Author: Cybernoz
Russia’s GRU-backed APT28, widely known as Fancy Bear, has intensified its cyber espionage campaign against NATO-aligned organizations. Active since at…
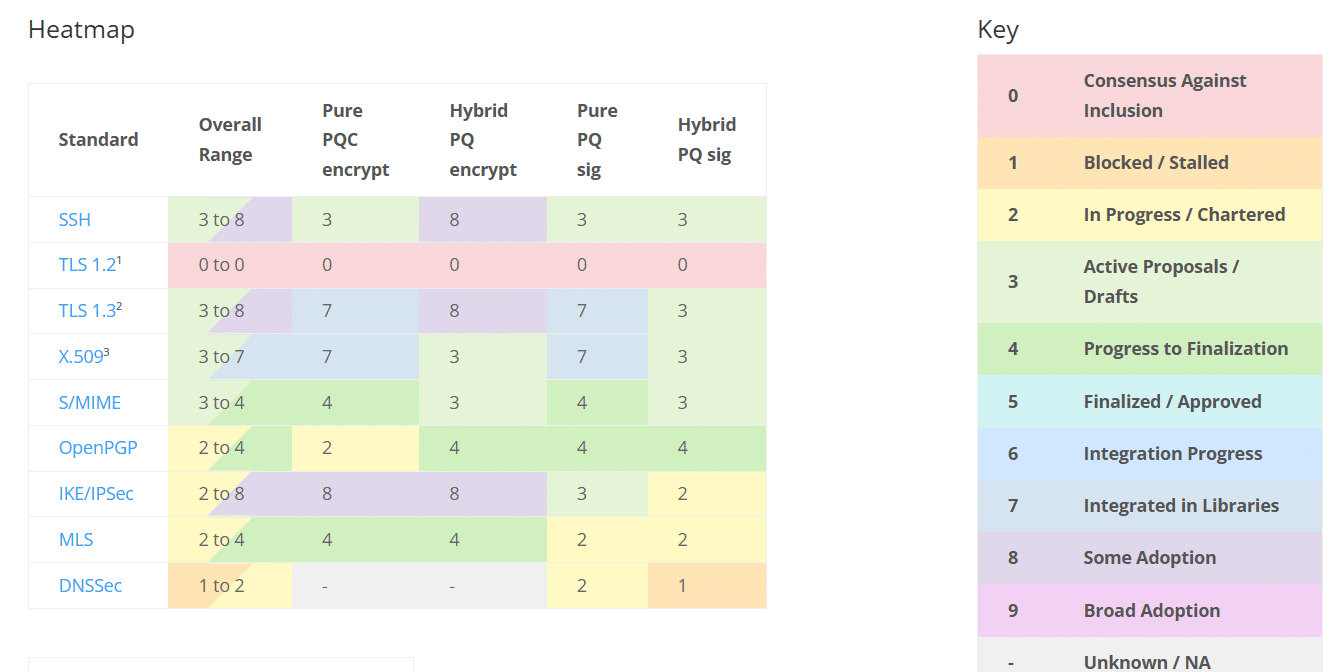
As estimates of the quantum computing power needed to crack current public key encryption algorithms continue to drop, a group…
Software maker MathWorks this week confirmed that a widespread outage that has impacted its applications since May 18 was the…
Google said Wednesday that it caught suspected People’s Republic of China-backed hackers leveraging its Calendar service to help stealthily stage…
A critical security vulnerability in the popular TI WooCommerce Wishlist plugin has left over 100,000 WordPress websites exposed to potential…
Cybersecurity researchers at Trend Research have uncovered the aggressive operations of Earth Lamia, an Advanced Persistent Threat (APT) group with…
Security researchers have uncovered a significant cybercrime operation involving 93.7 billion stolen browser cookies circulating on dark web marketplaces, representing…
Apple has strengthened the App Store as a bulwark of confidence, a remarkable testament to its commitment to customer safety….
Cybercriminals are taking advantage of the public’s interest in Artificial Intelligence (AI) and delivering malware via text-to-video tools. According to…
May 28, 2025Ravie LakshmananCybersecurity / Cyber Espionage The Czech Republic on Wednesday formally accused a threat actor associated with the…
The Interlock ransomware gang is deploying a previously undocumented remote access trojan (RAT) named NodeSnake against educational institutes for persistent…
As the digital threat landscape intensifies and new technologies reshape business operations, cybersecurity budgeting in 2025 will be significantly transformed….