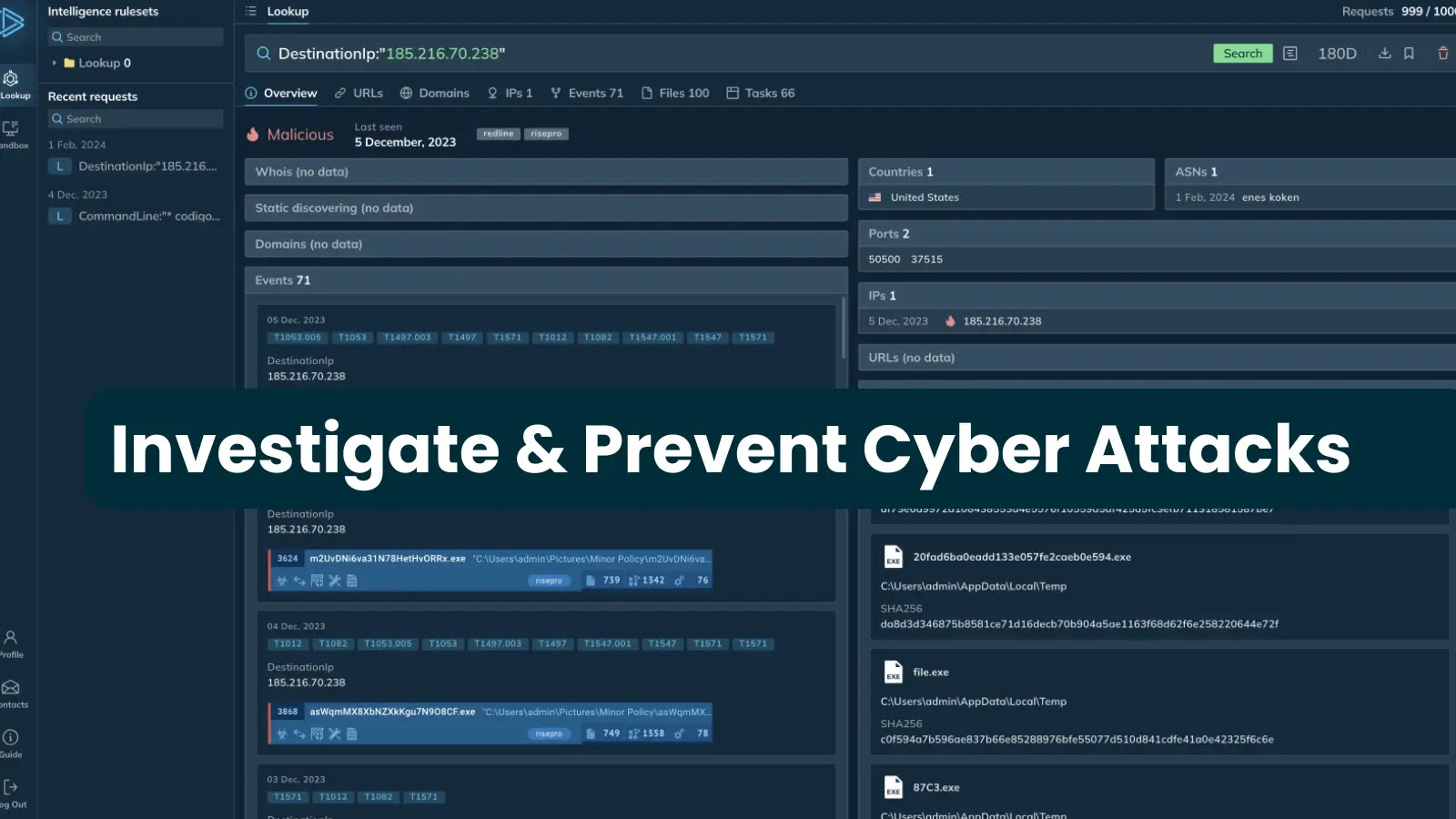
Author: Cybernoz
Microsoft has confirmed several issues affecting Microsoft 365 customers using the “paste special’ option and the calendar feature in the classic…
According to IBM Security annual research, “Cost of a Data Breach Report 2024”, an average cost of a data breach…
The House passed a bill Monday evening that would criminalize using a person’s likeness to create nonconsensual deepfake pornography. The…
Google’s Threat Intelligence Group (GTIG) says attackers exploited 75 zero-day vulnerabilities in the wild last year, over 50% of which…
Cybercriminals are leveraging automation across the entire attack chain, drastically reducing the time from reconnaissance to compromise. The data shows…
AI is expanding a $2 trillion total addressable market (TAM) for cybersecurity providers, according to a 2024/2025 study by McKinsey,…
A former Disney employee, Michael Scheuer, will serve three years in prison for computer fraud and aggravated identity theft after…
Cybersecurity company SentinelOne has revealed that a China-nexus threat cluster dubbed PurpleHaze conducted reconnaissance attempts against its infrastructure and some…
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) is warning of Broadcom Brocade Fabric OS, Commvault web servers, and Qualitia…
A severe vulnerability, identified as CVE-2025-2783, has been discovered in Google Chrome, specifically targeting the Mojo inter-process communication (IPC) component…
According to the Center for Strategic & International Studies’ (CSIS) 2025 Space Threat Assessment, space systems’ susceptibility to cyberattacks has…
The Cybersecurity and Infrastructure Security Agency (CISA) has added three new flaws to its Known Exploited Vulnerabilities catalog on Monday,…