Author: Cybernoz
May 25, 2025Ravie LakshmananThreat Intelligence / Software Security Cybersecurity researchers have disclosed a malware campaign that uses fake software installers…
Silent Ransom Group targeting law firms, the FBI warns Pierluigi Paganini May 24, 2025 FBI warns Silent Ransom Group has…
A critical XSS vulnerability, CVE-2024-27443, in Zimbra Collaboration Suite’s CalendarInvite feature is actively being exploited, potentially by the Sednit hacking…
ESET Research has been tracking Danabot’s activity since 2018 as part of a global effort that resulted in a major…
SK Telecom reveals malware intrusion that remained hidden for nearly two years, led to the leaking of 26.69 million IMSI…
Leader of Qakbot cybercrime network indicted in U.S. crackdown Pierluigi Paganini May 24, 2025 The U.S. indicted Russian Rustam Gallyamov…
This week, WIRED launched our Rogues issue—which included going a bit rough ourselves. WIRED senior correspondent Andy Greenberg flew to…
China’s top cybersecurity watchdog, in coordination with financial regulators, has shut down over a dozen social media accounts for spreading…
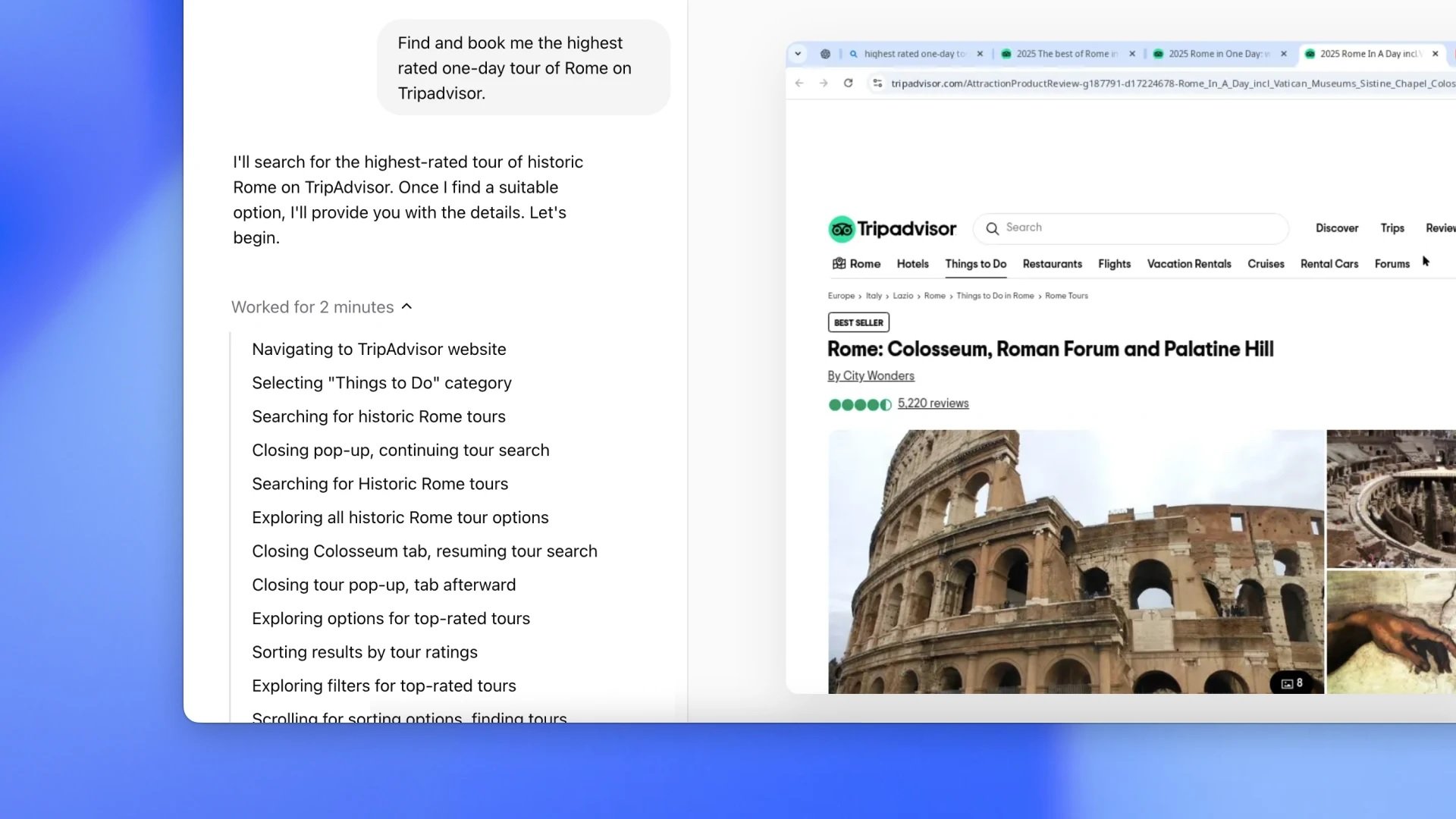
OpenAI says Operator Agent now uses the o3 model, which means it’s now significantly better at reasoning capabilities. For those…
Akamai researchers reveal a critical flaw in Windows Server 2025 dMSA feature that allows attackers to compromise any Active Directory…
Hackers are increasingly targeting macOS users with malicious clones of Ledger Live, the popular application for managing crypto assets via…
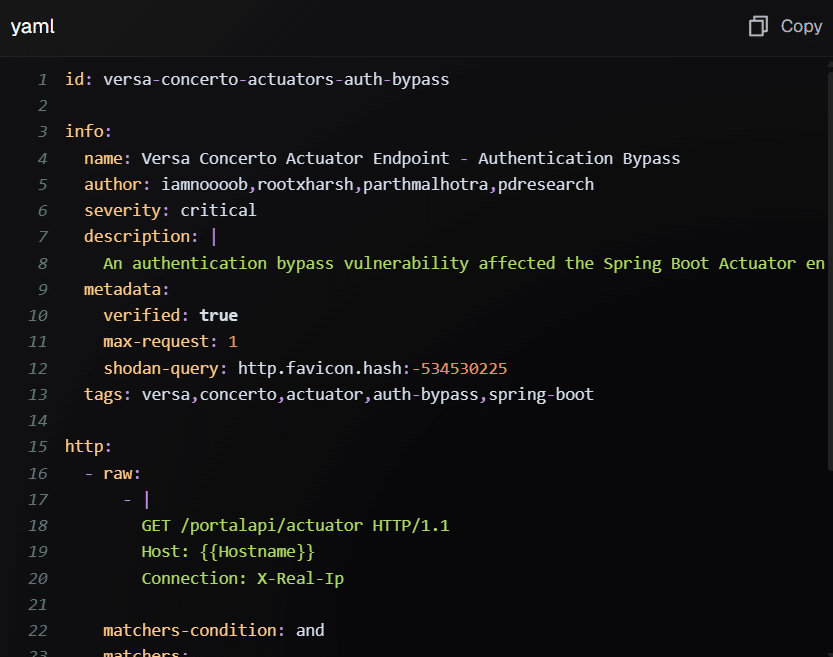
Versa Networks has patched three vulnerabilities in its Concerto network security and SD-WAN orchestration platform, including one that scored a…