Author: Cybernoz
The Australian Army is trialling technology that generates fake radio communications in order to mislead adversaries and protect frontline personnel….
The Federal Bureau of Investigation (FBI) has issued a critical alert regarding the escalating activities of the cyber threat actor…
The full source code of SilverRAT, a notorious remote access trojan (RAT), has been leaked online briefly appearing on GitHub…
ChatGPT has rolled out a beta feature called Deep Research Connectors, designed to integrate seamlessly with third-party applications such as…
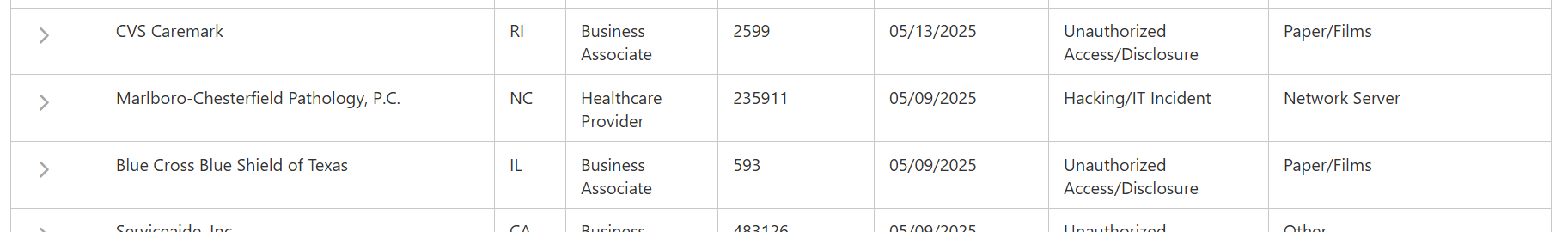
Marlboro-Chesterfield Pathology data breach impacted 235,911 individuals Pierluigi Paganini May 26, 2025 SafePay ransomware hit Marlboro-Chesterfield Pathology, stealing personal data…
A hackers has made news by allegedly selling a ZIP archive containing more than 500 compromised databases, which seems to…
ONEKEY Research Lab has uncovered a severe command injection vulnerability in the MeteoBridge firmware, a compact device designed to connect…
A Socket’s Threat Research Team has revealed a sophisticated and ongoing campaign targeting the npm ecosystem, involving 60 malicious packages…
While doing some reflecting, here are some states of being I want to achieve: Minimalism: A focus on simplicity, where…
Cisco Talos warns of active exploitation of a zero-day vulnerability (CVE-2025-0994) in Cityworks supposedly by Chinese hackers from the UAT-6382…
A decade-long cyber espionage campaign orchestrated by the advanced persistent threat (APT) group TA-ShadowCricket has been exposed through a joint…
Cybersecurity firm LayerX has uncovered over 40 malicious Chrome browser extensions, many of which are still available on the Google…