Author: Cybernoz
According to Verizon’s 2024 Data Breach Investigations Report, 80% of breaches stem from compromised credentials. While passwords were meant to…
Multiple vulnerabilities in Microsoft’s Copilot AI for SharePoint, enabling attackers to access sensitive corporate data including passwords, API keys, and…
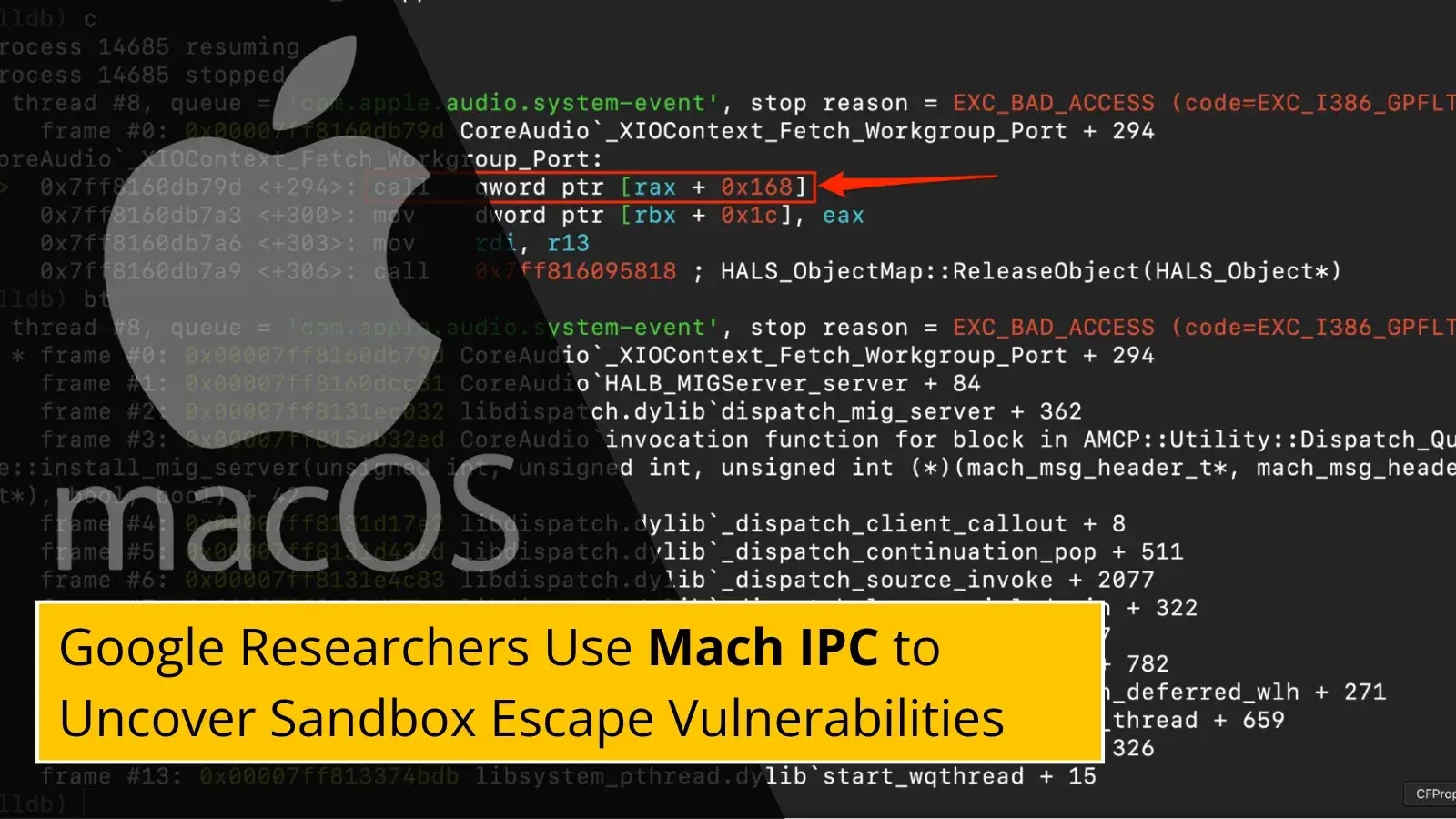
Google Project Zero researchers have uncovered new sandbox escape vulnerabilities in macOS using an innovative approach that leverages Mach Interprocess…
May 12, 2025Ravie LakshmananMalware / Artificial Intelligence Threat actors have been observed leveraging fake artificial intelligence (AI)-powered tools as a…
A critical security flaw has been discovered in the Linux kernel’s nftables subsystem, which is responsible for packet filtering in…
A critical Proof-of-Concept (PoC) exploit has been released for a significant vulnerability in the Linux kernel’s nftables subsystem, tracked as…
A chilling new ransomware attack method has emerged, with hackers exploiting innocuous JPEG image files to deliver fully undetectable (FUD) ransomware,…
Cybersecurity experts have identified a sophisticated phishing technique that exploits blob URIs (Uniform Resource Identifiers) to evade detection by Secure…
Microsoft has announced the upcoming release of a groundbreaking “Prevent Screen Capture” feature for Teams, designed to block unauthorized screenshots…
The Bluetooth Special Interest Group has released Bluetooth 6.1, and one of the most important new features is an update…
Texas Attorney General Ken Paxton has reached a $1.375 billion settlement with tech giant Google, marking the largest amount ever…
German police seized eXch crypto exchange Pierluigi Paganini May 12, 2025 Germany’s BKA shut down eXch crypto exchange, seizing its…