Author: Cybernoz
SAN FRANCISCO — North Korean nationals have infiltrated the employee ranks at top global companies more so than previously thought,…
A 23-year-old Scottish man thought to be a member of the prolific Scattered Spider cybercrime group was extradited last week…
US President Donald Trump said that Raytheon Technologies and IBM may get the contract to modernise the US air traffic…
ANZ Plus, ANZ’s digital bank, will introduce two passwordless authentication methods for its web banking from mid-2025. The bank said…
Tariff hikes will drive up prices and make it harder for telecommunications providers to replace networks more vulnerable to Chinese…
A new malware campaign targeting WordPress sites employs a malicious plugin disguised as a security tool to trick users into…
ESET researchers have uncovered sophisticated attack techniques employed by a China-aligned threat actor dubbed “TheWizards,” which has been actively targeting…
Lake Macquarie City Council has promoted its acting chief information officer, Joshua Crooks, to the permanent leadership position of chief…
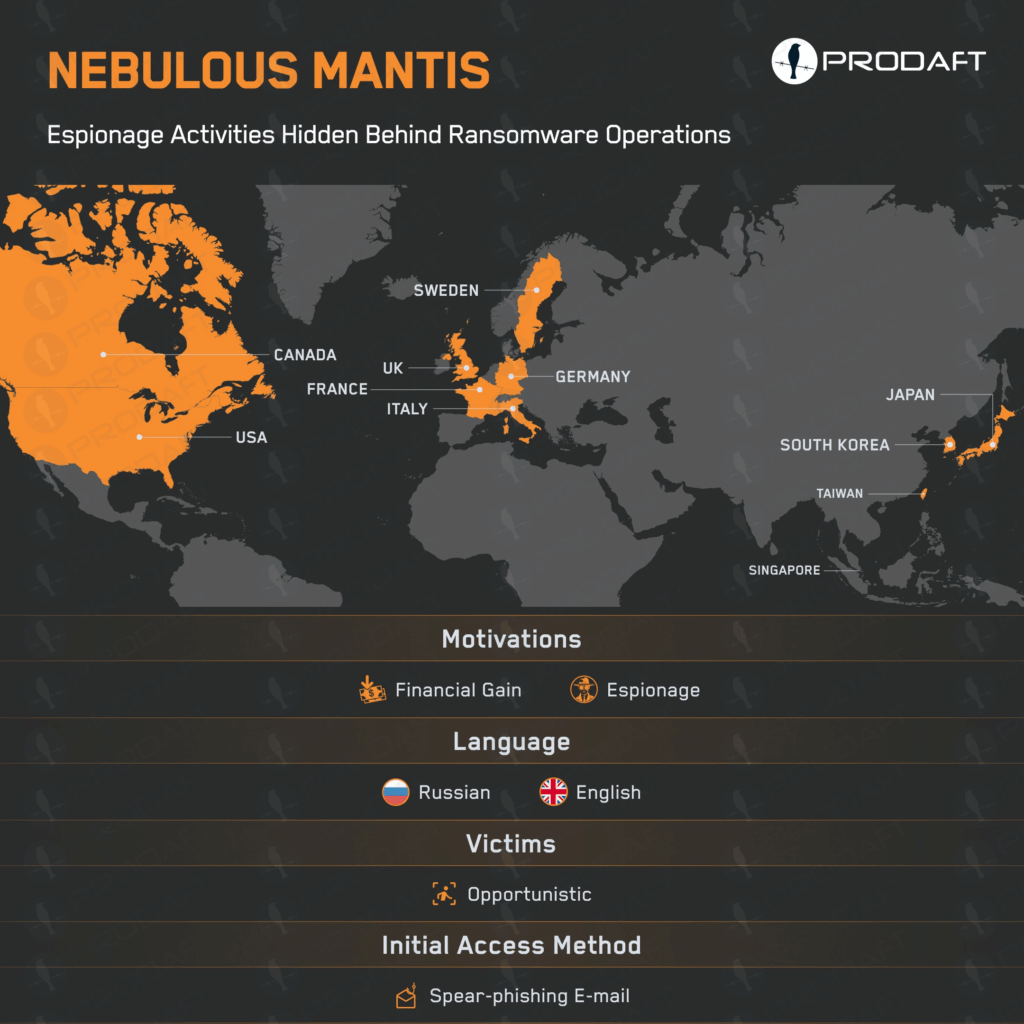
Russia-linked group Nebulous Mantis targets NATO-related defense organizations Pierluigi Paganini April 30, 2025 PRODAFT researchers warn of Russia-linked APT group…
SAN FRANCISCO – In her appearance at the RSAC 2025 Conference, Homeland Security Secretary Kristi Noem spoke about getting CISA…
The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) has become a fundamental reference for organizations aiming to…
US and Greek arrests expose 764 network’s global child abuse ring. Leaders face life for orchestrating violent exploitation through encrypted…