Author: Cybernoz
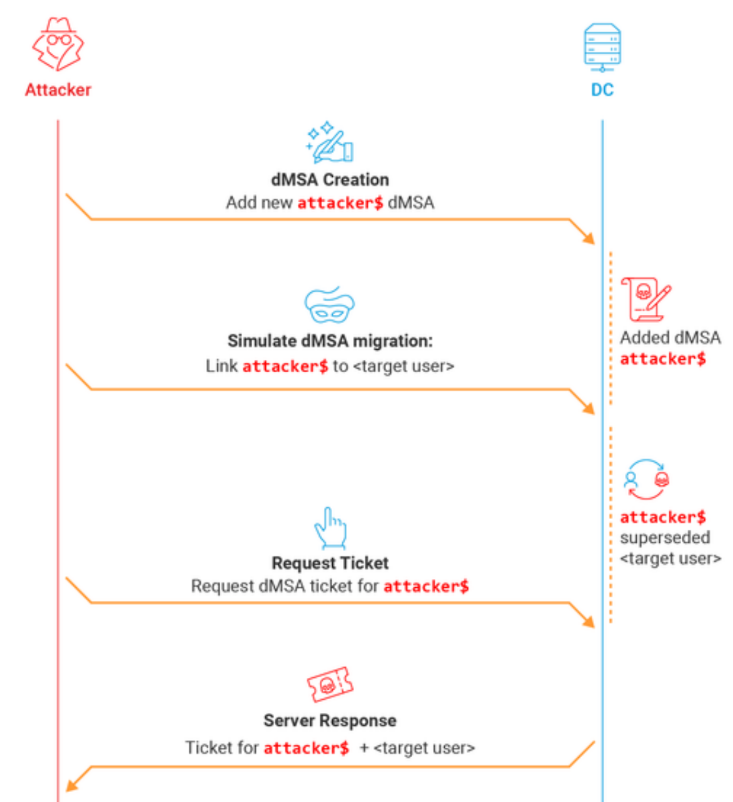
The delegated Managed Service Account (dMSA) feature was introduced in Windows Server 2025 as a secure replacement for legacy service…
When Coinbase said last week that it had refused to pay a $20 million ransom tied to an insider leak,…
Coinbase data breach impacted 69,461 individuals Pierluigi Paganini May 21, 2025 Cryptocurrency exchange Coinbase announced that the recent data breach…
The European Union has imposed strict sanctions against web-hosting provider Stark Industries and the two individuals running it, CEO Iurie…
The cybersecurity landscape reveal that the VanHelsing ransomware operation has experienced a significant security breach with its source code being…
KrebsOnSecurity, the well-known cybersecurity blog run by investigative journalist Brian Krebs, was recently hit by a massive distributed denial-of-service (DDoS)…
Black Hat USA 2025 returns to the Mandalay Bay Convention Center in Las Vegas with a 6-day program. The event will…
Developers who specialize in writing smart (primarily Ethereum) contracts using the Solidity programming language have been targeted via malicious VS…
Continuous Integration and Continuous Delivery/Deployment (CI/CD) refers to practices that automate how code is developed and released to different environments….
Vast Data has announced an agentic AI application environment – the Vast AgentEngine – for its data management stack, which…
An analysis conducted by researchers at the Norwegian University of Science and Technology Gjøvik and the Delft University of Technology…
PowerDNS has released a critical security update to address a vulnerability in its DNSdist load balancer that could allow remote…