Author: Cybernoz
According to recent industry analysis, cybersecurity professionals are overwhelmed by a flood of security alerts. Organizations process an average of…
The United States’ Cybersecurity and Infrastructure Security Agency (CISA), is likely to have its funding cut by approximately $495m and…
Orica will go live with a new payroll and workforce management system in Australia in July, the “biggest and most…
Multiple critical security vulnerabilities affecting MediaTek smartphones, tablets, and IoT chipsets could allow attackers to escalate privileges and compromise device…
Open source AI is gaining momentum across major players. DeepSeek recently announced plans to share parts of its model architecture…
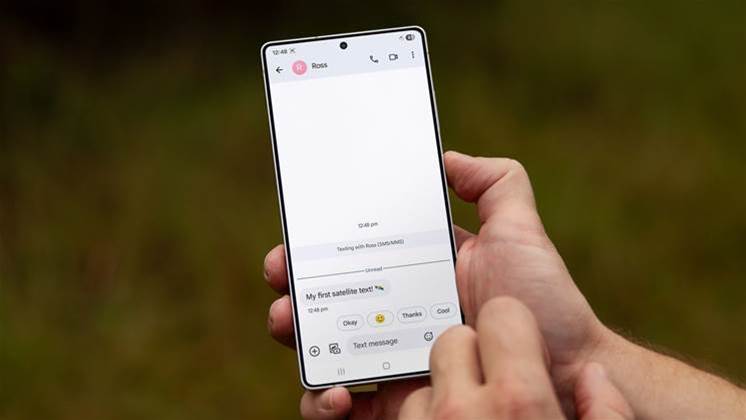
Telstra has commercially launched Starlink-backed satellite-to-mobile messaging just weeks after live trials, albeit initially only for Samsung Galaxy S25 series…
Significant vulnerabilities were uncovered in pre-installed applications on Ulefone and Krüger&Matz Android smartphones that expose users to significant risks, including…
Cybersecurity researchers have identified a sophisticated malware campaign utilizing deceptive CAPTCHA interfaces to distribute EddieStealer, a Rust-based information stealing malware…
Litecoin (LTC), often called the “silver to Bitcoin’s gold,” has long been popular for its speed, lower transaction fees, and…
Modern organizations face a growing challenge in protecting sensitive data. As more people adopt the cloud and rules get tougher,…
Advanced threat actors have developed sophisticated stealth syscall execution techniques that successfully bypass modern security infrastructure, including Event Tracing for…
Qualys details CVE-2025-5054 and CVE-2025-4598, critical vulnerabilities affecting Linux crash reporting tools like Apport and systemd-coredump. Learn how to protect…