Author: Cybernoz
Apr 18, 2025Ravie LakshmananWindows Security / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a medium-severity…
Many are confused by the terms decompiler and disassembler. As with most confusion of this type, most just use the…
Rise in accessible AI tools significantly lowered the barrier to entry for cyber attackers, enabling them to create and deploy…
I learned some web server Kung Fu this weekend. I now know how to set up both Nginx and Varnish,…
I write a lot about free will, and people don’t understand why. I’ll try here again to explain. Simply, one’s stance…
So I saw Obama’s SOTU speech last night. I have been avoiding political news for the most part lately, so…
The fundamental source of poor email style is the practice of quoting the entire message you’re replying to. If that’s…
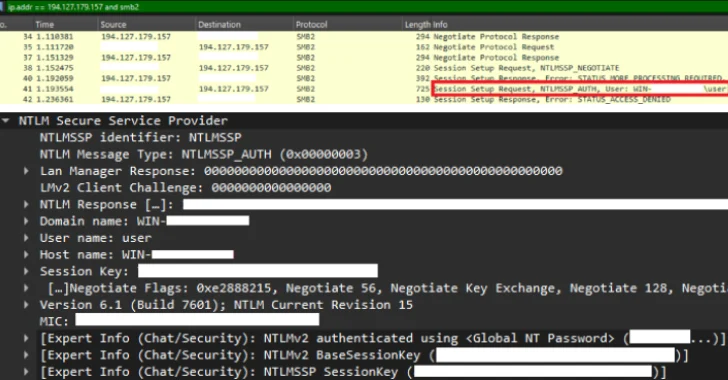
If you spent any time in the IT world you’re likely to be particularly tuned to the threat risk of…
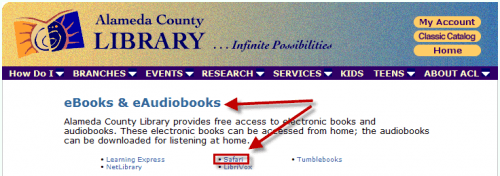
If you haven’t heard of Safari Books Online it’s basically a massive collection of the most popular technical books (over…
Google illegally dominates two markets for online advertising technology, a judge ruled, dealing another blow to the tech giant and…
Waste and irrationality. I think many among the rich would be far more willing to pay a larger portion in…
I often take criticism for my desire to own expensive things, live in nice neighborhoods, eat in quality restaurants, and…