Author: Cybernoz
Digital Nation is proudly hosting its first-ever Digital Nation Awards event, celebrating outstanding achievements in digital transformation, from groundbreaking tech…
Google addressed 47 vulnerabilities affecting Android devices in its May security update, including an actively exploited software defect that was…
The messaging app used by at least one top Trump administration official has suspended its services following reports of hackers…
TM SGNL, a chat app by US-Israeli firm TeleMessage used by Trump officials, halts operations after a breach exposed messages…
Over 14,000 Queensland public service workers have adopted the state government’s generative AI tool, QChat, nearly a year after it…
The Darcula phishing-as-a-service (PhaaS) platform stole 884,000 credit cards from 13 million clicks on malicious links sent via text messages…
Transport for NSW is expanding its SAP Ariba service to improve supplier vetting in its procurement activities. The transport department…
Dive Brief: The Department of Defense is streamlining its software-procurement approval process. The Pentagon on Monday announced that its “Software…
A new “Bring Your Own Installer” EDR bypass technique is exploited in attacks to bypass SentinelOne’s tamper protection feature, allowing threat…
Why Application Security is Non-Negotiable The resilience of your digital infrastructure directly impacts your ability to scale. And yet, application…
Microsoft warns about the security risks posed by default configurations in Kubernetes deployments, particularly those using out-of-the-box Helm charts, which…
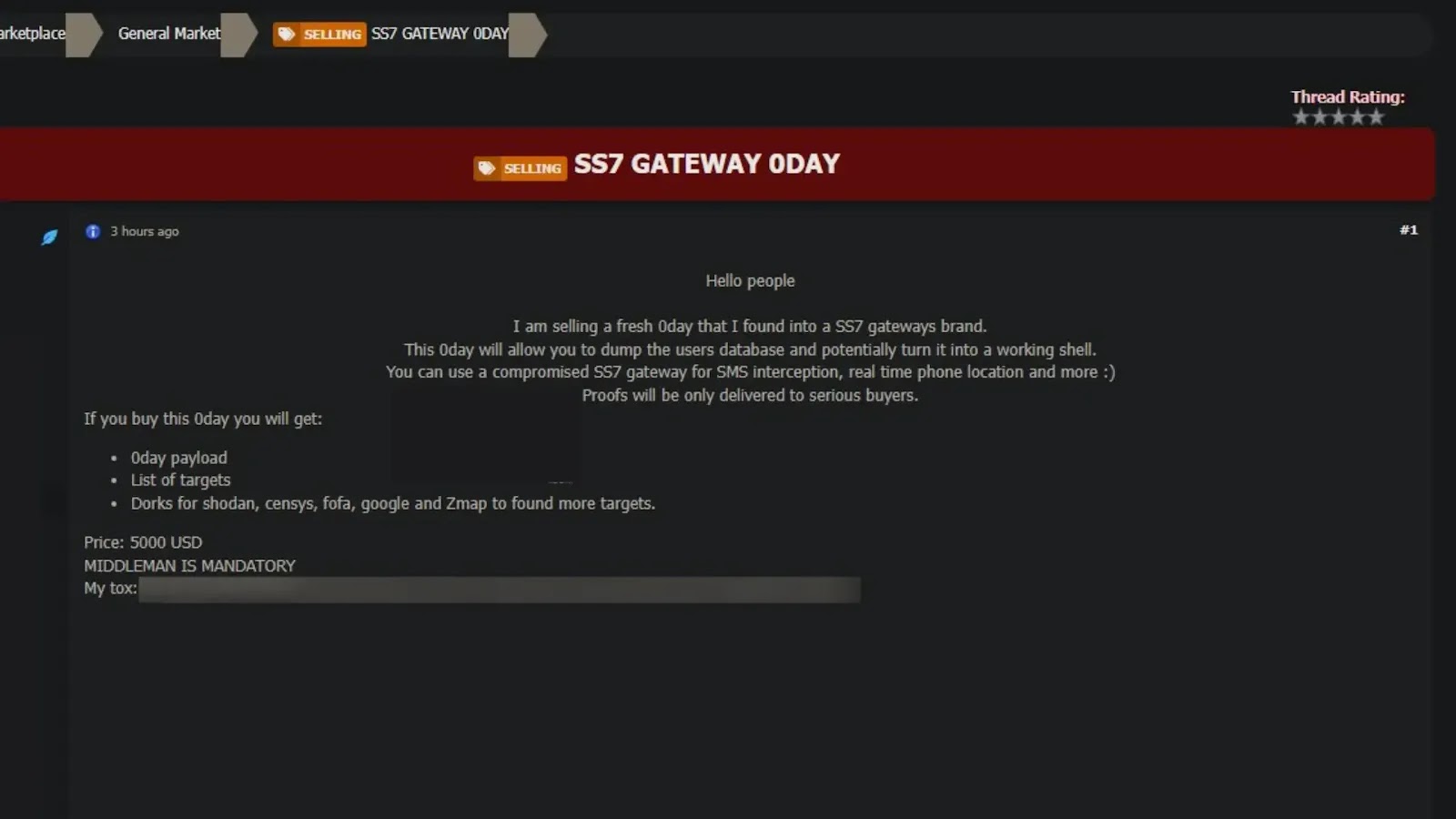
A newly discovered dark web listing claims to sell a critical SS7 protocol exploit for $5,000, raising alarms about global…