Author: Cybernoz
Over the years, many different technologies have transitioned to Cloud-based solutions, including ERP systems and email management platforms. Phone systems…
PentestPad announced a major rollout of new features to its platform, built to transform how modern security teams deliver penetration…
May 15, 2025The Hacker NewsCompliance / Penetration Testing Imagine this: Your organization completed its annual penetration test in January, earning…
The Post Office scandal public inquiry will publish the first part of its final report this summer, with its findings…
Ransomware has evolved into a deceptive, highly coordinated and dangerously sophisticated threat capable of crippling organizations of any size. Cybercriminals…
Over the past few years, Okta has stated its commitment to ending the threat of identity-enabled cyber crime and attacks….
Police in Europe have shut down a fake online trading platform that scammed hundreds of victims out of €3 million…
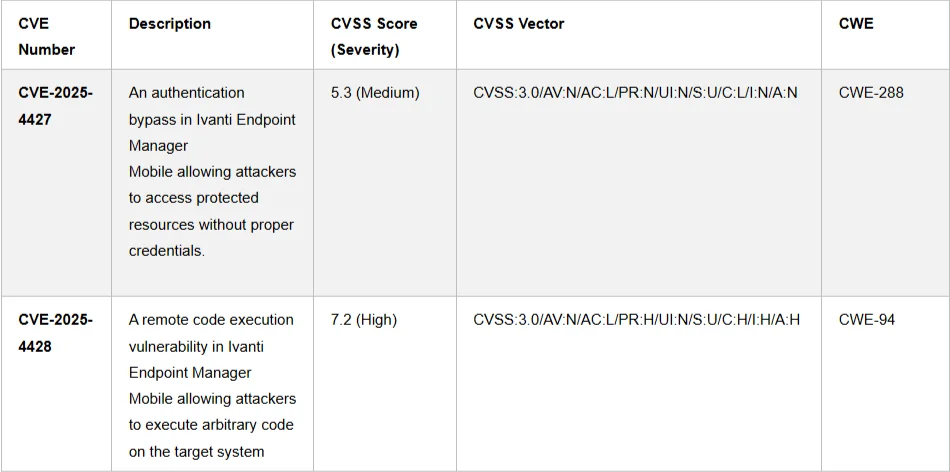
Ivanti has released security patches to address two vulnerabilities in its Endpoint Manager Mobile (EPMM) software, which were being actively…
U.S. CISA adds a Fortinet flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini May 15, 2025 U.S. Cybersecurity and Infrastructure…
How is the discipline of sports analytics evolving to deliver marginal gains to the performance of players and teams? Rugby…
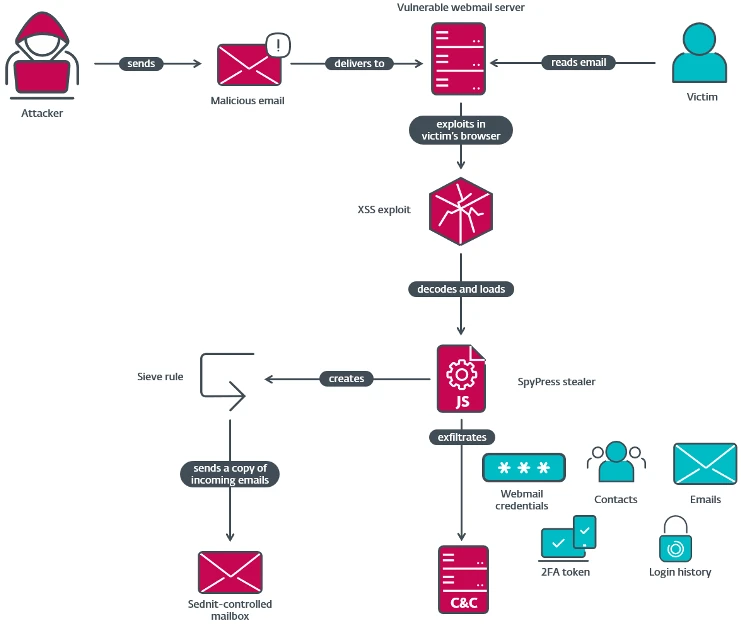
Fancy Bear, the hacking group linked to Russia’s Main Intelligence Directorate (GRU), has been targeting the email accounts of high-ranking…
ESET researchers have uncovered RoundPress, a Russia-aligned espionage operation targeting webmail servers via XSS vulnerabilities. Behind it is most likely…