Author: Cybernoz
In a surprising twist, DragonForce Ransomware, the group responsible for a recent attack on UK retailer Marks & Spencer, has…
In this Help Net Security interview, Dr. Peter Garraghan, CEO of Mindgard, discusses their research around vulnerabilities in the guardrails…
Prime Minister Anthony Albanese has unveiled the communications, cyber security and digital economy ministers for his returning government. The new…
Defendnot, a sophisticated new tool that effectively disables Windows Defender by exploiting the Windows Security Center (WSC) API to register…
A novel exploit method leveraging Beacon Object Files (BOFs) has emerged, enabling attackers to extract Microsoft Entra (formerly Azure AD)…
In this digital age, photos have become one of the most shared and stored types of content online. Whether it’s…
Most people think great presenters are born with natural talent. Luka Krejci, a presentation expert, disagrees. “They are called presentation…
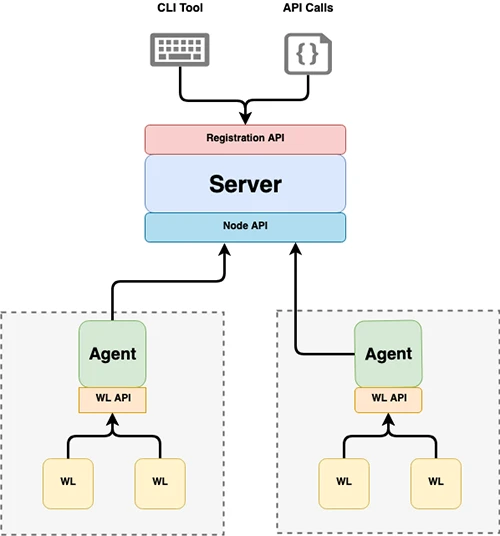
SPIRE is a graduated project of the Cloud Native Computing Foundation (CNCF). It’s a production-ready implementation of the SPIFFE APIs…
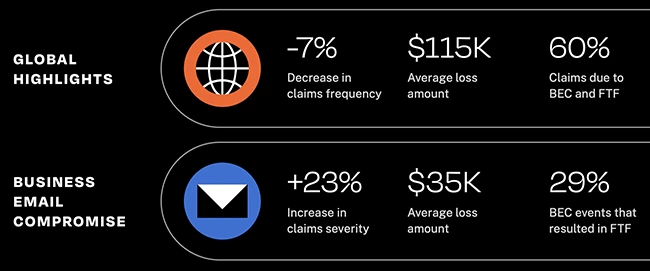
Ransomware claims stabilized in 2024 despite remaining the most costly and disruptive type of cyberattack, according to Coalition. 60% of…
Telstra InfraCo will be led by Microsoft’s managing director for Australia and New Zealand Steven Worrall from the end of…
A simulation of a dead man created by artificial intelligence addressed his killer in an Arizona court this month, in…
CSIRO is uplifting cyber security across its enterprise and research functions with an emphasis on protecting core systems, tightening access…