Author: Cybernoz
[Part 1 of 2 – Based on an interview with Zscaler CSO Deepen Desai] By Holger Schulze, Cybersecurity Insiders The…
Researchers have discovered a very versatile ad fraud network—known as Kaleidoscope—that bombards users with unskippable ads. Normally, ad fraud is…
Google said hackers responsible for paralysing disruptions of UK retailers are turning their attention to similar companies in the United…
The state of Texas reached a mammoth financial agreement with Google last week, securing $1.375 billion in payments to settle…
Retailers in the United States are now coming under attack from Scattered Spider, the English-speaking hacking collective that is suspected…
US energy officials are reassessing the risk posed by Chinese-made devices that play a critical role in renewable energy infrastructure…
Identity theft has reached unprecedented levels in 2024, fueled by increasingly sophisticated criminal tactics that exploit technological advancements and systemic…
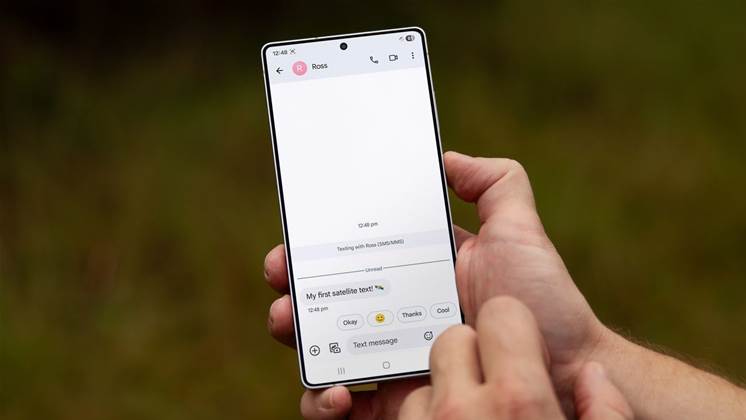
Telstra has started a live trial of satellite-to-mobile messaging in regional Australia, ahead of a commercial launch of the service…
U.S. CISA adds Microsoft Windows flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini May 14, 2025 U.S. Cybersecurity and…
Nucor Corp. on Wednesday disclosed a cyberattack involving an unauthorized third party that gained access to parts of its IT…
The Consumer Financial Protection Bureau is set to withdraw a Biden-era rule aimed at cracking down on data brokers and…
Google is rolling out a change to Chromium that “de-elevates” Google Chrome so it does not run as an administrator…