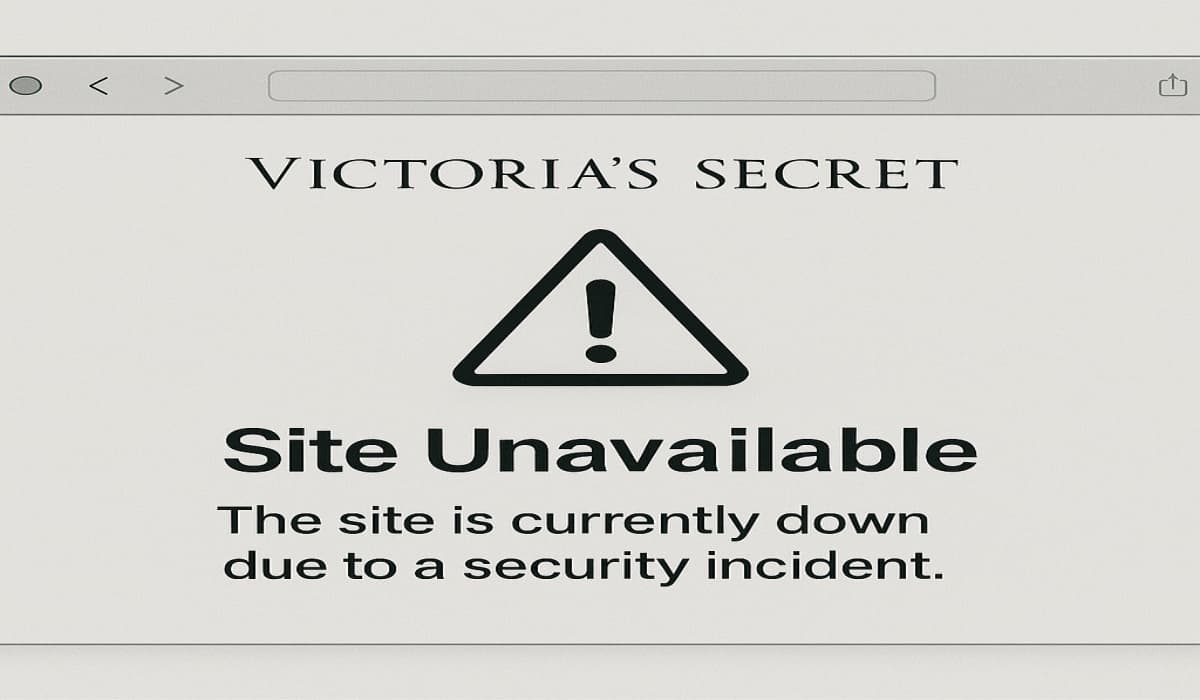
Victoria’s Secret website was down due to a ‘security incident’ impacting online and some in-store services. Get the latest on…
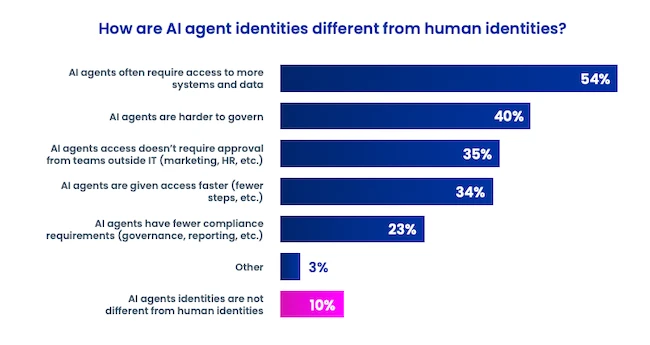
82% of organizations already use AI agents, but only 44% of organizations report having policies in place to secure them,…
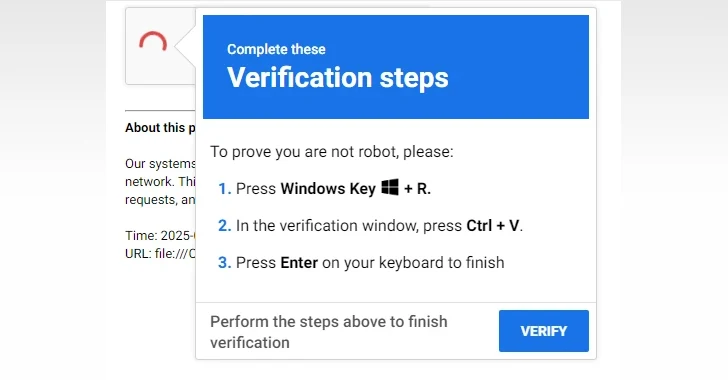
A new malware campaign is distributing a novel Rust-based information stealer dubbed EDDIESTEALER using the popular ClickFix social engineering tactic…
What does US retrenchment on Diversity, Equality and Inclusion, mean for tech companies in the UK, and could a similar…