Author: Cybernoz
SentinelOne warns of threat actors targeting its systems and high-value clients Pierluigi Paganini April 29, 2025 SentinelOne warns China-linked APT…
Threat actors are intensifying internet-wide scanning for Git configuration files that can reveal sensitive secrets and authentication tokens used to…
A critical vulnerability in Google Chrome has recently been discovered that allows malicious actors to break out of the browser’s…
A sophisticated cyberattack targeted senior members of the World Uyghur Congress (WUC), the largest Uyghur diaspora organization, using a weaponized…
Who has the best cybersecurity name at the RSA Conference in San Francisco this year? It depends on who you…
SAN FRANCISCO — Threat intelligence flowing from private companies to cybersecurity authorities and law enforcement agencies is critical to the…
A critical vulnerability in Apple’s AirPlay protocol, dubbed AirBorne, has exposed over 2.35 billion active Apple devices and tens of…
Cybersecurity researchers at Hunt have uncovered a server hosting advanced malicious tools, including SuperShell command-and-control (C2) payloads and a Linux…
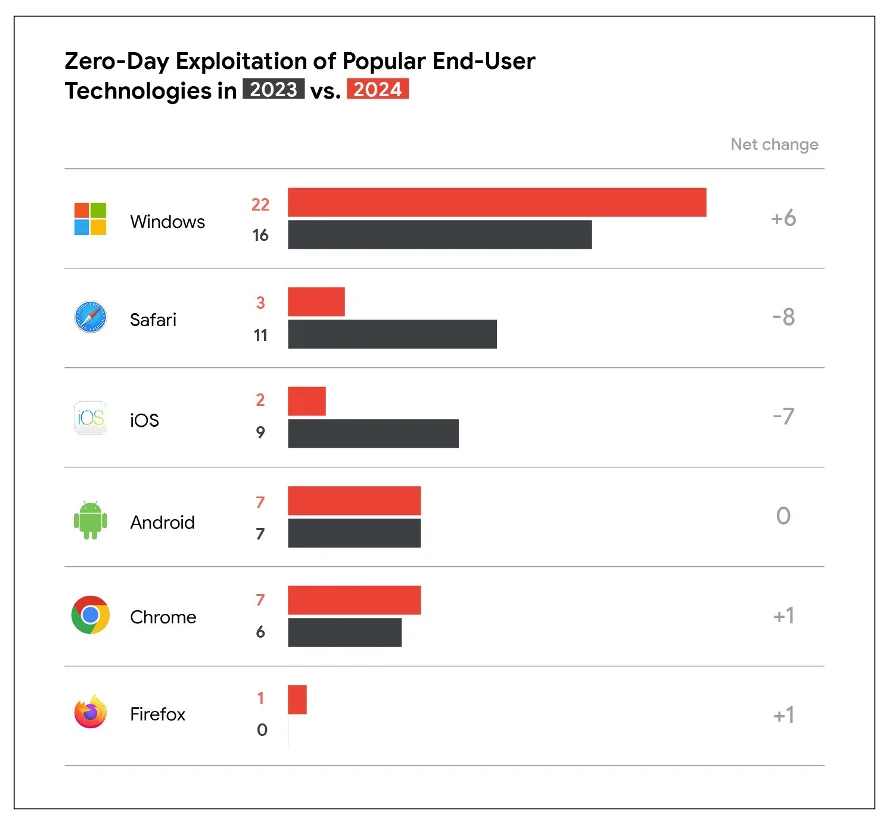
In 2024, threat actors exploited 75 zero-days – i.e., vulnerabilities previously unknown to vendors, thus without a readily available patch…
Various generative artificial intelligence (GenAI) services have been found vulnerable to two types of jailbreak attacks that make it possible…
A set of security vulnerabilities in Apple’s AirPlay Protocol and AirPlay Software Development Kit (SDK) exposed unpatched third-party and Apple…
CISA officially added a significant security flaw affecting Broadcom’s Brocade Fabric OS to its authoritative Known Exploited Vulnerabilities (KEV) Catalog,…