Author: Cybernoz
The world we live in is packed with data. Texts, emails, social media posts, deleted files, you name it. And…
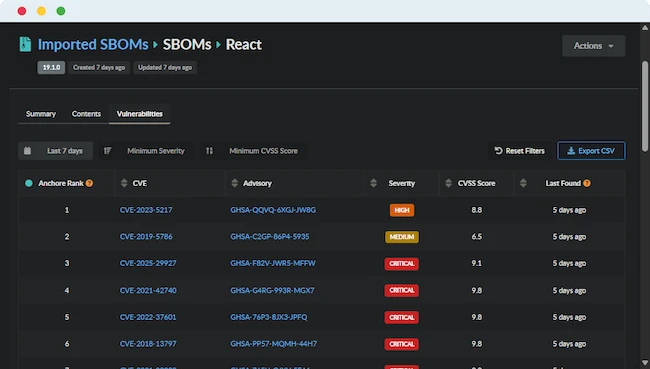
Anchore announced the next phase of its SBOM strategy with the release of Anchore SBOM. With the addition of Anchore…
May 21, 2025Ravie LakshmananMalware / Artificial Intelligence Counterfeit Facebook pages and sponsored ads on the social media platform are being…
Cybersecurity firm Wiz says threat actors are actively exploiting in the wild two recently patched Ivanti Endpoint Manager Mobile (EPMM)…
Kettering Health, a healthcare network that operates 14 medical centers in Ohio, was forced to cancel inpatient and outpatient procedures…
The Acronis Threat Research Unit (TRU) has revealed an advanced campaign believed to be orchestrated by the SideWinder advanced persistent…
Google DeepMind has developed an ongoing process to counter the continuously evolving threat from Agentic AI’s bete noir: adaptive indirect…
When the news broke that a Chinese hacking group known as Salt Typhoon had penetrated multiple U.S. telecommunications networks, gained…
Cellcom/Nsight has officially confirmed a cyberattack as the cause of a five-day service disruption affecting customers across its network. In…
It takes just one email to compromise an entire system. A single well-crafted message can bypass filters, trick employees, and…
A Massachusetts student pleaded guilty in court to hacking two US companies and extorting them for ransom. One of the…
U.S. CISA adds Ivanti EPMM, MDaemon Email Server, Srimax Output Messenger, Zimbra Collaboration, and ZKTeco BioTime flaws to its Known…