Author: Cybernoz
A recent wave of malicious NPM packages has emerged as a significant threat to cryptocurrency users, specifically targeting Ethereum wallet…
Jun 03, 2025Ravie LakshmananMobile Security / Malware A growing number of malicious campaigns have leveraged a recently discovered Android banking…
Google on Monday released a fresh Chrome 137 update to address three vulnerabilities, including a high-severity bug exploited in the…
Google fixed the second actively exploited Chrome zero-day since the start of the year Pierluigi Paganini June 03, 2025 Google…
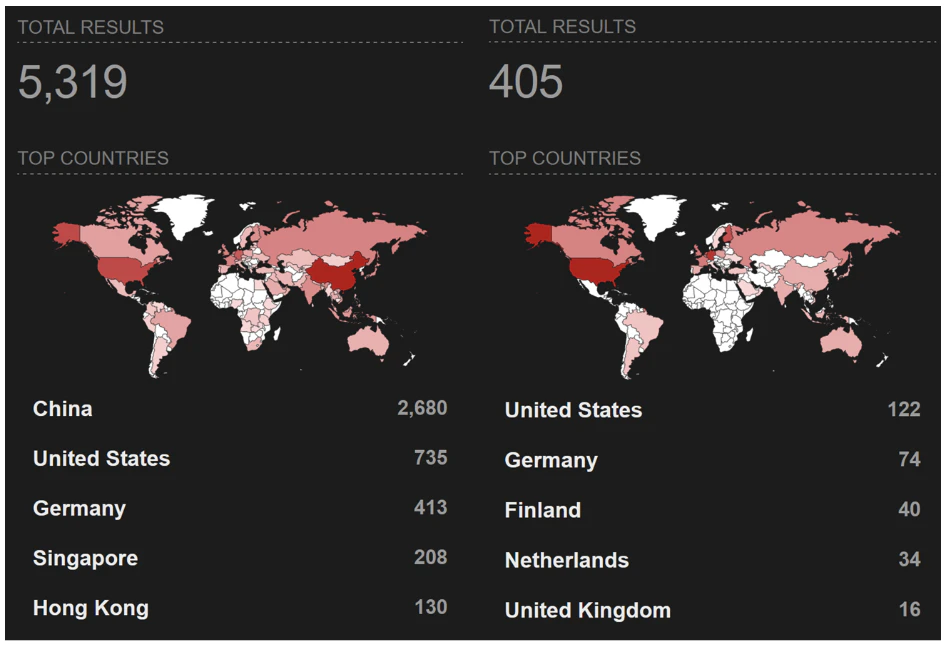
A recent post on an underground forum has brought renewed attention to the escalating arms race between cybercriminals and anti-bot…
Interactive Brokers is warning customers to be on high alert due to a wave of scams involving fraudsters posing as…
Jun 03, 2025Ravie LakshmananThreat Intelligence / Cyber Threats Microsoft and CrowdStrike have announced that they are teaming up to align…
The National Grid has confirmed that it is in the process of building its largest new electrical substation in response…
Microsoft and CrowdStrike announced on Monday that they are leading an industry effort to map threat actor naming, with the…
Jun 03, 2025Ravie LakshmananWeb Security / Digital Identity Google has revealed that it will no longer trust digital certificates issued…
Cryptojacking campaign relies on DevOps tools Pierluigi Paganini June 03, 2025 A cryptojacking campaign is targeting exposed DevOps servers like…
Multiple security vulnerabilities in Hewlett-Packard Enterprise (HPE) StoreOnce software platform that could allow remote attackers to execute malicious code, bypass…