Author: Cybernoz
The recent leak of sensitive US military operations via the Signal messaging platform, triggered by the accidental inclusion of a…
Quantum computing is rapidly emerging as one of the most transformative technology trends of 2025, promising to revolutionize industries by…
PALO ALTO, California, May 29th, 2025, CyberNewsWire Today, SquareX released new threat research on an advanced Browser-in-the-Middle (BitM) attack targeting…
Search hijacking, often referred to as browser hijacking, occurs when cybercriminals modify users’ browser settings without their consent. This often results…
Cyber security has long been likened to building a fortress: thick walls, watchtowers, and a moat separating the inside from…
As part of its ongoing commitment to product security, Dell Technologies has released a significant update for the PowerStore T…
Microsoft is looking to streamline the software updating process for IT admins and users by providing a Windows-native update orchestration…
Regulations and legal frameworks for artificial intelligence (AI) currently lag behind the technology’s uptake. The rise of generative AI (GenAI)…
Lingerie retailer Victoria’s Secret has fallen victim to a cyberattack that forced it to take its website down on Wednesday….
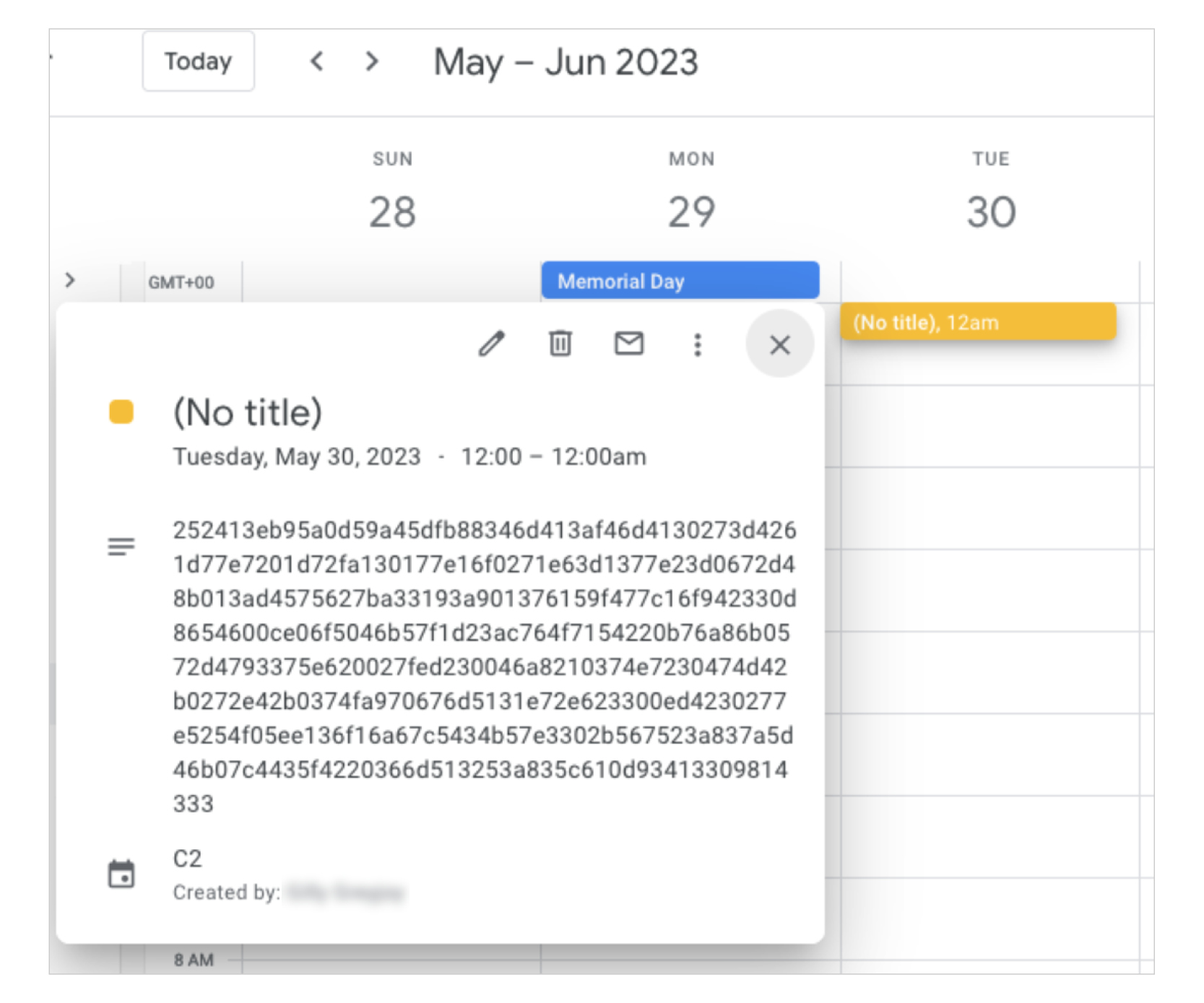
China-linked APT41 used Google Calendar as C2 to control its TOUGHPROGRESS malware Pierluigi Paganini May 29, 2025 Google says China-linked…
IMAGE: ROWANLOVESCARS (CC BY-SA 4.0) Fashion giant Victoria’s Secret has taken down its website and some store services because of…
Security Information and Event Management (SIEM) platforms are essential for detecting, analyzing, and responding to cybersecurity threats in real time….