Author: Cybernoz
A new report from Cofense Intelligence reveals a troubling trend in cyberattacks: criminals are increasingly hijacking legitimate Remote Access Tools…
A threat actor known as #LongNight has reportedly put up for sale remote code execution (RCE) access to Burger King…
A bipartisan pair of senators is taking another shot at legislation that would require federal government contractors to follow National…
The decentralized exchange Cetus Protocol announced that hackers have stolen $223 million in cryptocurrency and is offering a deal to…
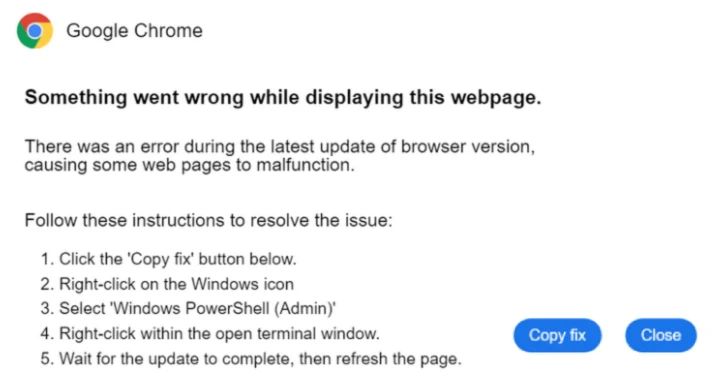
The malware known as Latrodectus has become the latest to embrace the widely-used social engineering technique called ClickFix as a…
60 packages have been discovered in the NPM index that attempt to collect sensitive host and network data and send it…
A new project has exposed a critical attack vector that exploits protocol vulnerabilities to disrupt DNS infrastructure, manipulate Non-Human Identity…
In a major international operation coordinated by Europol and Eurojust, law enforcement agencies and private sector partners have successfully dismantled…
The bustling cybercrime enterprise has been dealt a significant blow in a global operation that relied on the expertise of…
Elastic Security Labs has recently exposed a sophisticated new malware family dubbed DOUBLELOADER, observed in conjunction with the RHADAMANTHYS infostealer….
Nation-state threat actors targeting Commvault applications hosted in Microsoft Azure may be part of a broader campaign targeting Software-as-a-Service (SaaS)…
A security vulnerability was recently discovered in GitLab Duo, the AI-powered coding assistant integrated into GitLab and based on Anthropic’s…