Author: Cybernoz
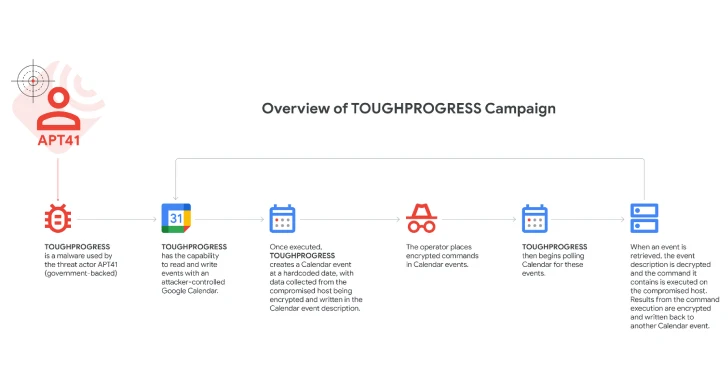
May 29, 2025Ravie LakshmananMalware / Cloud Security Google on Wednesday disclosed that the Chinese state-sponsored threat actor known as APT41…
New AyySSHush botnet compromised over 9,000 ASUS routers, adding a persistent SSH backdoor. Pierluigi Paganini May 29, 2025 GreyNoise researchers…
Mike Wilkes has had a career many cybersecurity professionals could only dream of. An adjunct professor, former CISO of Marvel…
A critical security flaw in Microsoft’s OneDrive File Picker has exposed millions of users to unauthorized data access, allowing third-party…
At Span Cyber Security Arena, I sat down with Ria Shetty, Director, Cyber Security & Resilience for Europe at Mastercard….
May 29, 2025Ravie LakshmananVulnerability / Website Security Cybersecurity researchers have disclosed a critical unpatched security flaw impacting TI WooCommerce Wishlist…
As Australia races to meet ambitious housing targets, a quiet crisis is playing out in council offices across the country….
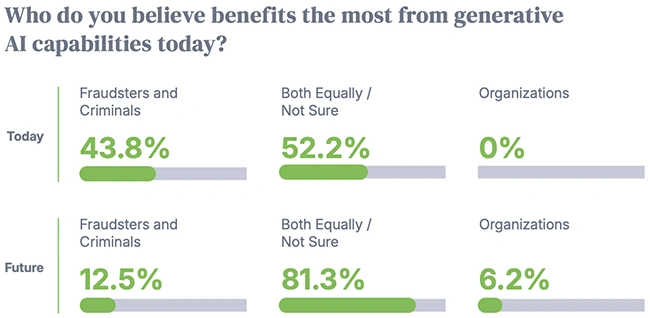
Fraudsters are winning the AI arms race, first-party fraud is rising, and siloed systems are holding back defenses, according to…
Cybersecurity leaders and consultants identified AI-driven automation and cost optimization as top organizational priorities, according to Wipro. 30% of respondents…
If you’re new to cybersecurity and looking for a book that doesn’t overwhelm you with jargon or dive too deep…
Cybersecurity researchers have uncovered a sophisticated new attack method called “ChoiceJacking” that allows malicious charging stations to steal sensitive data…
Cybercriminals impersonate the trusted e-signature brand and send fake Docusign notifications to trick people into giving away their personal or…