Author: Cybernoz
A newly disclosed vulnerability, CVE-2025-33073, dubbed the “Reflective Kerberos Relay Attack,” has shaken the Windows security landscape. Discovered by RedTeam…
Jun 12, 2025Ravie LakshmananVulnerability / Software Security ConnectWise has disclosed that it’s planning to rotate the digital code signing certificates…
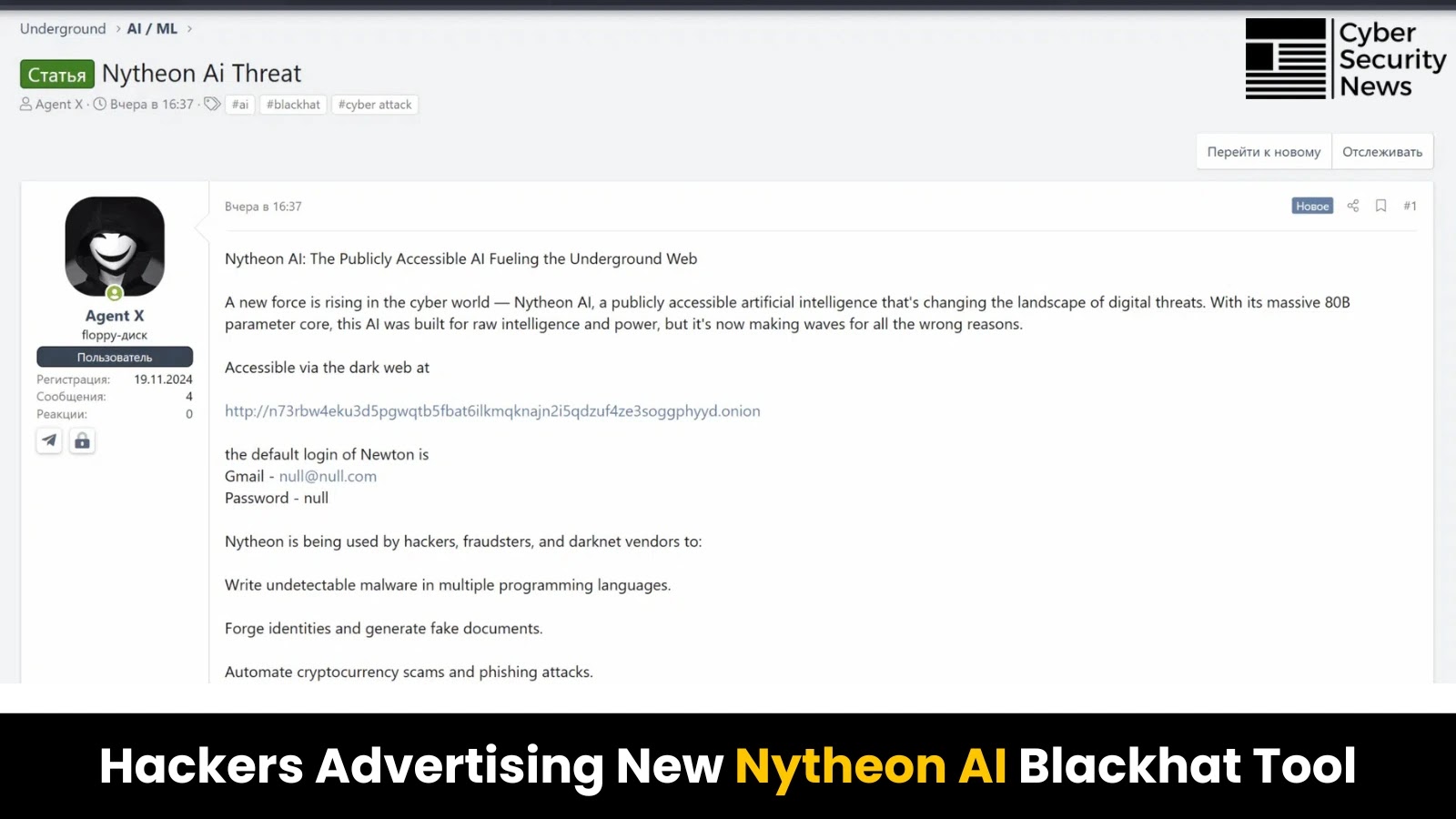
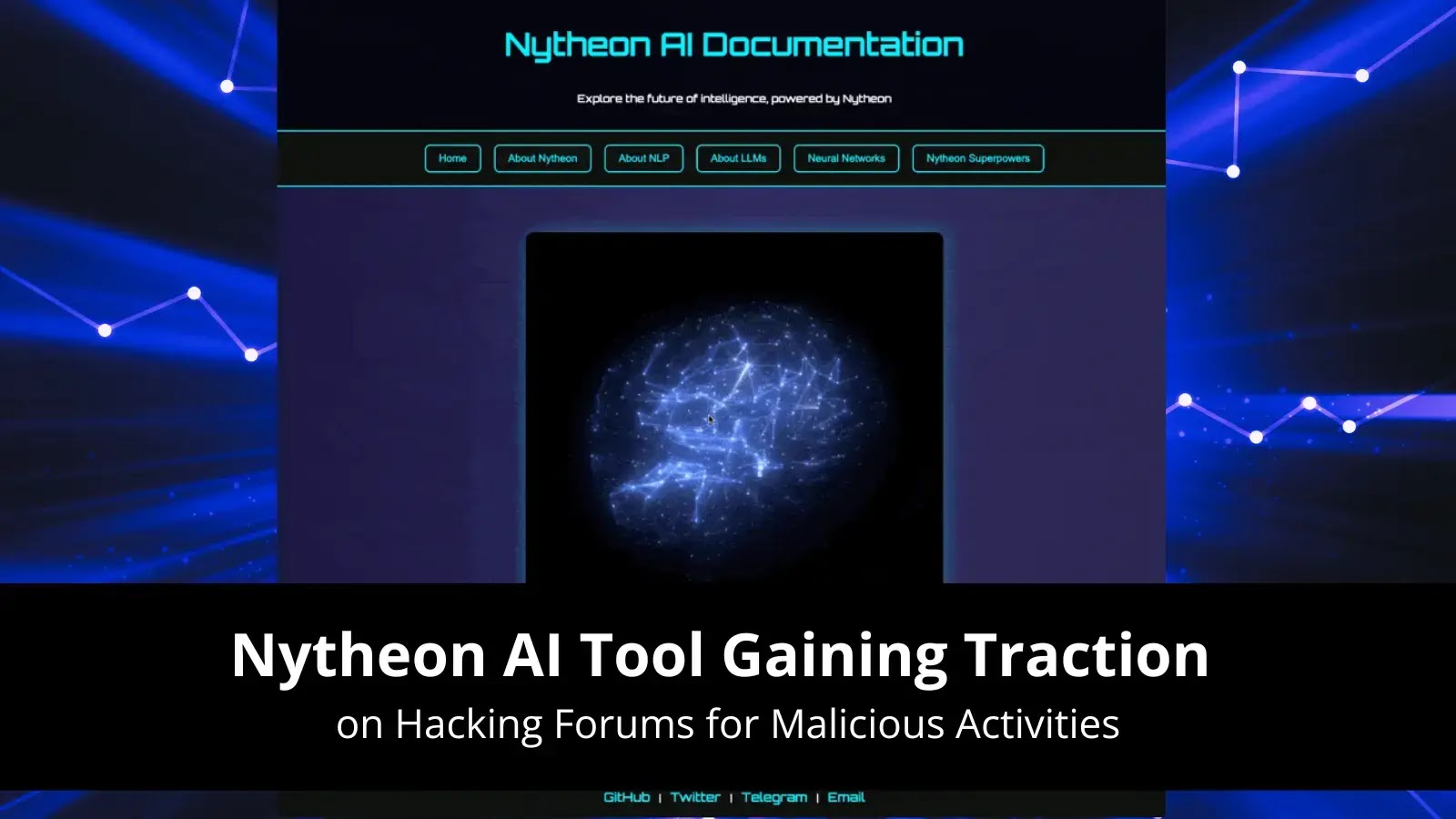
A sophisticated new threat platform, Nytheon AI, has emerged, which combines multiple uncensored large language models (LLMs) built specifically for…
Security researchers have uncovered the first-ever zero-click vulnerability in an AI agent, targeting Microsoft 365 Copilot and potentially exposing sensitive…
Lemony announced its on-premise artificial intelligence solution that is redefining how organizations deploy generative AI. Lemony’s secure, hardware-based node offers…
Exposed eyes: 40,000 security cameras vulnerable to remote hacking Pierluigi Paganini June 12, 2025 Over 40,000 internet-exposed security cameras worldwide…
The emergence of Nytheon AI marks a significant escalation in the landscape of uncensored large language model (LLM) platforms. Unlike…
A cybersecurity hobbyist has built a compact, foldable mobile hacking rig that runs Kali NetHunter on a Google Pixel 3…
Nestled in a log cabin high in the Rocky Mountains, Rick Bohm starts his day the same way he’s approached…
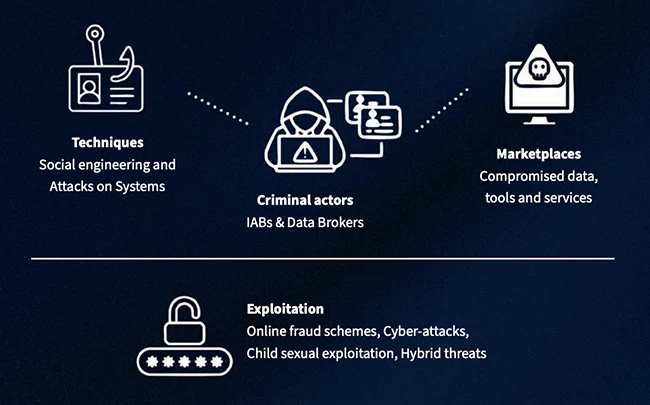
Cybercriminals are stealing data and running full-scale businesses around it. Europol’s latest Internet Organised Crime Threat Assessment (IOCTA) report reveals…
The Cybersecurity and Infrastructure Security Agency (CISA), in partnership with international cybersecurity authorities, announced the release of comprehensive guidance to…
CISOs understand that threat modeling helps teams identify risks early and build safer systems. But outside the security org, the…